We reached to our final challenge in this the objective is to do DOS the application and crash it
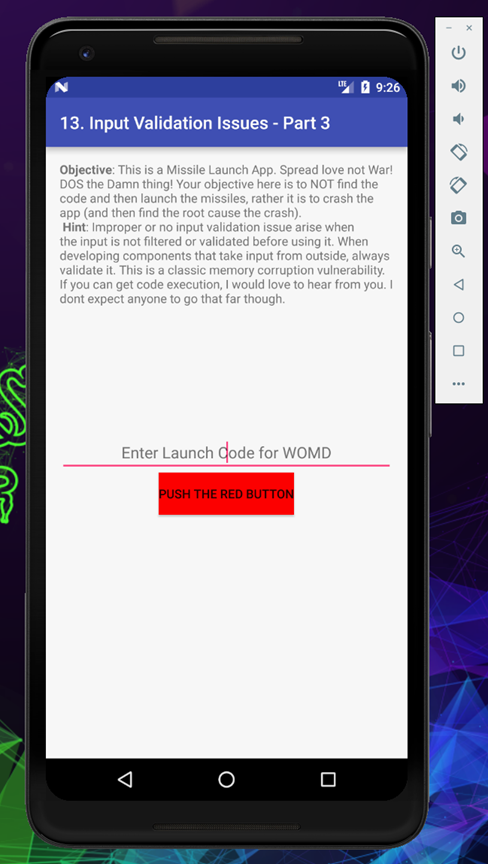
As the hint mention that this is a classic example of memory corruption or stack based buffer overflow
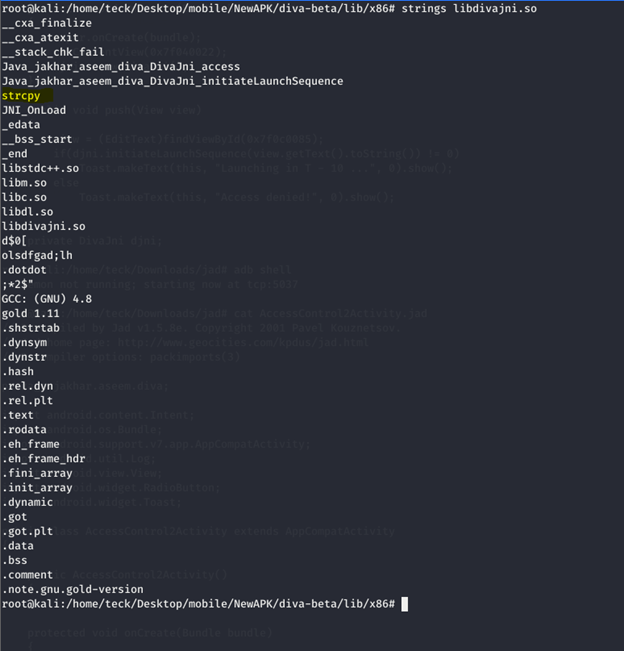
As you can see there is strcpy function available in the library of the application, so let’s try with something simple to understand where we are
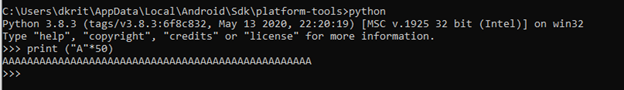
Generate a string of A’s and feed it inside the application to see the response in Logcat
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
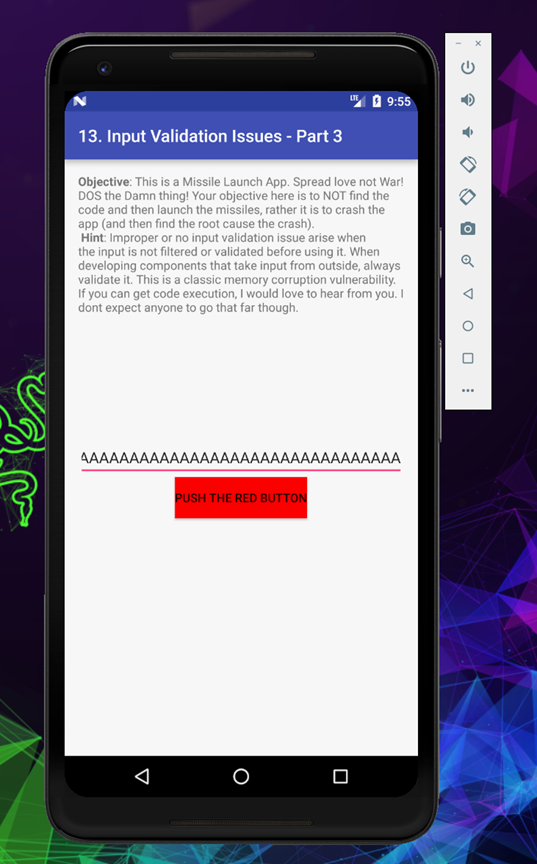
Now push the red button
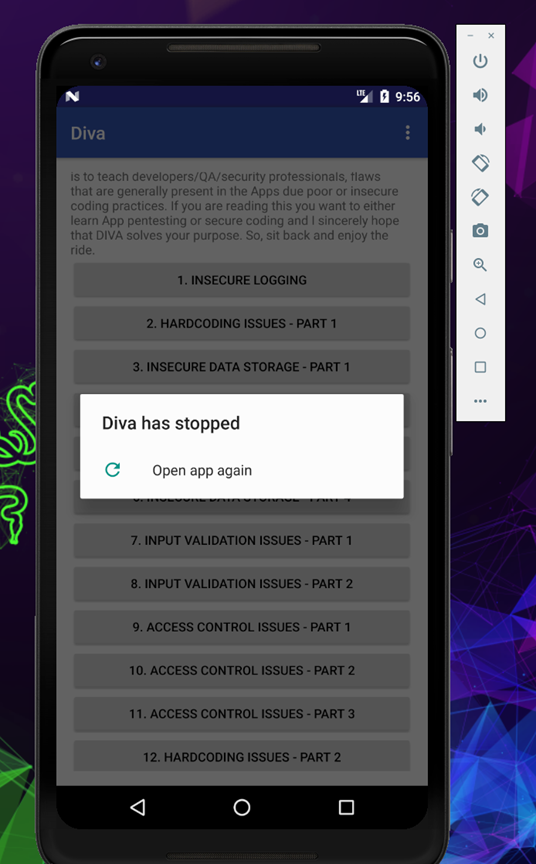
And you will notice the application crashed successfully, basically the challenge finished at this stage, but I decided to go ahead and take a reverse shell, which turn out to be the worst decision for me 😂, as expected Android binary exploitation should be similar what we expirience in a normal linux machine, untill unless you are using a ARM based architecture which is slightly different, but that was my mistake to think like that, becasue the application was coustom build and have lot of restriction which I had never experienced, and later as usual my mentor KNX came to rescue me from this hell 😂. I have shared my overall experience in the next Blog Binary from Hell 😈
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments