Our next challange is abourt Input Validation Issues
Input validation attack happens when the application could not sanitize the user input properly, and which could lead to data information leak, one of the simplest example of this is SQLi and XSS.
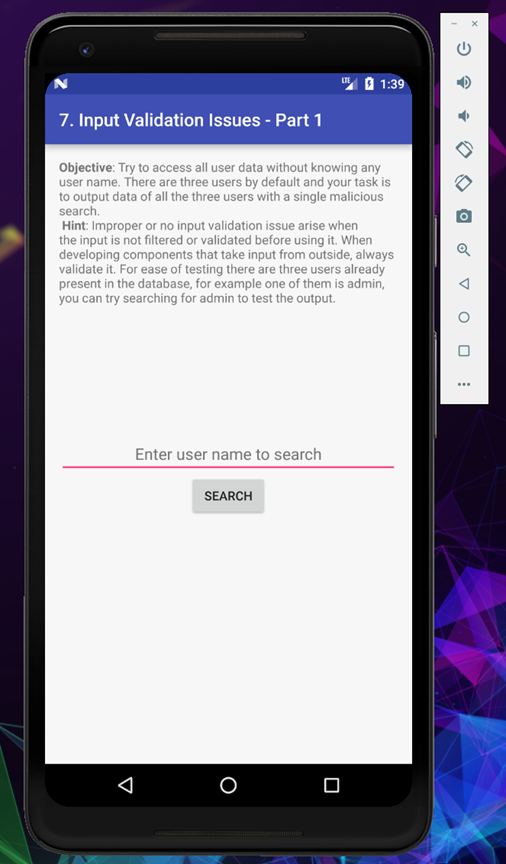
So in this challenge there are 3 default users, and if we could find any of them, we can see the secret data, so let’s start
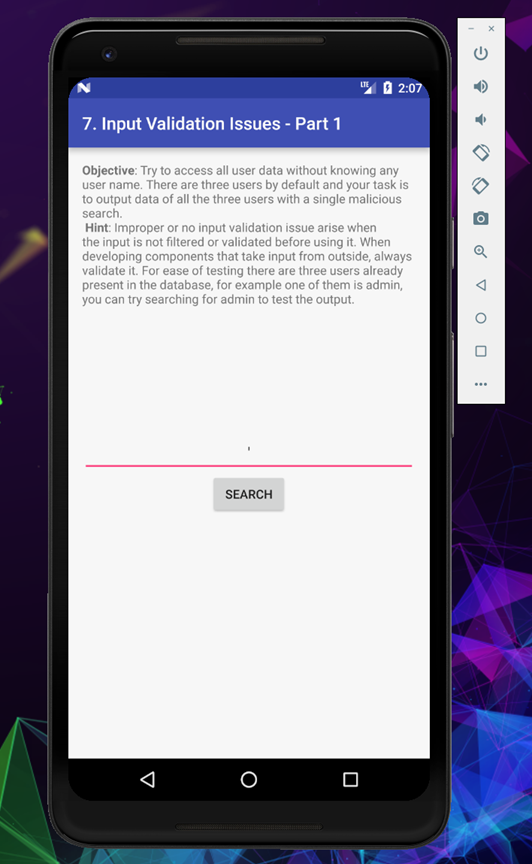
First I tried with a single quote (‘) and looked at Logcat to see the error
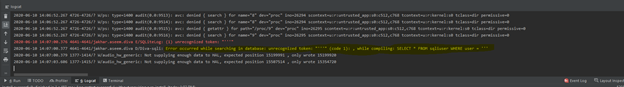
We can see a sql error, which means we are on the right path as it’s using dynamic queries to retrieve data from the database, and as usual a single quote created an error in the query
Now let’s try with two and three quotes and see the response in the Logcat
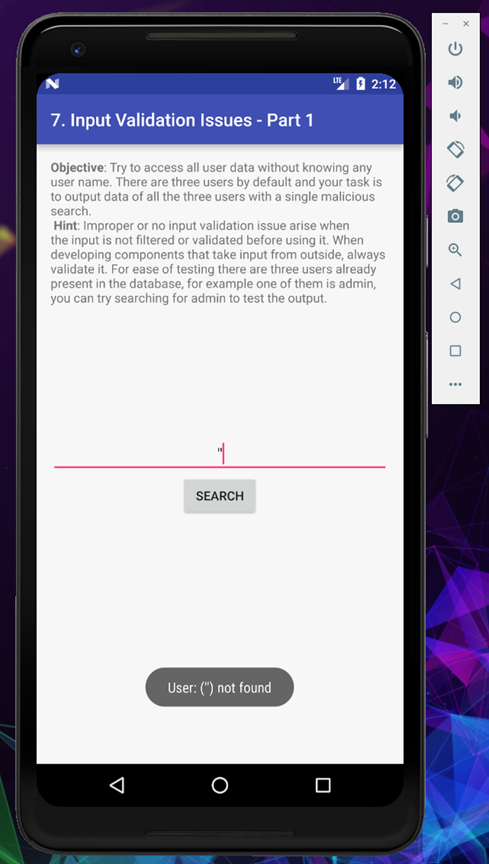
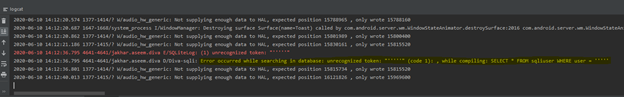
Perfetto, now have verified that odd number of single quotes are causing sql errors, now let’s try to retrieve the username from the database
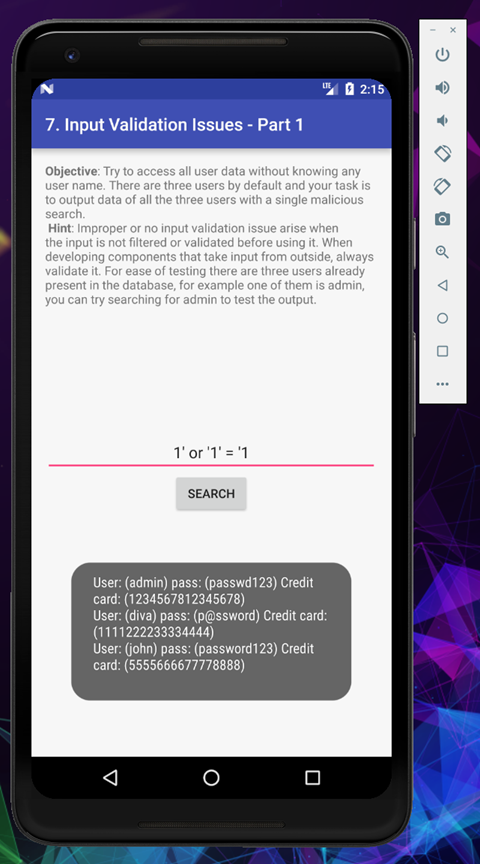
With a simple true statement we can extract the stored credentials from the database
Now, let’s have a look in the source code which is the reason behind this vulnerability.
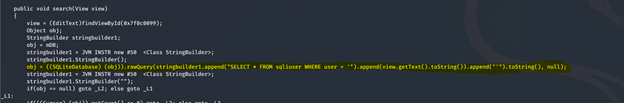
This line of code allow the user to retrieve the data from sql query.
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments