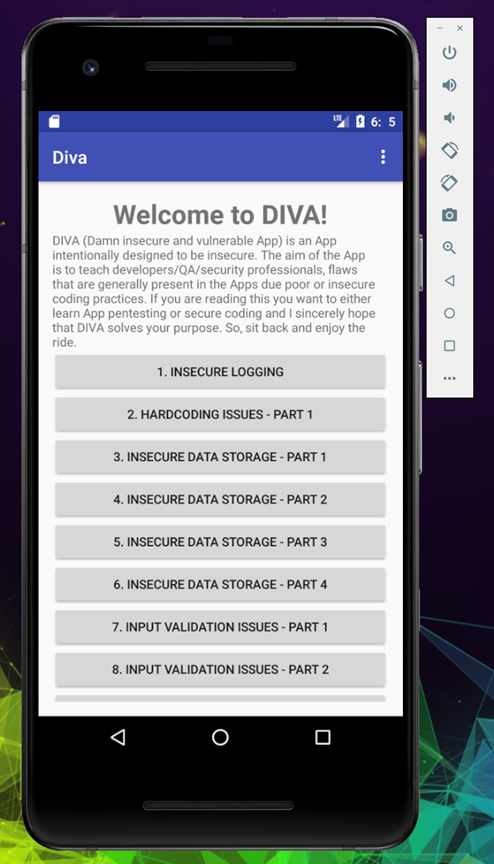
The first challange in DIVA is Insecure Logging
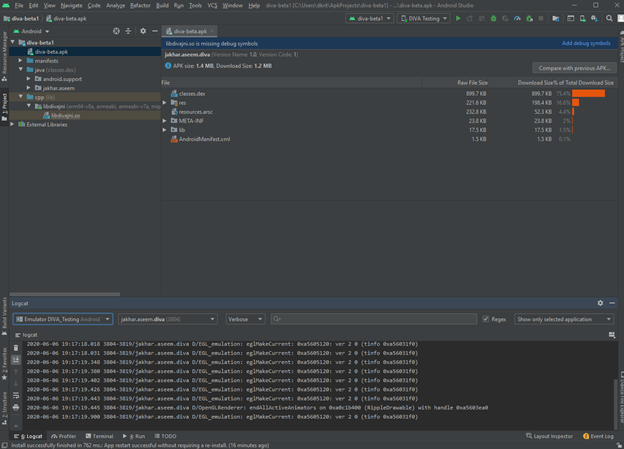
Now to analyze our logs we will open logcat on the android studio
If we open this we can see the logs the application is feeding with its stack trace when it generates any errors.
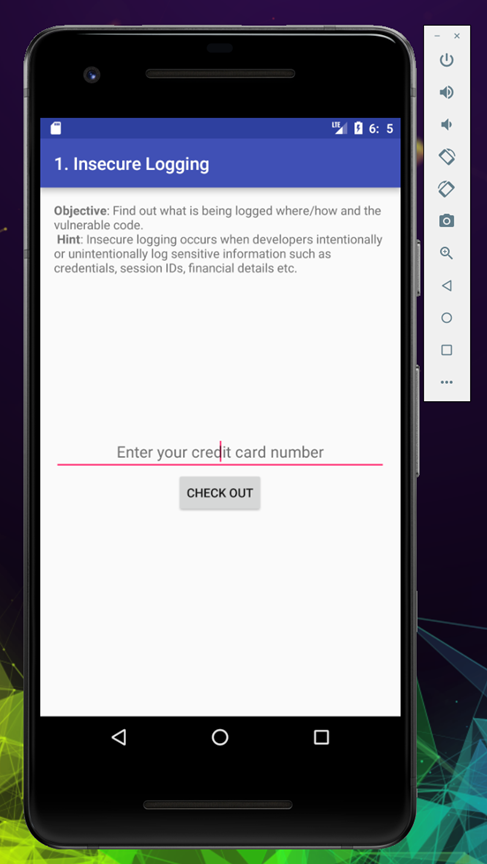
Let’s feed the application with any random number to create an error
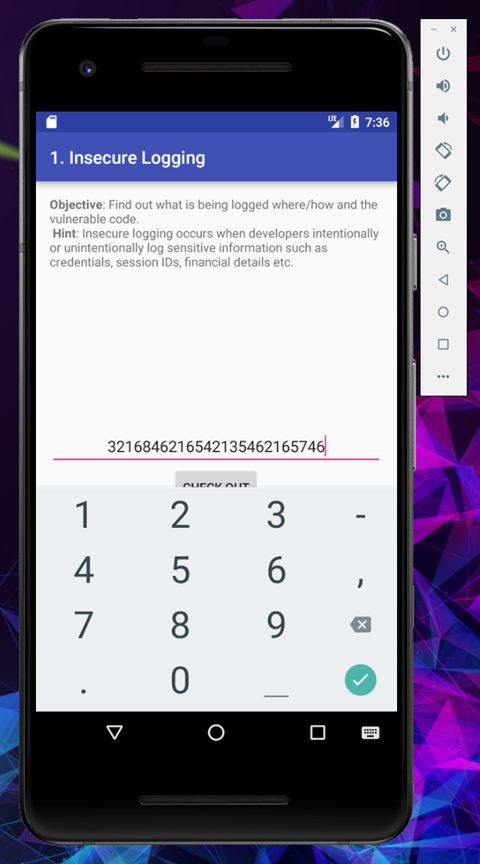
And click on checkout
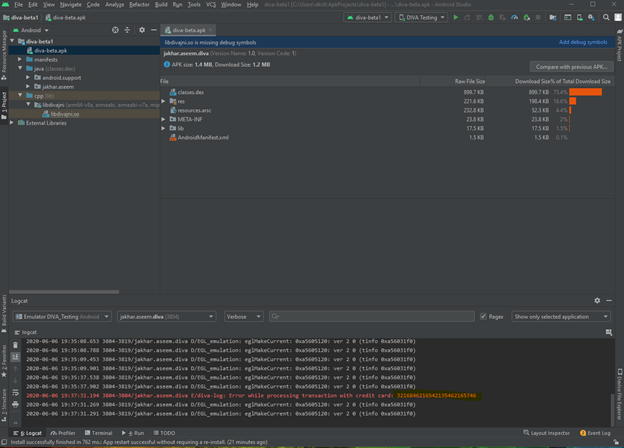
As you can see the credit card number which we feed in the application is visible in logcat which is considered as an Insecure Logging vulnerability.
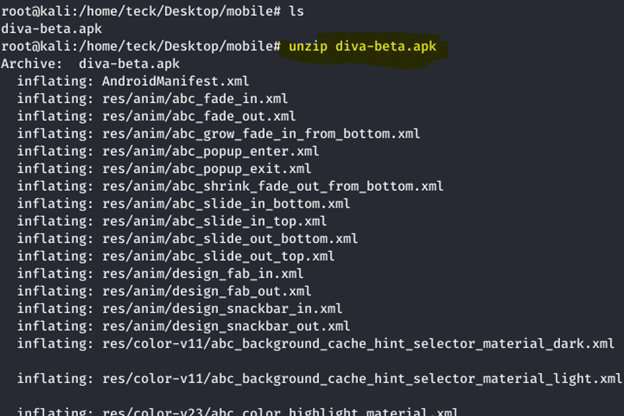
Let’s decomplie/unpack the APK to analyz the code which cause this vulnerbality in the application.
Unzip the apk file
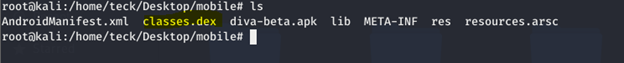
Classes.dex this is what we need
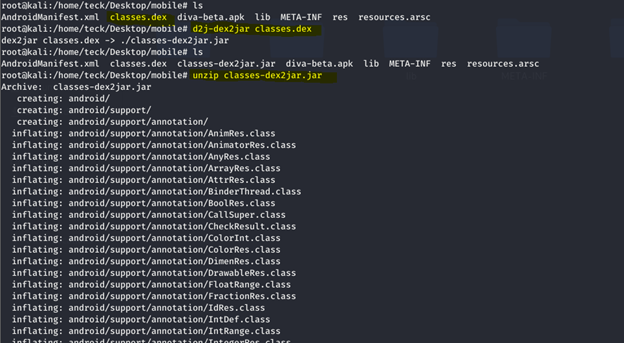
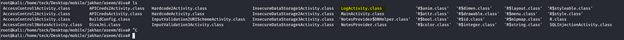
Inside ./jakhar/aseem/diva we can find the file LogActivity.class which have vulnerable code which we are looking for
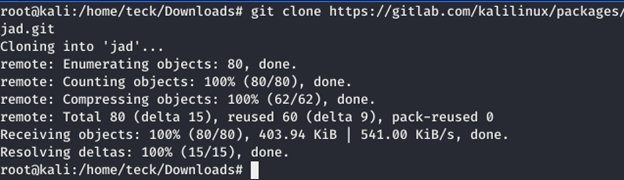
Again we need to breakdown the file into normal readable text but this time we will use a different toll (jad)
I guess in new kali 2020 they removed the jad from the repo
You can download it from gitlab-jad
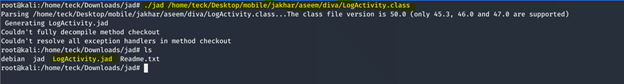
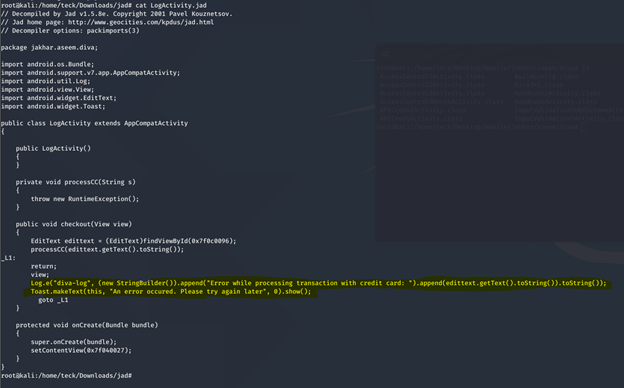
As you can see this is the piece of code which logs the data of credit card no. from the application in Logcat.
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
Log.e(“diva-log”, (new StringBuilder()).append(“Error while processing transaction with credit card: “).append(edittext.getText().toString()).toString());
Toast.makeText(this, “An error occured. Please try again later”, 0).show();
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments