Last week I was assigned a project for a Very Big Organization to do a Internal PT, and it was a gray box pentesting, The main objective was to bypass their newly installed Cisco ISE, So I decided to share my experience with you. Let's start from scratch.
What is CISCO ISE?
Cisco (ISE) – Cisco Identity Services Engine (Cisco ISE) is a next generation identity and access control policy platform that enables enterprises to enforce compliance, enhance infrastructure security, and streamline their service operation.
What is NAC?
Network Access Control or NAC is a solution to prevent unauthorized access to internal networks. It restricts access to the network based on identity or security posture of the device that is trying to connect.
How NAC works?
When a tool connects to the community, the NAC depends on a number of detection methods to detect the units’ presence. They are listed under:
DHCP Proxy – a NAC resolution intercepts DHCP requests for community configuration info coming from components working on the community disclosing their presence.
Broadcast Listener – a NAC resolution listens to broadcast community visitors, corresponding to ARP requests, DHCP requests, and so forth., generated by components working on the community disclosing their presence.
Listening to (sniffing) IP visitors – IP packets passing by way of a sure monitoring location disclosing a sure ingredient is linked to the community.
Client-Based Software – some NAC options make use of client-based software program as a part of the answer structure, which is used to carry out endpoint security assessment to forestall a component from acquiring community configuration info till it’s evaluated and to inform a centralized administration console the ingredient is on the community.
SNMP Traps – some switches might be configured to ship an SNMP entice when a brand new MAC deal with is registered with a sure swap port. The SNMP entice info particulars the MAC deal with and the community interface on which it was registered.
Most of the NAC solutions available today use only one of the detection techniques. Detecting various devices on the network is one of the key elements of the NAC and if the NAC is incorrectly configured and if it fails at detecting a device connecting to the network, the NAC solution can be bypassed.
The scenario of the attack and how I bypassed NAC
As you know it was a Gray box Pentesting I have only physical access to the target organization and had no prior knowledge of the network/infrastructure or subnet ranges nor had my device whitelisted on the network.
As every penetration test starts, my first step begins with information gathering. I had nothing but a VoIP phone next to me of an employee who was on leave. I started to look at the settings, and I got the following details:
* Call Manager TFTP server IP address
* DHCP server IP
* Default gateway
* MAC Address of VoIP phone, etc
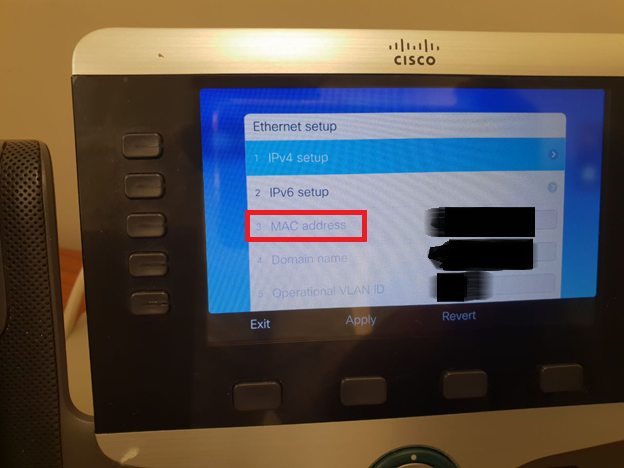

I thought to myself, based on what do VoIP phones or network printers get connected on the network. Since VoIP phones and network printers are non dot1x authentication capable devices, they, therefore, cannot have an updated AV signature list and so on. They will definitely need to be whitelisted based on MAC as there is no mechanism for the NAC to assess these kinds of devices. If I spoofed the MAC address, then I should be seen as that VoIP phone by the NAC.
Dot1x is a part of the IEEE 802.1 group of protocols. It provides an authentication mechanism to devices wishing to attach to LAN or WAN. IEEE 802.1X defines the encapsulation of the Extensible Authentication Protocol (EAP) over IEEE 802, which is known as “EAP over LAN” or EAPOL.
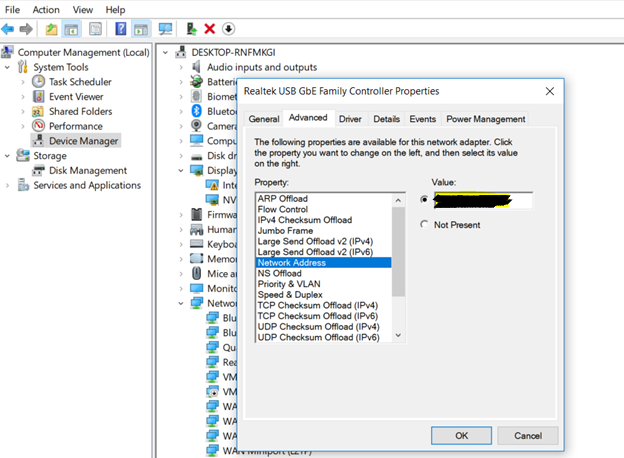
Getting back to action, I spoofed the MAC address of the VoIP phone on my Windows system to see if my theory worked and found that I was correct. I could access the Voice VLAN IPs and also was able to reach the Server VLAN subnet ranges. This was one of the best NAC solutions around, and I was surprised it could not detect my device as a Windows system.
Boom I am in the network, I got the IP address from DHCP Server and able to ping available machines in the network and also able to scan ports and do other nasty things.
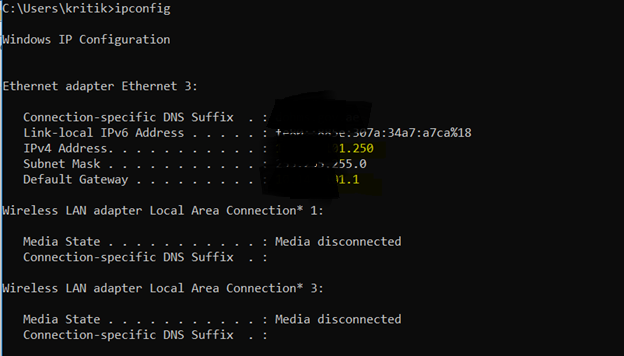
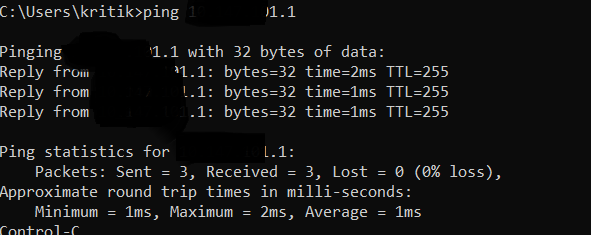
If you remember I found the TFTP domain name earlier in the settings of VoIP phone, I extracted the IP and found, The network was straightly connecting me to their main office network without any restriction, and there I enumerated other subdomain and some interesting Servers.
Mitigations to reduce the effectiveness of a Cisco ISE(NAC) bypass.
My first step towards gaining access to the network was to gather information from the VoIP phone lying around. Users normally do not need access to such information. Hence access to the network configuration on VoIP phones should be locked down. Also, by default, there is a web service running that gives unauthenticated access to the Cisco VoIP phones’ network configuration. This too should not be available.
What if an attacker still manages to get access to the network by spoofing the MAC address of a printer? The best practice is to segregate Voice VLAN and Server VLAN. In my case, the organization failed to restrict traffic internally between the two VLANS hence I was able to reach the Server VLAN. The network was completely flat. It stresses the importance of having a firewall in the core layer of the network so as to segregate and restrict traffic going from one VLAN to another.
Vendors could possibly ping the newly connected device on the network. The TTL response could be a good indicator of the host and operating system.
In short, the following mitigations are recommended:
* Lock down access to view network configuration on VoIP phones.
* In case an attacker manages to bypass the NAC; a core firewall in the network will help that restricts traffic from Voice VLAN to Data VLAN. Not all traffic should be trusted from Voice VLAN.
* Disable the web service on VoIP phones to further restrict users to view network configuration.
* There should be a mechanism by the NAC vendors that pings the devices to determine the kind of host that is connected (this technique may be around but may not be known to the NAC administrators).
Cisco also has enhanced their profiling capability citing MAC spoof issue. The details can be found on the below link:
https://www.cisco.com/c/en/us/support/docs/security/
Twitter / Hack The Box / CTF Team / Teck_N00bs Community Telegram
Comments