Next challange in the list is Insecure Data Storge.
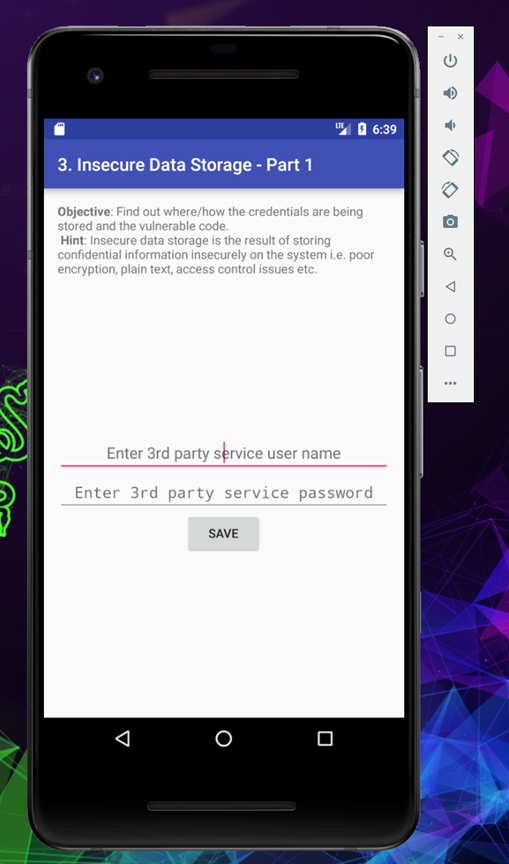
In this challenge we will try to understand how an application store a sensitive information inside the device in plain text or with weak encryption, which could later lead to data information leakage.
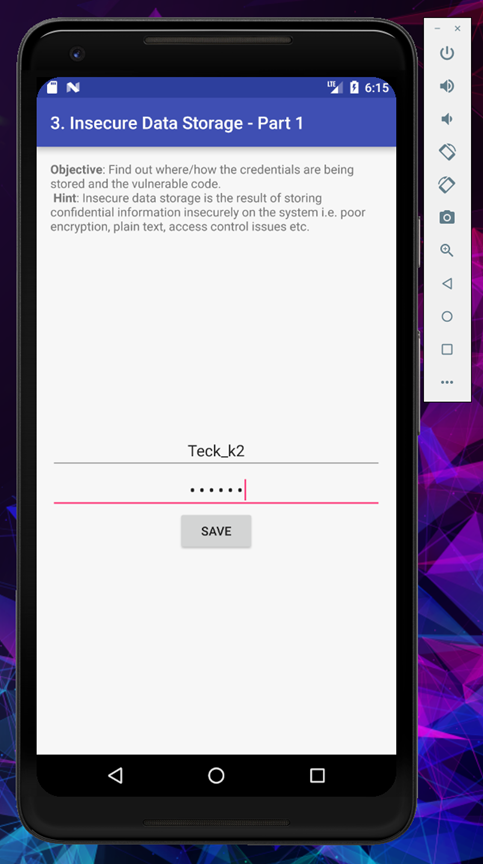
In the password section I put (111222) or any random password you wish to save and click on save.
Now for our next step we need to read some internal files and for that we would require root permission
Now connect to android device with adb shell
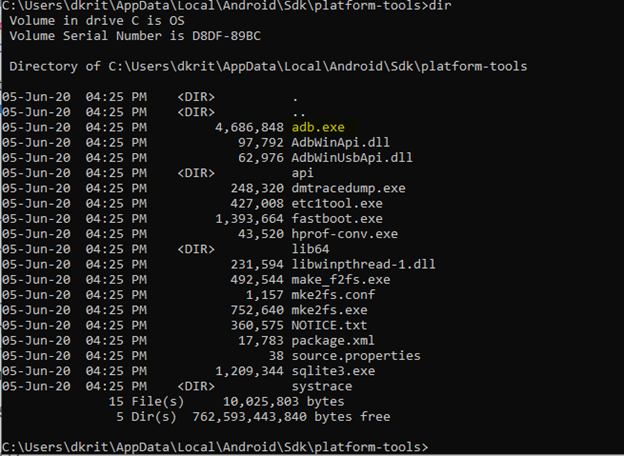
Check for connect devices
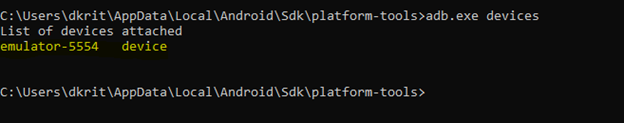
As we can see our device is connect we are good to go
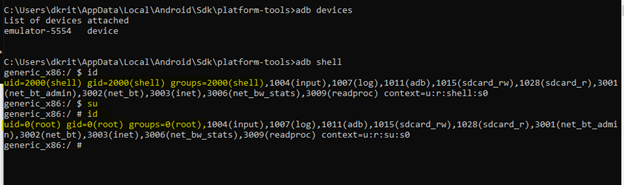
We have the root shell now, we can read the internal file without restriction now
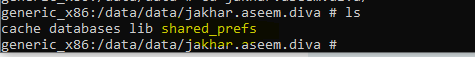
As you can see there is a (shared_prefs) folder which means the application is storing these details using shared preferences
If you analyze the source code you will get the clear understanding
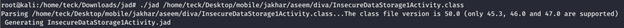
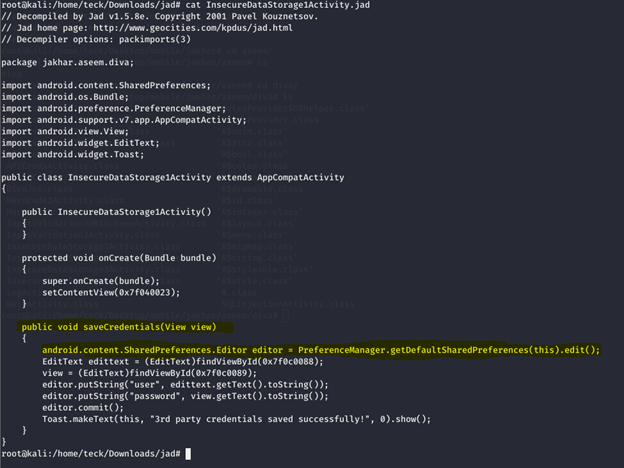
Now get back to adb shell
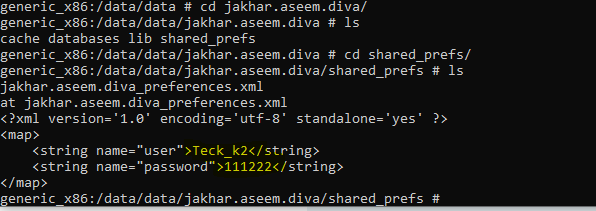
As you cans see the credentials are being saved in plain text inside the device.
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments