This challenge is the second part of Hardcoding issues, where the objective is to find sensitive information which is the vendor code left by developer inside the application source code.
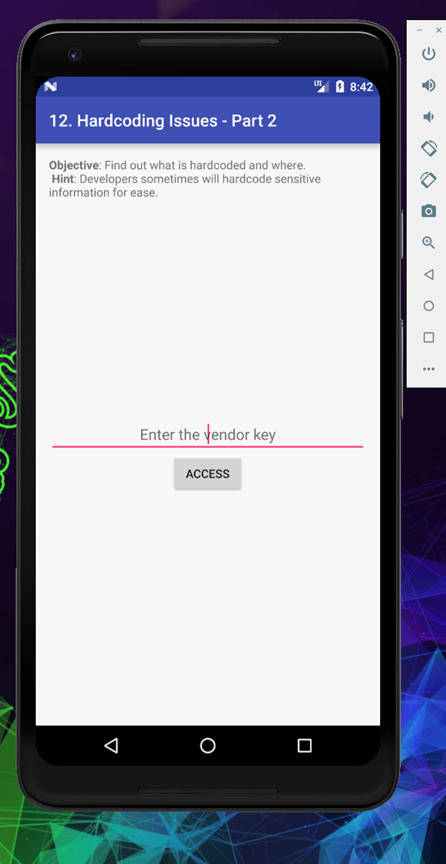
Let’s have a look inside source code
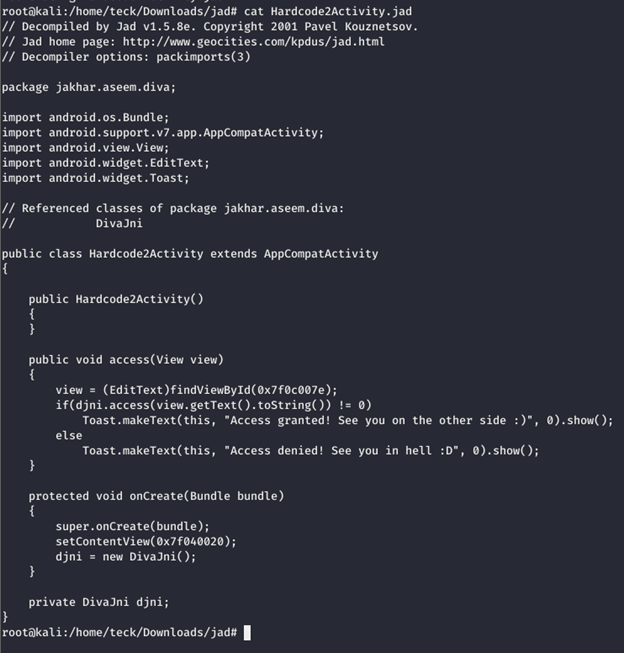
After analyzing the code above, we can understand that the activity is creating another class with the name of DivaJni, let’s have a look at that.
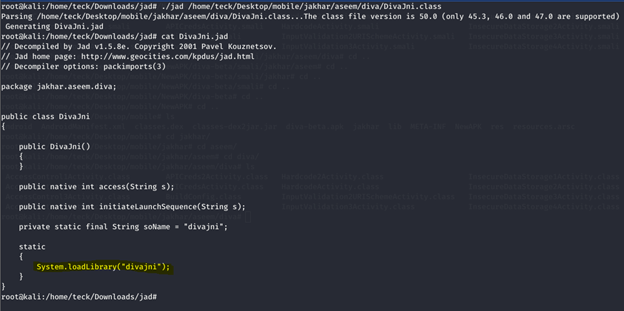
After analyzing the code above we could understand that there is a native library with the same name divajni, if you unzip the APK you will see the lib folder, which contains all the libraries inside it, let’s have a look
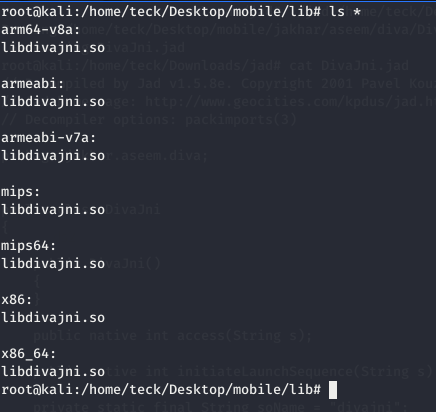
Let’s open any of the library and analyze it
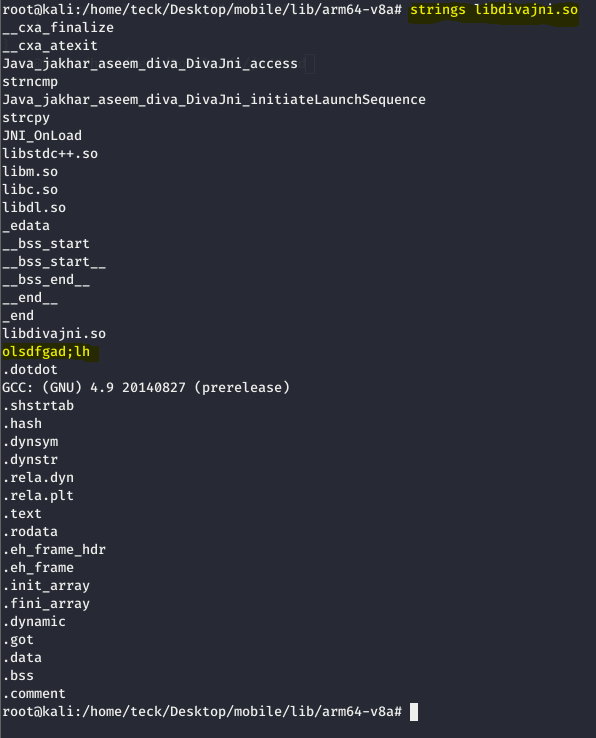
After trying couple of strings, I finally found the correct string which can give us access [olsdfgad;lh]
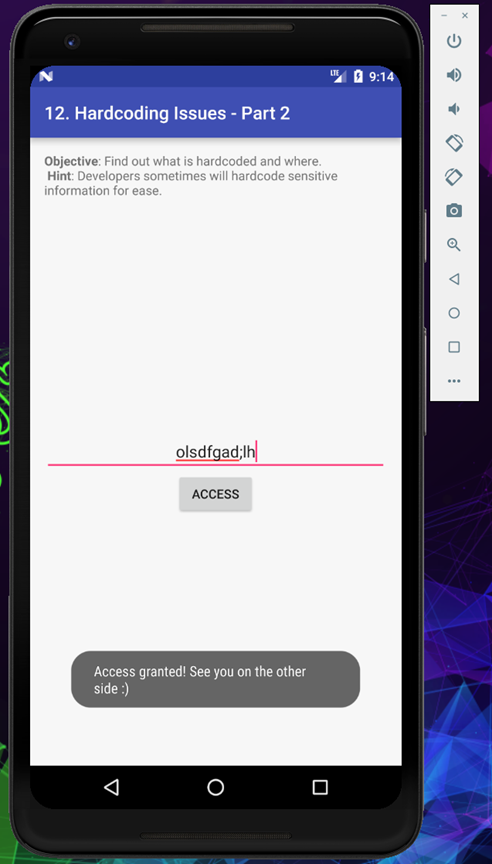
Finally we found the correct key, see you in the last challenge.
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments