Next few challenges are all about insecure data storage, so let’s go
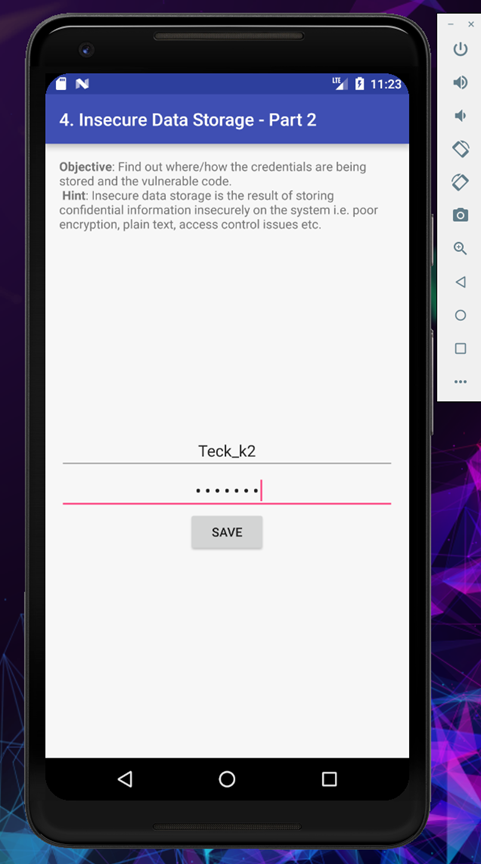
I put the credential as [Teck_k2:Teck_k2] and save
Before we proceed further, we will check the code which allow this insecure data storage vulnerability to happen.
Let’ back again to our kali
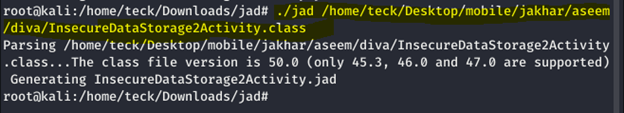
Extract the file content, and analyze
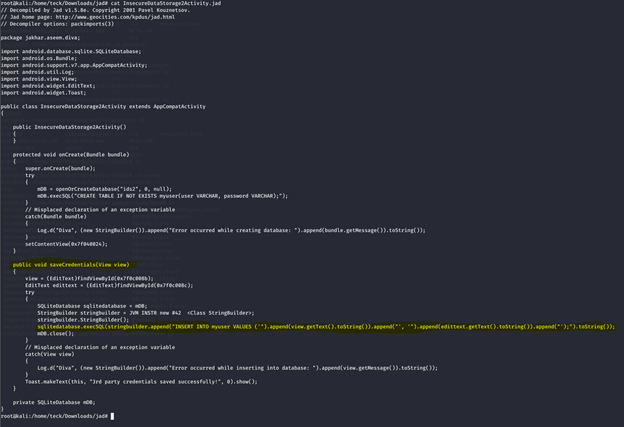
As you can see this piece of code inserting the credential into sql database inside the device, Now let’s come back to our adb shell and extract the database file
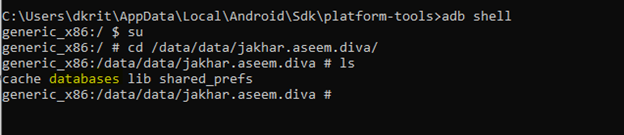
As you can see the databases folder is available, let’s go inside the folder and see all the available files
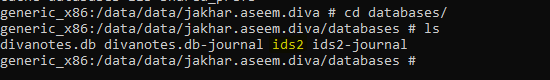
Generally we need to analyze all file one by one, but as this is a specific challenge based scenario, we won’t waste much time in analyzing all the files
For this challenge specifically we just need (ids2), we will extract this file in our local machine, for that we need to run adb as root first and then extract or it will show you permission error or file not found.
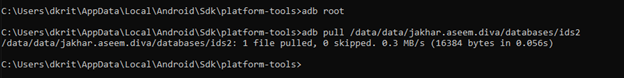
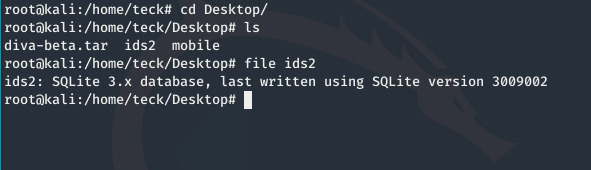
Move the file in your kali and open it with slqlite3
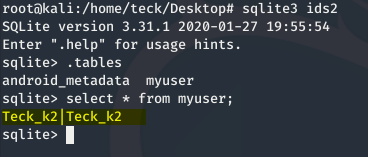
As you can see the clear text credentials are saved inside the sql database locally inside the device.
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments