Now we have reached to the last challenge of our Access Control Issues
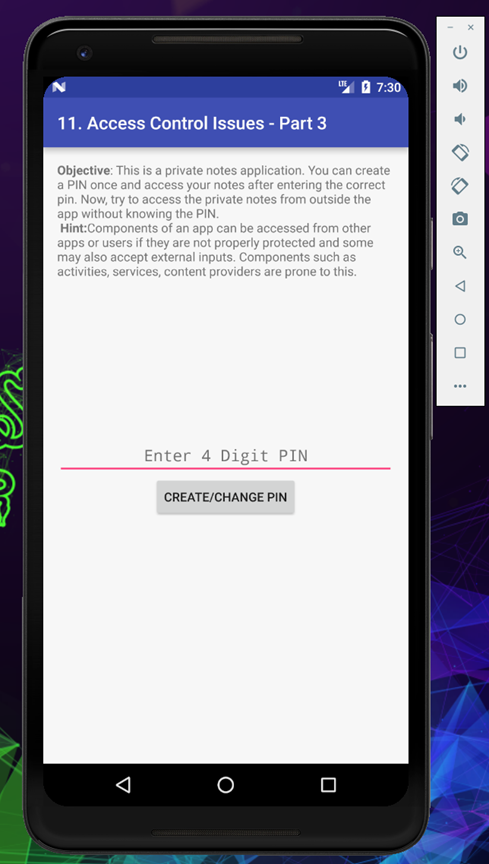
The application is meant to save notes, but before accessing the notes we need to create a 4 digit pin, once we do that we can access the notes, but the objective of this challenge is to view the notes without entering the pin, let’s have a look in the application and then we will analyze AndroidManifest.xml
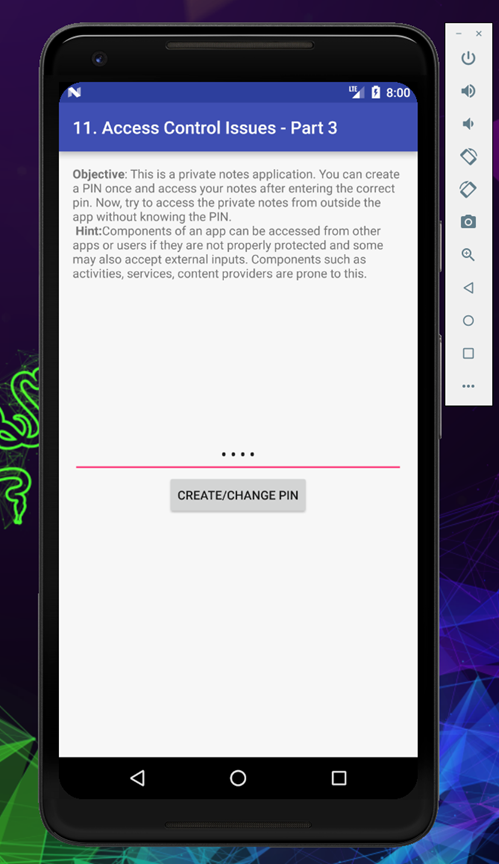
Put your 4 digit pin and click on create/change pin
Once you create a pin, you will able to see a new option to go to private notes
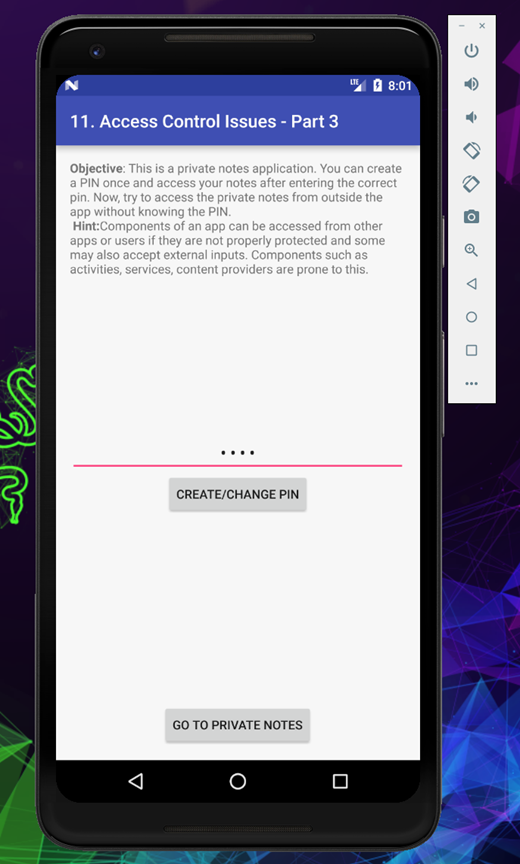
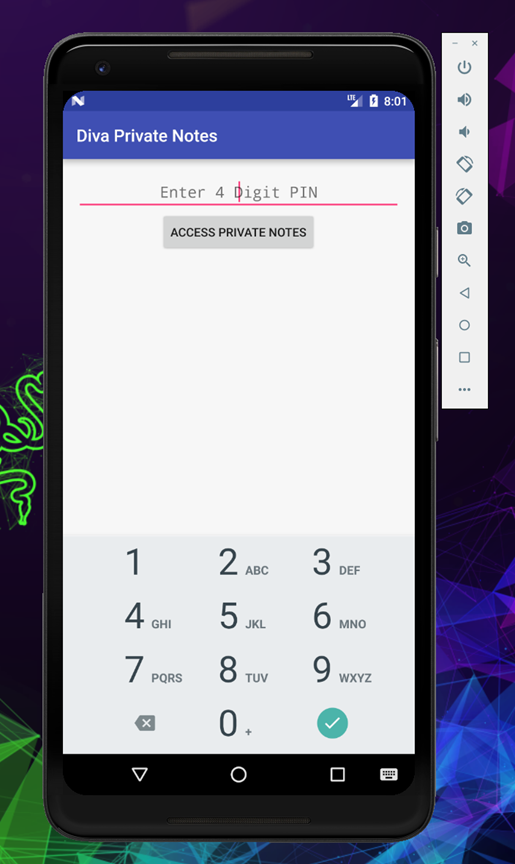
It will again ask you to enter your pin
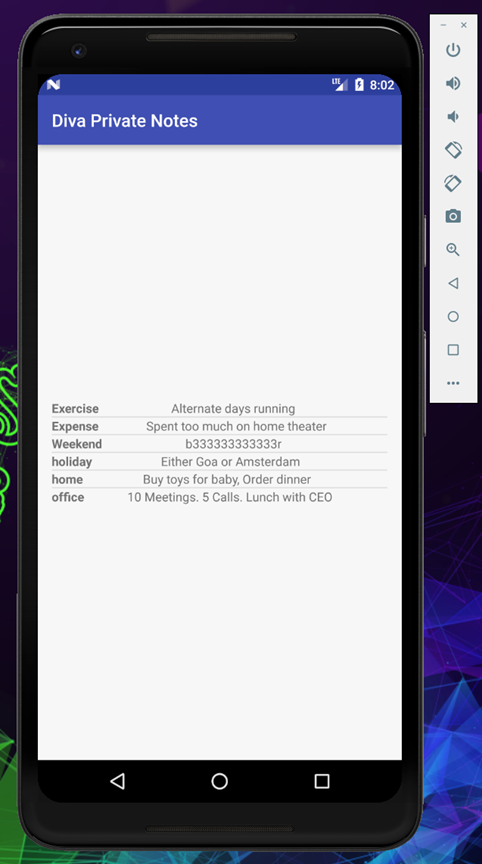
Once you enter the correct pin, you will be able to see the private notes
Now let’s have a look at AndroidManifest.xml to find the vulnerable piece of code.
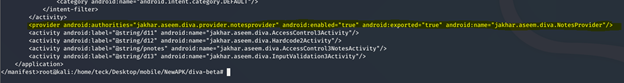
If you focus on the above highlighted line, it shows the content provider is set to [android:enabled:”true”]
Generally the content provider is represented like [content://] let’s have a look inside smali code and find the correct URI
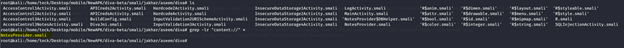
If we try to find the content:// from all the file, we found the following inside the NotesProvider.smali, let’s open and have a look inside
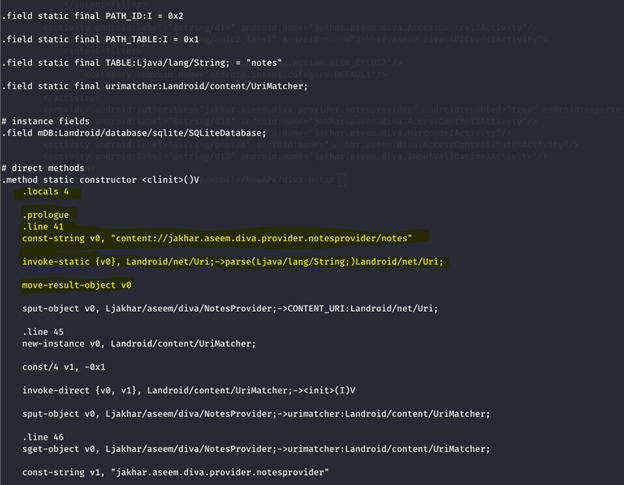
As you can see in the above URI it provide us the exact URI path
[content://jakhar.aseem.diva.provider.notesprovider/notes]
If you remember few steps above we found that the content provider can we queried without any permission, let’s try to open it from adb shell
[adb shell content query –uri content://jakhar.aseem.diva.provider.notesprovider/notes]
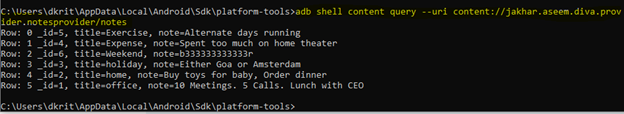
As you can see we can view all the private notes from the application without providing any pin.
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments