In this challenge we will solve and learn how we can view sensitive data inside the device, from the application which was meant to view only web URLs
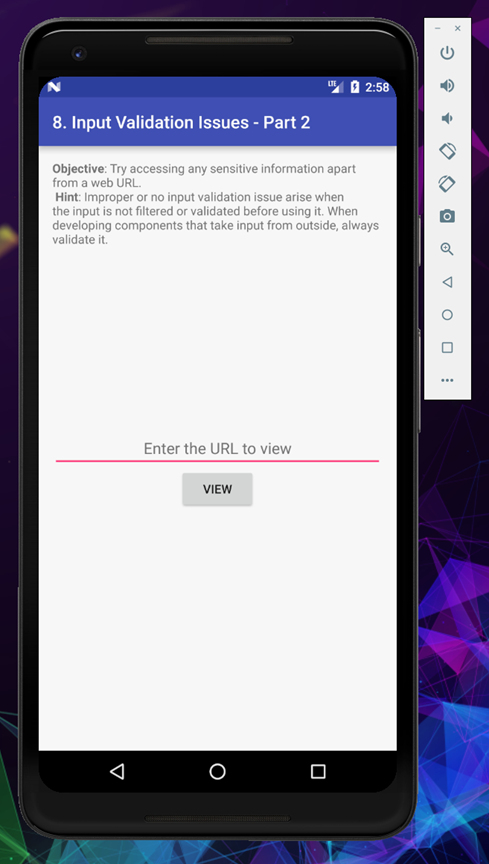
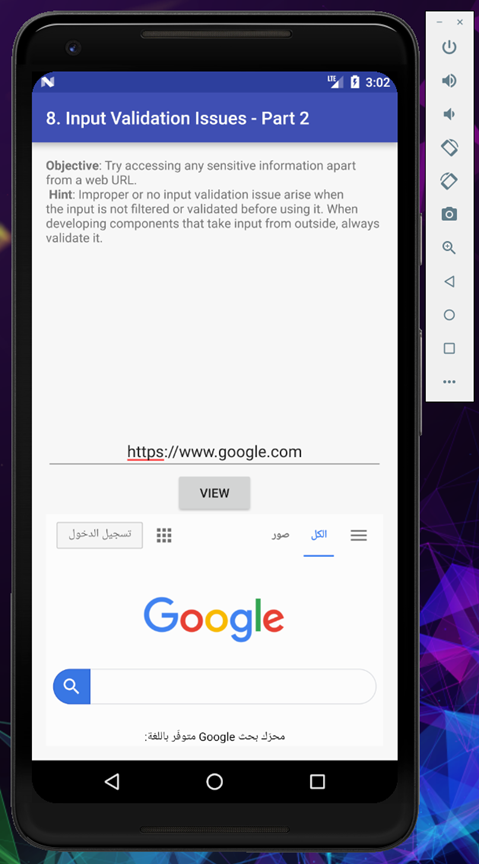
As you can see the application open the webpage inside the application frame.
Let’s see if could read internal device files through application or not?
Let’s start with something basic, create a new file and try to read it from application itself
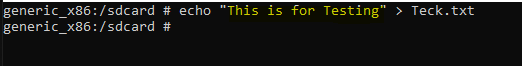
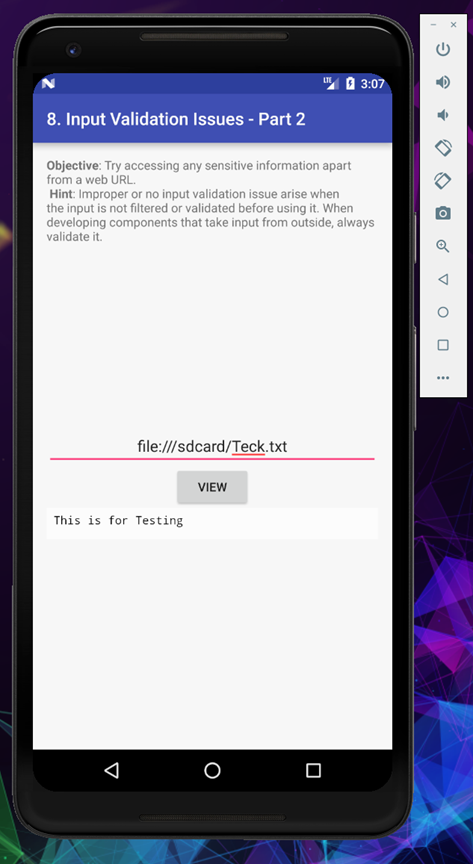
It’s working fine, let’s try to read some confidential file which we found in our earlier challenges
[ file:///data/data/jakhar.aseem.diva/shared_prefs/jakhar.aseem.diva_preferences.xml ]
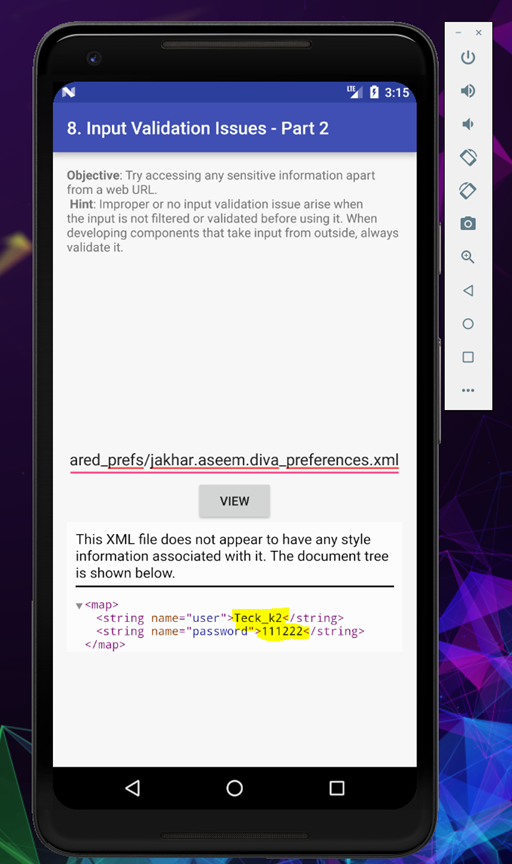
As you can see we can view the XML file which store our credential from the challenge 3 which we solved earlier.
Now let’s have the source code of the application which is the reason for this vulnerability
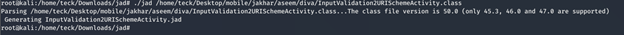
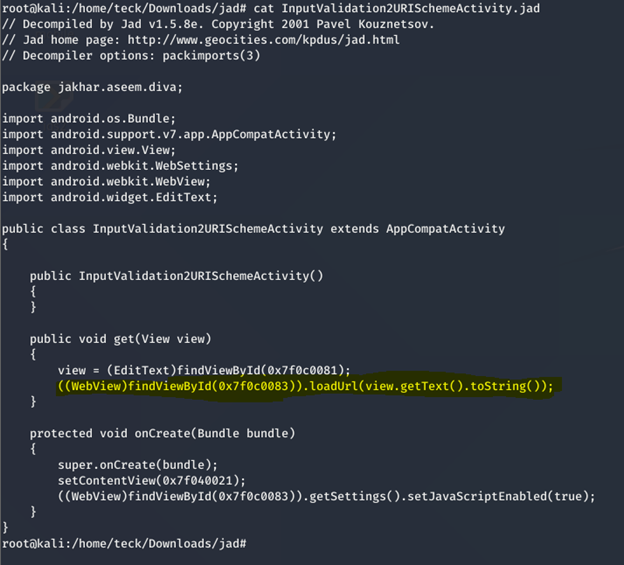
This piece of code allow to read any URL even the system internal files, without validating or sanitizing it properly and as the application have permission to read any file in the system, because of which we were able to easily read any file even on SDcard.
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments